Device for realizing network security management based on virtualization and management method
A network security and virtual network technology, applied in electrical components, transmission systems, etc., can solve the problems of reducing virtual machine network security access and management capabilities, low network security protection capabilities, poor network security and stability, etc., to improve network security. The effect of efficient operation, improved network security capabilities, and improved operability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
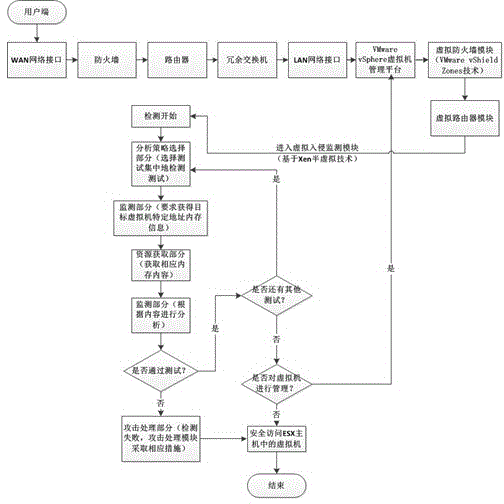
[0026] Example 1: figure 2 A flow of a method for implementing network security management based on virtualization is shown:
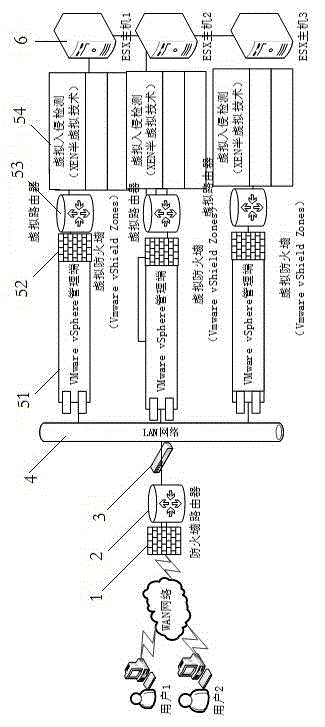
[0027] 1) First of all, after WAN users enter the LAN network, they first isolate the virtual machine through the virtual firewall module (VMwarevShieldZones), provide control area, external network and parameter protection, etc., and protect access rights, malicious information and malicious information through the drivermodel Third-party programs perform filtering and interception settings.
[0028] 2) Secondly, assign routes through the virtual router module to point to virtual machines that request access to different resources, that is, set the routes to different bridging methods in VMware vSphere according to actual needs, and establish virtual routes.
[0029] 3) Finally, the access is monitored in real time through the virtual intrusion monitoring module based on Xen paravirtualization technology. The process flow is: after the monitoring i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com