Encrypted embedded video chaotic secret communication method after H.264 coding
A post-encoding encryption and secure communication technology, which is applied in the field of embedded video chaotic secure communication, can solve problems such as insufficient security and efficiency, difficult design, and reduced encoding compression rate, so as to improve real-time performance, security, and real-time performance And the effect of high security and increasing the unique solution distance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
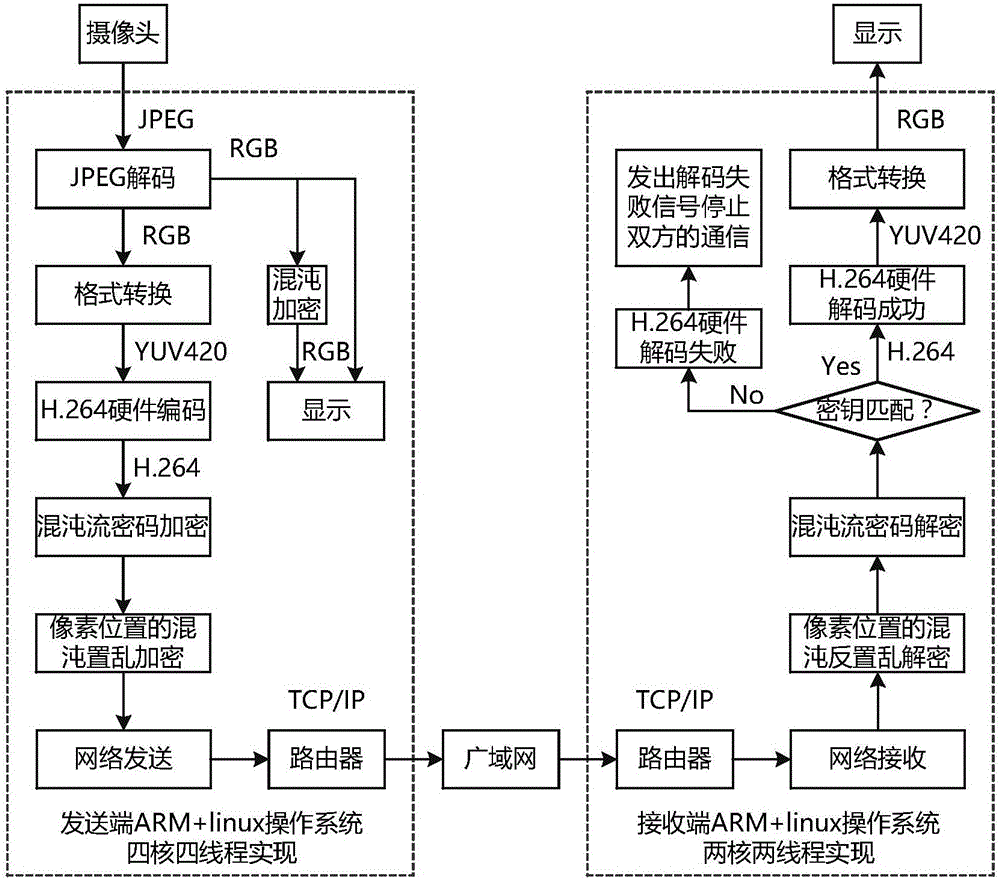
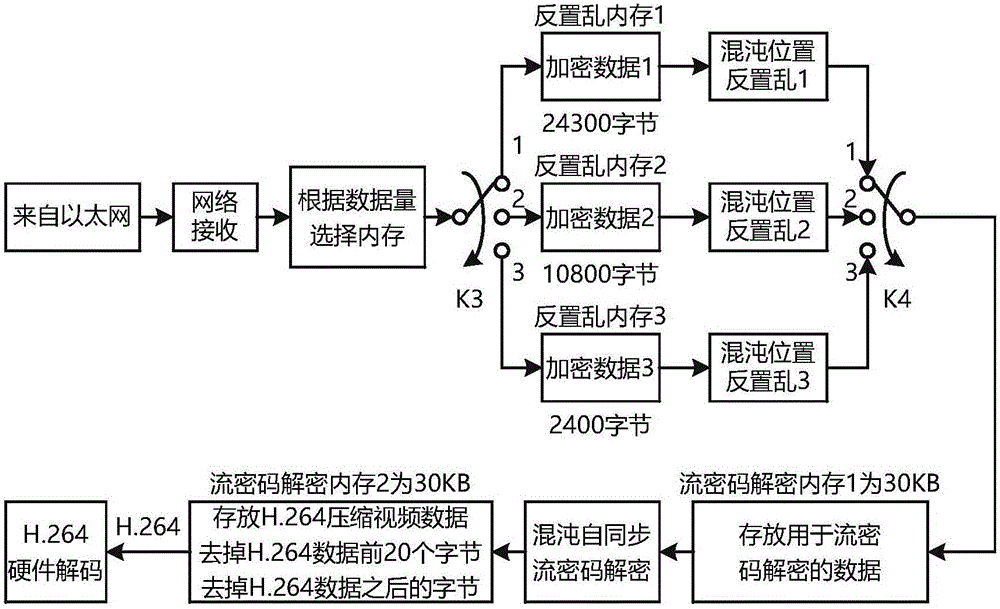
[0044] see figure 1 , the method of the present invention comprises the following steps: camera captures video, JPEG decoding of video image, RGB format to YUV420 format conversion, H.264 hardware encoding, chaotic stream cipher encryption, chaotic scrambling encryption of pixel position, network transmission, wide area network transmission , network reception, chaotic anti-scrambling decryption of pixel positions, chaotic stream cipher decryption, successful decoding of H.264 hardware under key matching conditions, conversion from YUV420 format to RGB format, decrypted video display, key mismatch conditions After the H.264 hardware decoding fails, the communication between the sending end and the receiving end stops, and the original video signal cannot be decrypted.
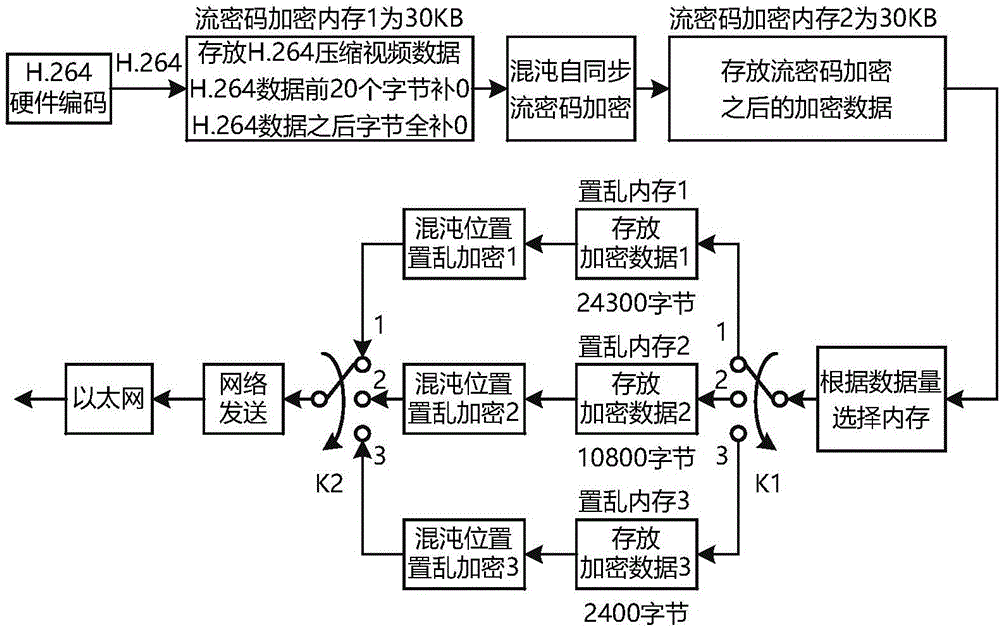
[0045] 1. At the sending end, the operation mode of four cores and four threads is adopted, and the sequence of H.264 hardware encoding and chaotic encryption is followed. The specific operation steps at the s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com