Confidential information transmission method in P2P network based on BitTorrent protocol
A P2P network and secret information technology, applied in the field of computer network and information security, to achieve the effect of low cost and good concealment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] The present invention will be further explained below in conjunction with the accompanying drawings.
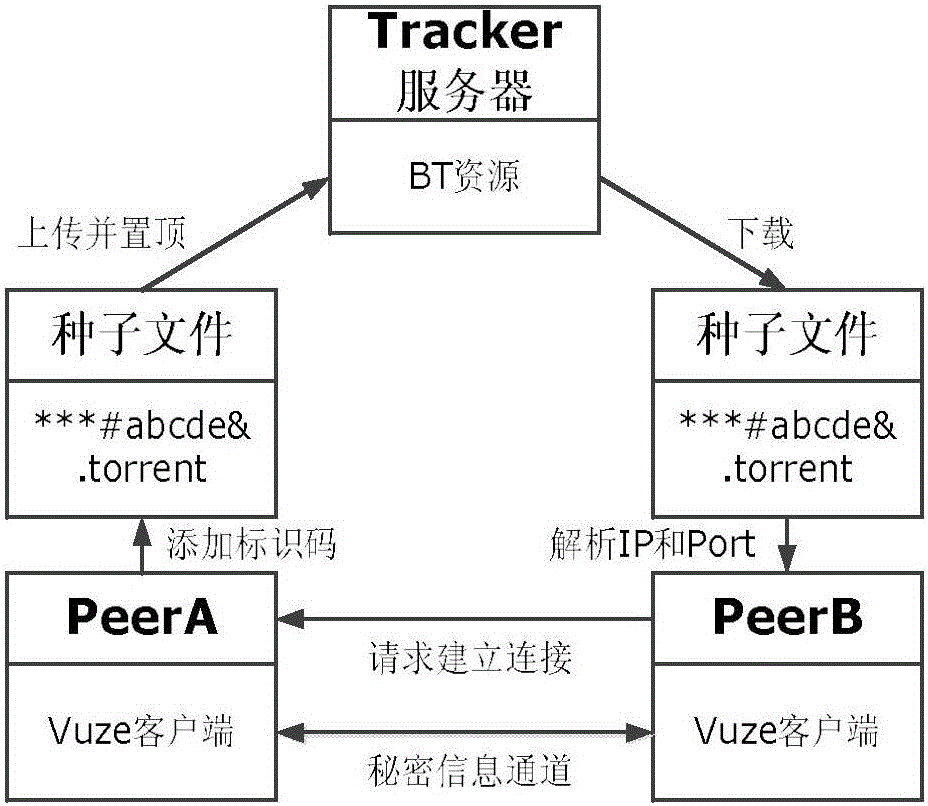
[0027] Taking the client software Vuze4.4 as an example, the secret information transmission method under the P2P network based on the BitTorrent protocol provided by the present invention is further clarified.
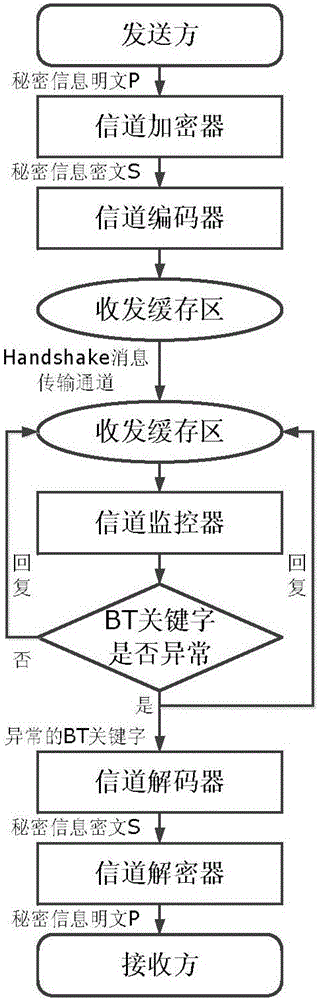
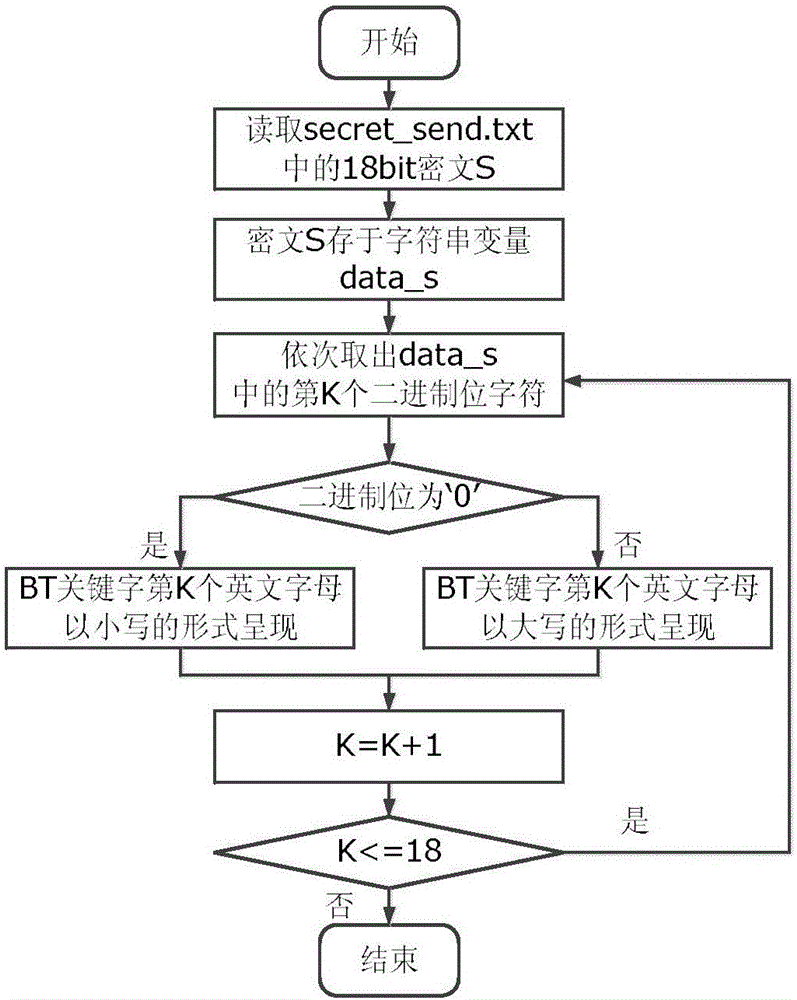
[0028] Such as figure 1 As shown, the present invention implements covert communication based on the Handshake message transmission channel in the P2P network. The sender first encrypts the plaintext P of the secret information to generate a ciphertext S, and then uses a channel encoder to embed the ciphertext S into In the BT keyword of the Handshake message to be sent, the secret information is transmitted out together with the Handshake message. The receiver obtains the string information of the current BT keyword by monitoring the Handshake message receiving channel, and performs corresponding operations according to whether it is an abnormal BT keyword; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com