File reinforcement method and device
A technology for strengthening devices and files, applied in computer security devices, instruments, computing, etc., can solve problems such as harming users, defrauding users, defrauding users for installation, etc., and achieves the effect of preventing reverse and protecting security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0029] refer to figure 1 , shows a flow chart of steps of a file hardening method according to an embodiment of the present invention.
[0030] Step 102, converting the target function in the target executable file in advance and registering it in the library file.
[0031] Taking the Android system as an example, the APK (Android Package, Android installation package) includes the dex (DalvikVM executes) file, which is the Android Dalvik execution program, that is, the type of executable file on the Android platform, and the suffix is .dex. If the execution process of the dex file, such as functions, is reversed, it will affect the security of the corresponding application and system. Therefore, the embodiment of the present invention proposes a reinforcement method for dex files, so as to prevent the dex files from being reversed and protect the security of files, applications and systems.
[0032] For the target executable file such as the target function in the dex fil...
Embodiment 2
[0040] The embodiment of the present invention can be applied to the Android system. Taking the reinforcement and protection of the dex file as an example, it is assumed that the library file is an so file, the target function is an OnCreate function, and the local function is a native function. The steps and flow of the file hardening method are discussed in conjunction with this example.
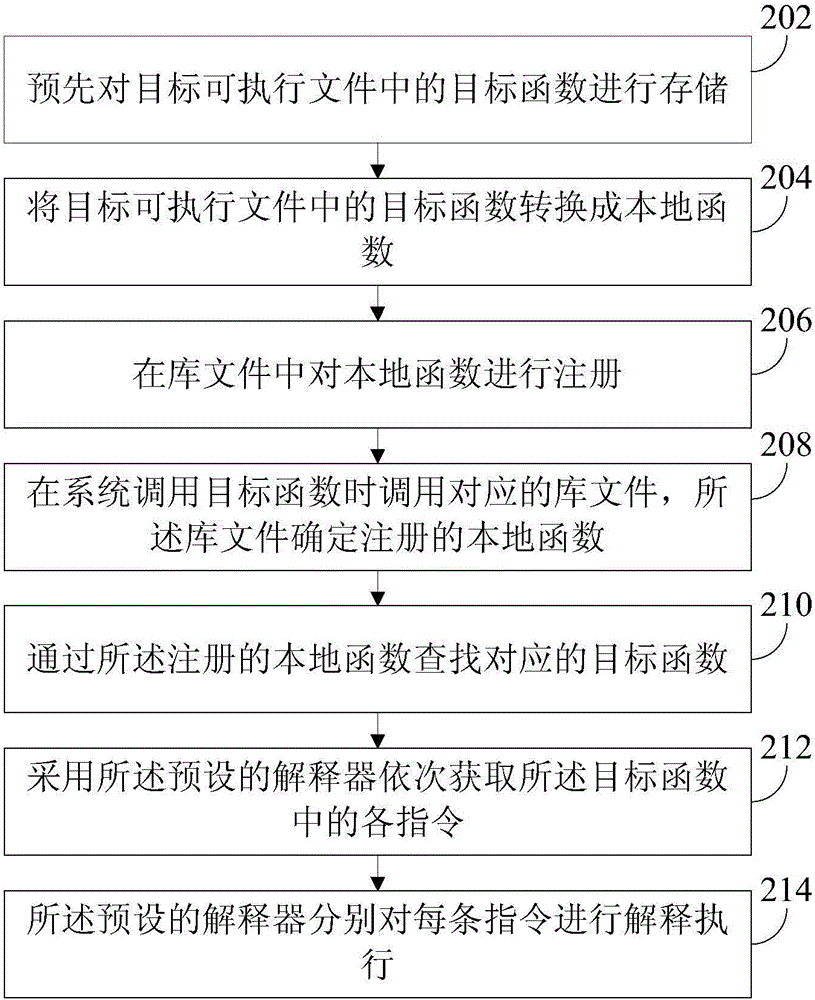
[0041] refer to figure 2 , shows a flow chart of steps of a file hardening method according to another embodiment of the present invention.
[0042] Step 202, pre-store the target function in the target executable file.
[0043] Step 204, converting the target function in the target executable file into a local function.
[0044] Step 206, register the local function in the library file.
[0045] In the embodiment of the present invention, the target executable file to be protected can store its target function in advance, so that the outside cannot crack its execution process during s...
Embodiment 3
[0064] On the basis of the above embodiments, this embodiment also provides a file strengthening device.
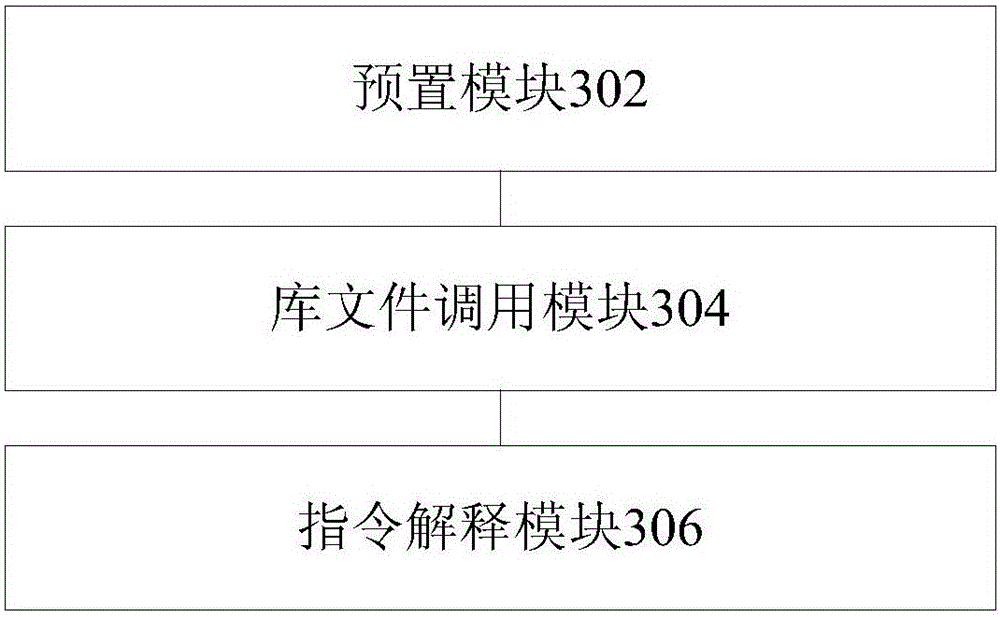
[0065] refer to image 3 , shows a structural block diagram of a file hardening device according to an embodiment of the present invention.
[0066] The preset module 302 is configured to pre-transform the target function in the target executable file and register it in the library file.
[0067] The library file calling module 304 is configured to determine the registered local function through the library file when the system calls the target function.
[0068] The instruction interpreting module 306 is configured to determine the target function according to the registered local function, and sequentially interpret and execute each instruction in the target function through a preset interpreter.
[0069] For the target executable file such as the target function in the dex file, convert the target function, and then register the converted function in the library file...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com