Image encryption method based on Hash function and inserting-deleting model
A technology of hash function and encryption method, which is applied in image data processing, image data processing, instruments, etc., to achieve the effect of improving stability, high storage density, and improving encryption efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0045] In order to further understand the image encryption method based on the hash function and the insertion-deletion model, the present invention will be further described below in conjunction with the accompanying drawings.
[0046] The detailed steps are as follows:
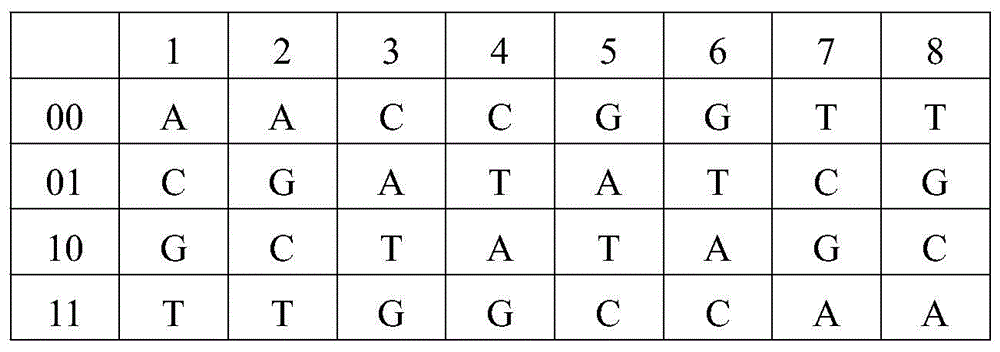
[0047] S1, the original image (see attached image 3 ) into matrix A(m,n), and then get hash table B and hash matrix C(m,n) through hash function H(key)=keymod3, where key is the pixel value of the original image, and hash table The size of is determined by the key.
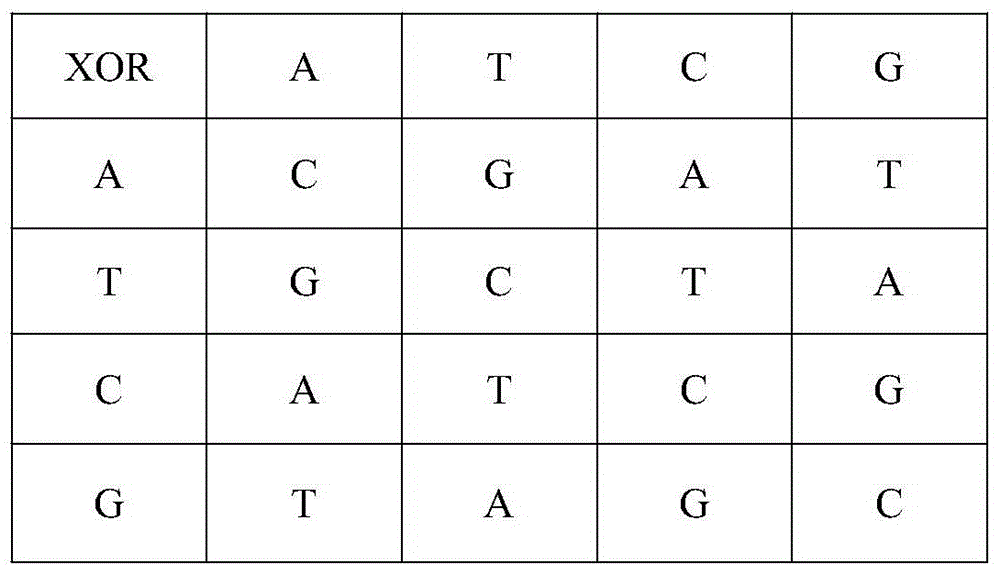
[0048] S2. Use the hash table B and the hash matrix C to scramble the pixel values of the image
[0049] count1=count2=count3=size(C,2),
[0050] When C(i,j)=0, if B(1,count1)≠0, then D(i,j)=B(1,count1), count1=count1-1;
[0051] When C(i,j)=1, if B(2,count2)≠0, then D(i,j)=B(2,count2), count2=count2-1;
[0052] When C(i,j)=2, if B(3,count3)≠0, then D(i,j)=B(3,count3), count3=count3-1;
[0053] where D(m,n) is the scrambled matrix.
[...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com