A way to order anonymously
A client-side and server-side technology, applied in the fields of anonymous authentication, signature technology and ordering technology, can solve problems such as time-consuming, impractical payment methods, and large storage capacity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
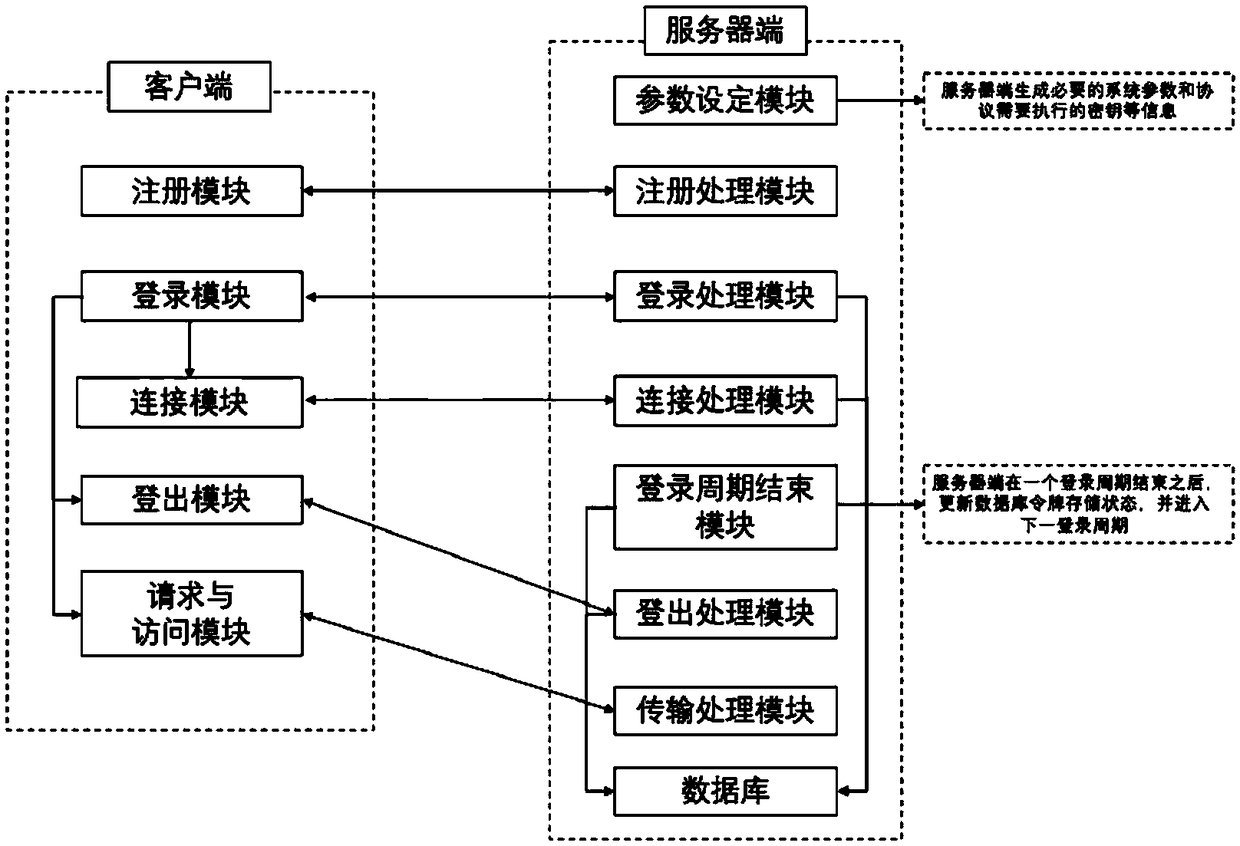
[0071] The database type in this embodiment uses redis to store tokens; before implementing the registration process, the server needs to execute the parameter setting module, mainly to generate necessary system parameters and its public key and private key, corresponding to the steps in the main body of the manual One, the specific steps are:
[0072] Step 1.1 generate security parameters t=80, l=40, s=40; generate n, n=pq is a large composite number, p and q are large prime numbers, |n|=100; generate n > refers to the n The resulting multiplicative group;
[0073] Step 1.2 Select Set X = g x ,Y=g y , Set public key and private key: spk=(q,G,G T ,g,X,Y,Z 1 ,Z 2 ), ssk=(x,y,z 1 ,z 2 ), wherein G is an elliptic curve group, in the present embodiment 1, the elliptic curve is y 2 =x 3 +1modp, q is the order of the elliptic curve, g is a generator of the elliptic curve, G T is a bilinear mapping group on the elliptic curve, expressed as e:G×G→G T , and g T =e(g...
Embodiment 2
[0095] This embodiment is based on the login process of an anonymous ordering system on which the present invention is based, specifically taking access to video services as an example.
[0096] After successful registration, the user can log in to the client to access the video service to watch videos. The user logs in through the client login module and interacts with the server login processing module. The specific steps are:
[0097] Step (3.1) The client uses sk=(s=(a, A 1 ,A 2 ,b,B 1 ,B 2 ,c),d,exp s , exp e ) to generate a blind signature, select t is the start time of the current login period; at the same time, this embodiment uses the difference between the current time and the time at 0:00 on January 1, 1970, and converts it into minutes; the client login module generates and Y d (t), where Y d (t) is a token, which is generated using the PRF method and sent to the server;
[0098] Step (3.2) The server-side login processing module judges the token Y d ...
Embodiment 3
[0118] This embodiment is based on the connection process of an anonymous ordering system of the present invention.
[0119] When the user is in the login state, the connection operation can be performed. The connection operation is mainly an optional operation provided to the user. When de-association is not required, the user can choose the connection between the current cycle and the next cycle, so that after the next cycle arrives , the user does not need to log in again; the connection operation is performed through the connection module of the client, and interacts with the connection processing module of the server, mainly through the user maintaining a variable linkn in the connection module of the client, linkn indicates the current login period after the connection starts Linkn cycles, every time a cycle ends, linkn will be decremented by 1, and linkn will be reduced to 0 to indicate that there will be no connection in the future, and linkn can be modified in any logi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com