Information security protection monitoring method of LED asynchronous control card
An asynchronous control card and security monitoring technology, which is applied to the usage of multiple keys/algorithms, secure communication devices, public keys for secure communication, etc., to achieve the effect of improving security, ensuring integrity and confidentiality
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] Below in conjunction with accompanying drawing, the scheme of the present invention is described in detail
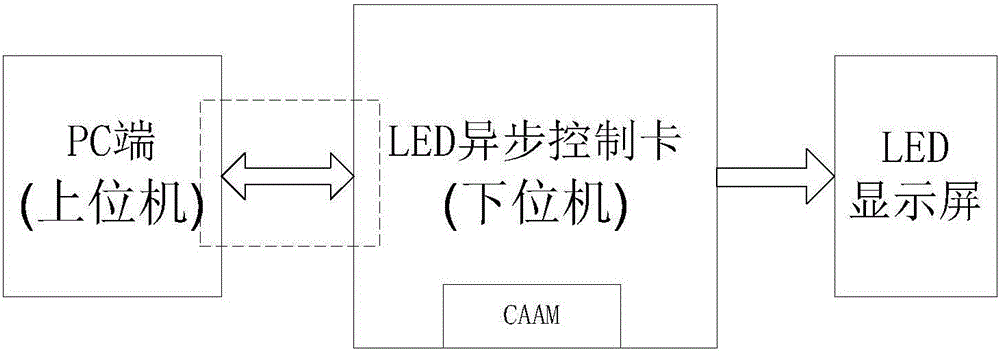
[0035] Such as figure 1 , the information security monitoring method of the LED asynchronous control card provided in this embodiment mainly solves the security problem of data transmission between the upper computer and the lower computer, ie, the LED asynchronous control card. Specifically, the connection interface between the upper computer and the LED asynchronous control card is a Gigabit Ethernet interface, and the connection methods include: direct connection with a wired network cable, local area network connection such as wireless network WiFi connection; wide area network connection such as internet connection.
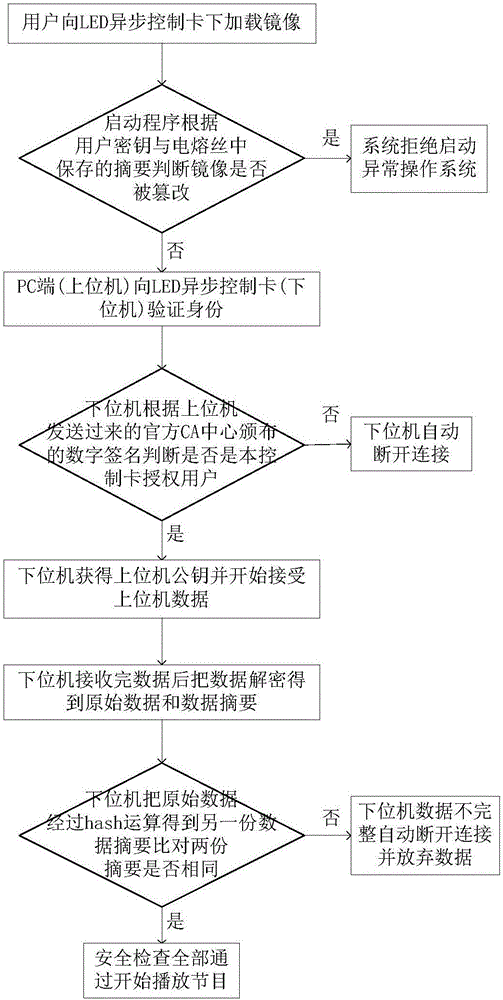
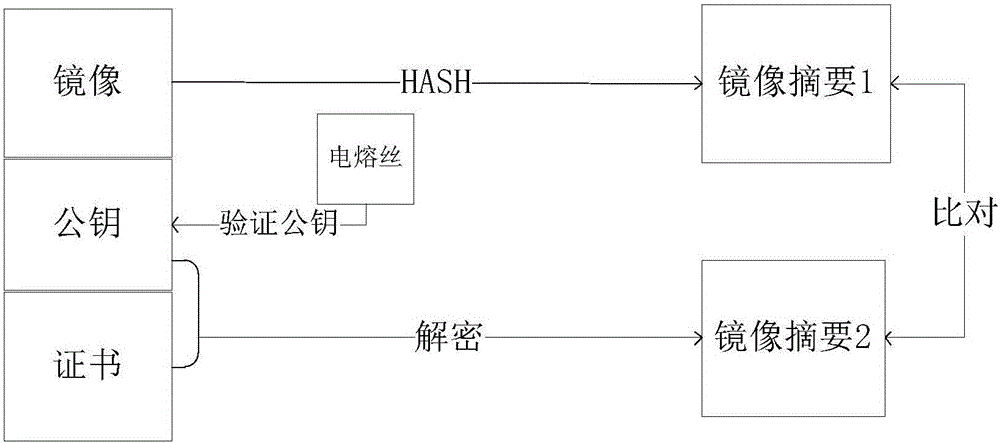
[0036] At present, the password-based identity authentication method is the most widely used, and it is also the simplest authentication technology. Its advantages lie in the simplicity of implementation, low cost, and high speed. However, ther...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com