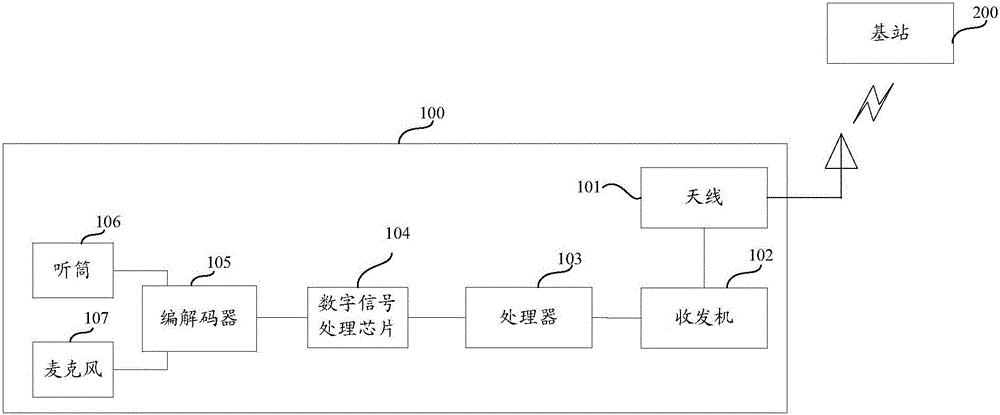
Identification method for pseudo base station and terminal
An identification method and pseudo base station technology, applied in electrical components, wireless communication, security devices, etc., can solve the problems of reducing the flexibility and applicability of terminal identification of pseudo base stations, the single method of terminal identification of pseudo base stations, and the single authentication method
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
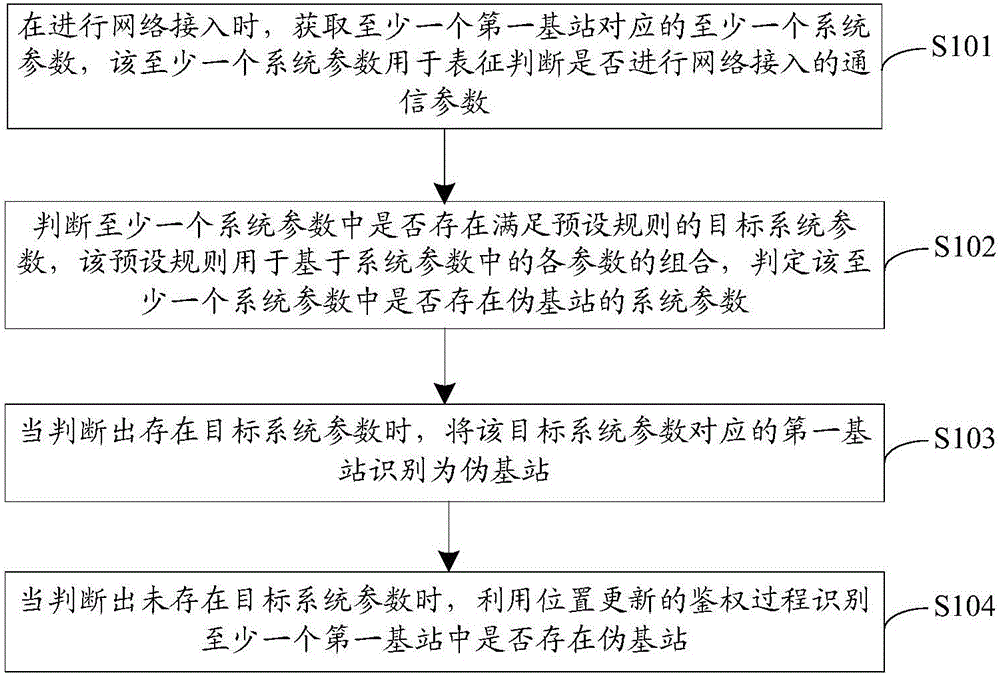
[0079] An embodiment of the present invention provides a method for identifying a pseudo base station, such as figure 2 As shown, the method may include:
[0080] S101. When performing network access, acquire at least one system parameter corresponding to at least one first base station, where the at least one system parameter is used to represent a communication parameter for judging whether to perform network access.
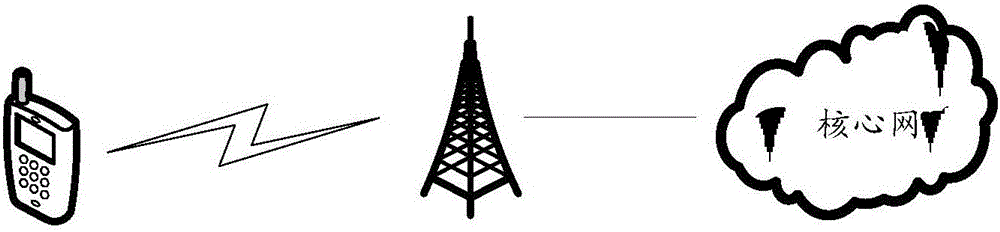
[0081] It should be noted that, based on image 3 In the communication architecture shown, the terminal can communicate with the base station. When the terminal selects or reselects a cell, the terminal can search for available network frequency points from the core network through the base station, obtain available network frequency point information and notify the The terminal selects a frequency point with a strong signal from the network frequency point information to access, so as to realize network communication. The method for identifying a pseudo-ba...
Embodiment 2
[0122] An embodiment of the present invention provides a method for identifying a pseudo base station, such as Figure 5 As shown, the method may include:
[0123] S201. Acquire at least one system message broadcast by at least one base station during network access.
[0124] S202. Parse at least one system parameter from at least one system message, and the at least one system parameter is used to characterize the communication parameters for judging whether to perform network access, where each system parameter includes: the number of blocks reserved for access permission, public control Channel configuration parameters, location update cycle, cell minimum access level value and cell reselection bias parameters.
[0125] It should be noted that, based on image 3 In the communication architecture shown, the terminal can communicate with the base station. When the terminal selects or reselects a cell, the terminal can search for available network frequency points from the c...
Embodiment 3
[0178] Such as Figure 6 As shown, the embodiment of the present invention provides a terminal 1, the terminal 1 may include:
[0179] The obtaining unit 10 is configured to obtain at least one system parameter corresponding to at least one first base station when performing network access, and the at least one system parameter is used to represent a communication parameter for judging whether to perform network access.
[0180] A judging unit 11, configured to judge whether there is a target system parameter that satisfies a preset rule among the at least one system parameter acquired by the acquiring unit 10, and the preset rule is used to determine based on a combination of parameters in the system parameters Whether there is a system parameter of a pseudo base station in the at least one system parameter.
[0181] An identifying unit 12, configured to identify the first base station corresponding to the target system parameter as a pseudo base station when the judging uni...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com