Cross-tenant access control method based on trust model in cloud environment
A trust model and access control technology, applied in the field of cloud computing information security, can solve the problems of cloud resources losing security control and inapplicability, and achieve the effect of good promotion and use value, simple structure and reasonable design
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
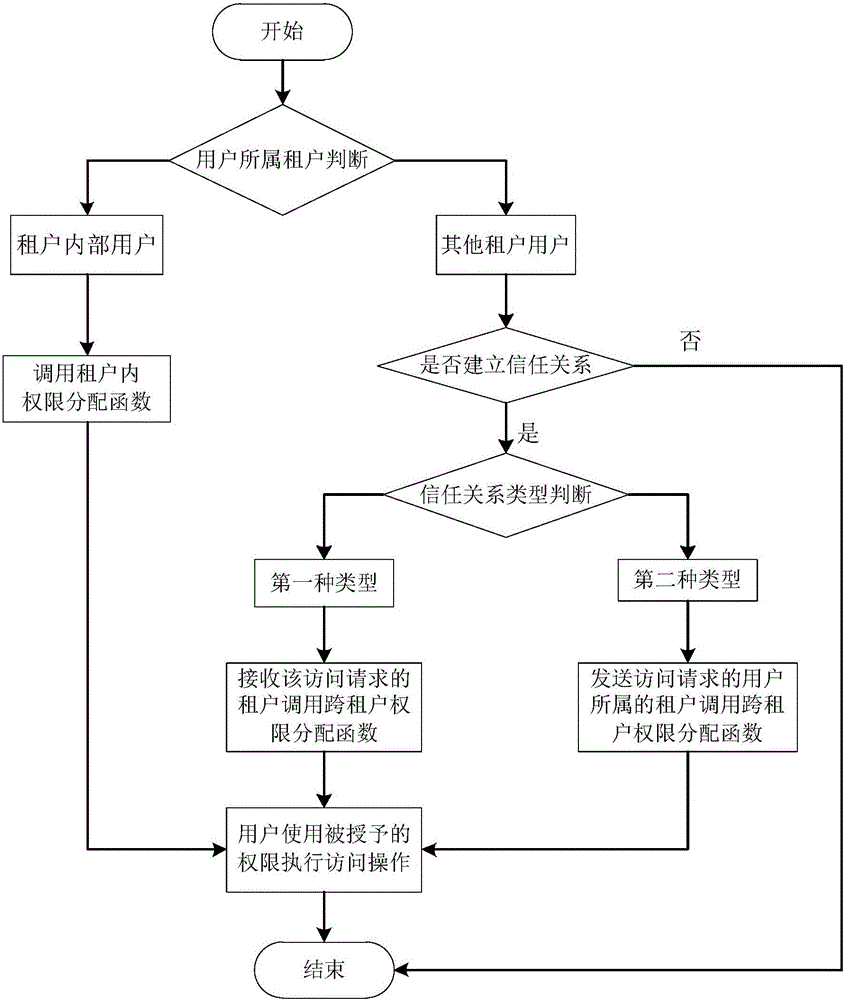
[0061] (1) Tenant registration
[0062] Enterprise tenants plan to use the tenant trust relationship management services provided by cloud service providers. First, the enterprise tenant applies to the cloud service provider through the registration process, and registers the tenant information, including company name, address, phone number, etc.; then provides the tenant administrator information (this administrator will be used later to create tenant internal users and assign permissions), Select the specific functional modules of the trust relationship management service, such as application, permission, and revocation.
[0063] (2) Internal access control modeling
[0064] Tenant administrators can choose one of the three access control types (discretionary access control, mandatory access control, and role-based access control) provided by cloud service providers to complete tenant internal access control modeling.
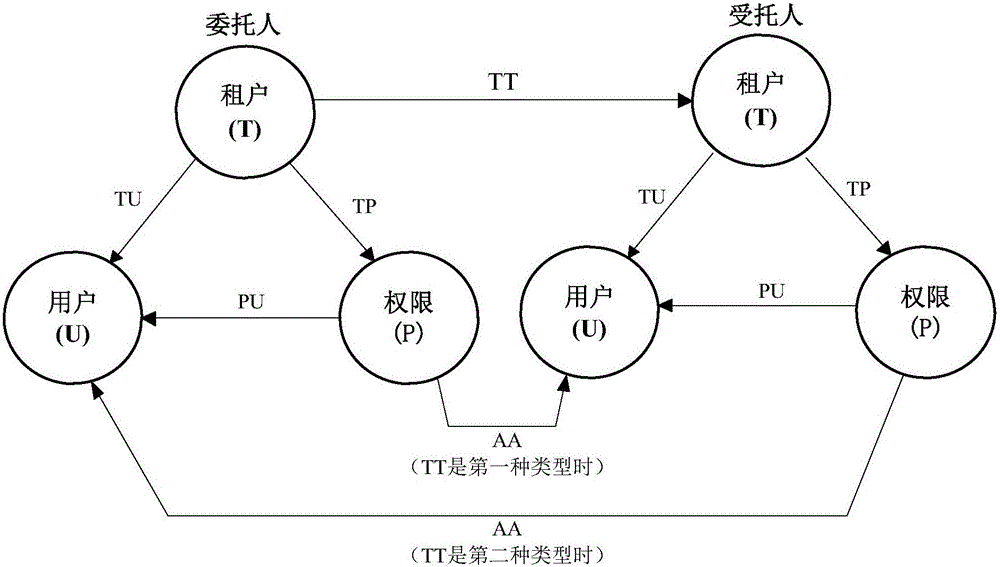
[0065] (3) Cross-tenant access control modeling
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com