Device and method for accessing computer desktop service in multi-network isolation environment
A technology of service access and access method, applied in the field of computer desktop service access devices, can solve the problems of vulnerable security, high hardware cost, attacking the network, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
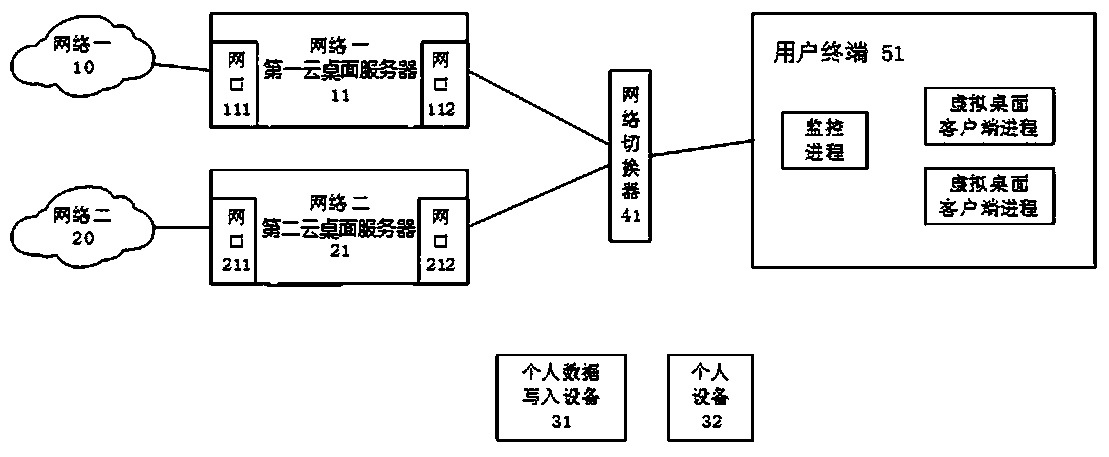
[0017] refer to figure 1 , the computer desktop service access device in a multi-network isolation environment includes a first cloud desktop server 11 (ie, a virtual desktop server) and a second cloud desktop server 21 (ie, a virtual desktop server), and the first cloud desktop server 11 is located in an isolated network. 10, the first cloud desktop server 11 through the physical network interface 111 (ie figure 1 The network port in the network port) is connected to the isolated network one 10, the second cloud desktop server 21 is located in the isolated network two 20, and the second cloud desktop server 21 is connected through another physical network interface 211 (i.e. figure 1 network port) to connect to isolated network 2 20, isolated network 1 and isolated network 2 are physically separated, each cloud desktop server runs a virtual machine, and each virtual machine runs a user virtual desktop environment, which can provide users with Virtual desktop service, user ap...
Embodiment 2
[0023] The difference between this embodiment and Embodiment 1 is that there may be three or four isolated networks. The user terminal is a PC. The user's personal device 32 is a password-protected USB password device that stores a personal identity certificate. There are 3 virtual desktop client processes running in the user terminal 51, forming a process queue, and each monitoring process selects the queue head process to connect to the cloud desktop server in the isolated network physically connected through the network switcher. When the network is switched, the process at the head of the queue is dequeued and destroyed, and a new process at the head of the queue is selected to automatically connect to the cloud desktop server in the new network based on personal data. When the computing resources of the user terminal are idle, a new virtual desktop client process is started and added to the tail of the queue.
Embodiment 3
[0025] The difference between this embodiment and Embodiment 1 is that the network port 112 is connected to a certain port of the network switch 41 through the network, and the other network port 212 is connected to a certain port of the network switch 41 through the network.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com