System boot method and apparatus
A technology of system guidance and guidance devices, applied in the field of information security, can solve problems such as insufficient security and low security of open source mobile operating systems, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
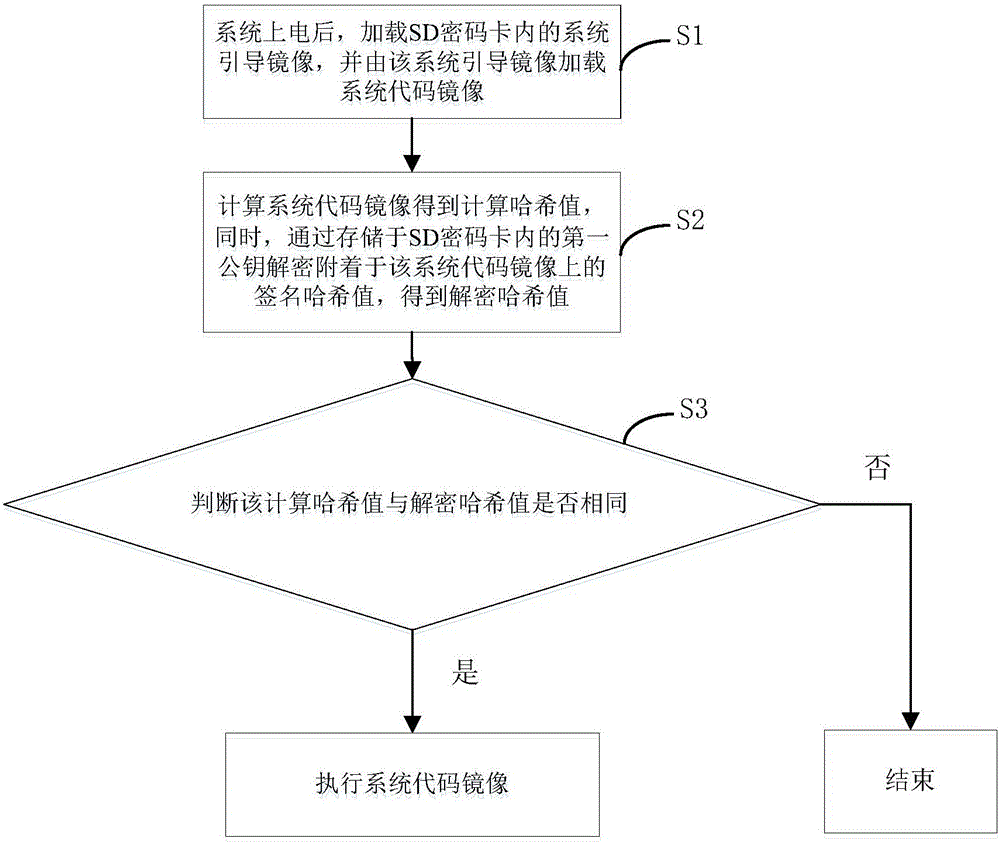
[0053] see figure 1 , is a flow chart of the first embodiment of the system startup and guidance method of the present invention. In the first embodiment of the system startup and guidance method, the method includes:
[0054] S1, after the system is powered on, load the system boot image in the SD password card, and load the system code image from the system boot image;
[0055] This embodiment is applied to terminal devices running mobile operating systems, such as smart phones, tablet computers, and notebook computers.
[0056] During the startup process of the terminal device, the system boot image preset in the SD password card is loaded through the system startup command. Wherein, the SD password card refers to an SD memory card with an encryption and decryption chip and a private storage area. Specifically, two sub-storage areas are set in the private storage area, one of which is the first sub-storage area for storing the system boot image, The second is the second s...
Embodiment 2
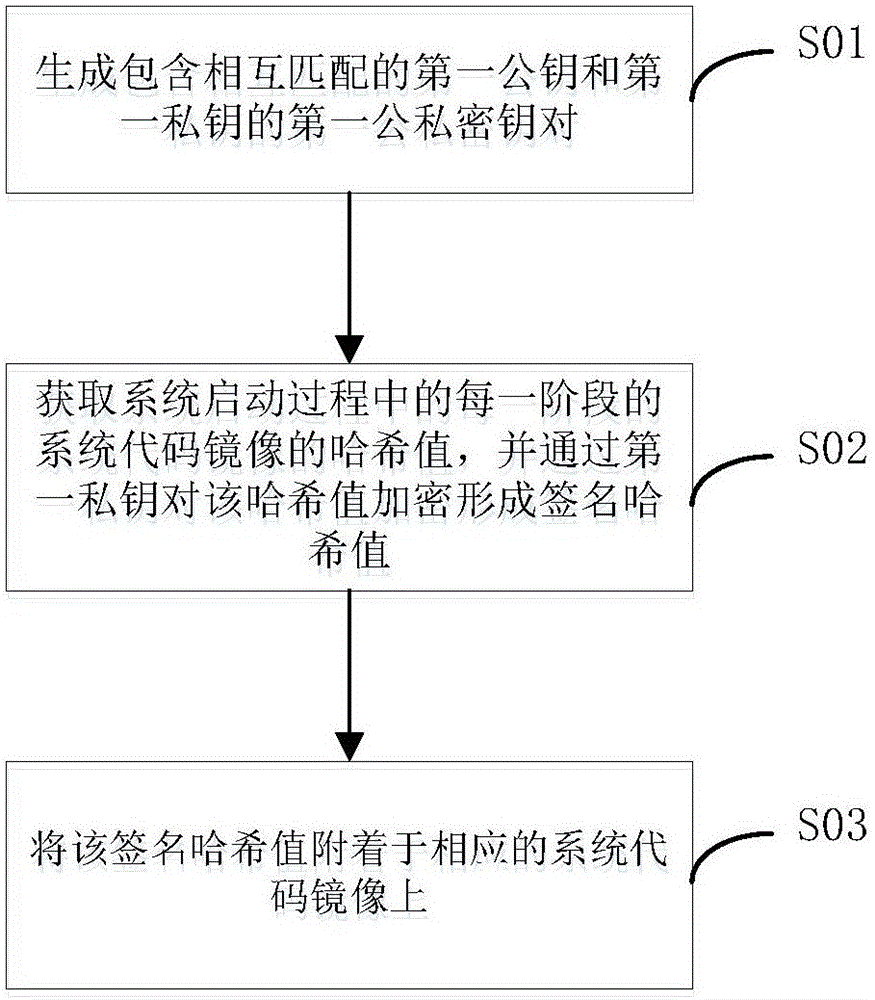
[0069] see figure 2 , is the flow chart of the second embodiment of the system boot method of the present invention, the second embodiment of the system boot method is based on the first embodiment above, loading the system boot image in the SD password card, and according to Before loading the system code image, the system boot image also includes:
[0070] S01, generating a first public-private key pair including a first public key and a first private key that match each other;
[0071] S02. Obtain the hash value of the system code image at each stage in the system startup process, and encrypt the hash value with the first private key to form a signature hash value;
[0072] S03. Attach the signature hash value to the corresponding system code image.
[0073] Wherein, the first public-private key pair is generated by a security agency, or may be generated by a terminal manufacturer through a key generator, etc., and the generated first public-private key pair includes a f...
Embodiment 3
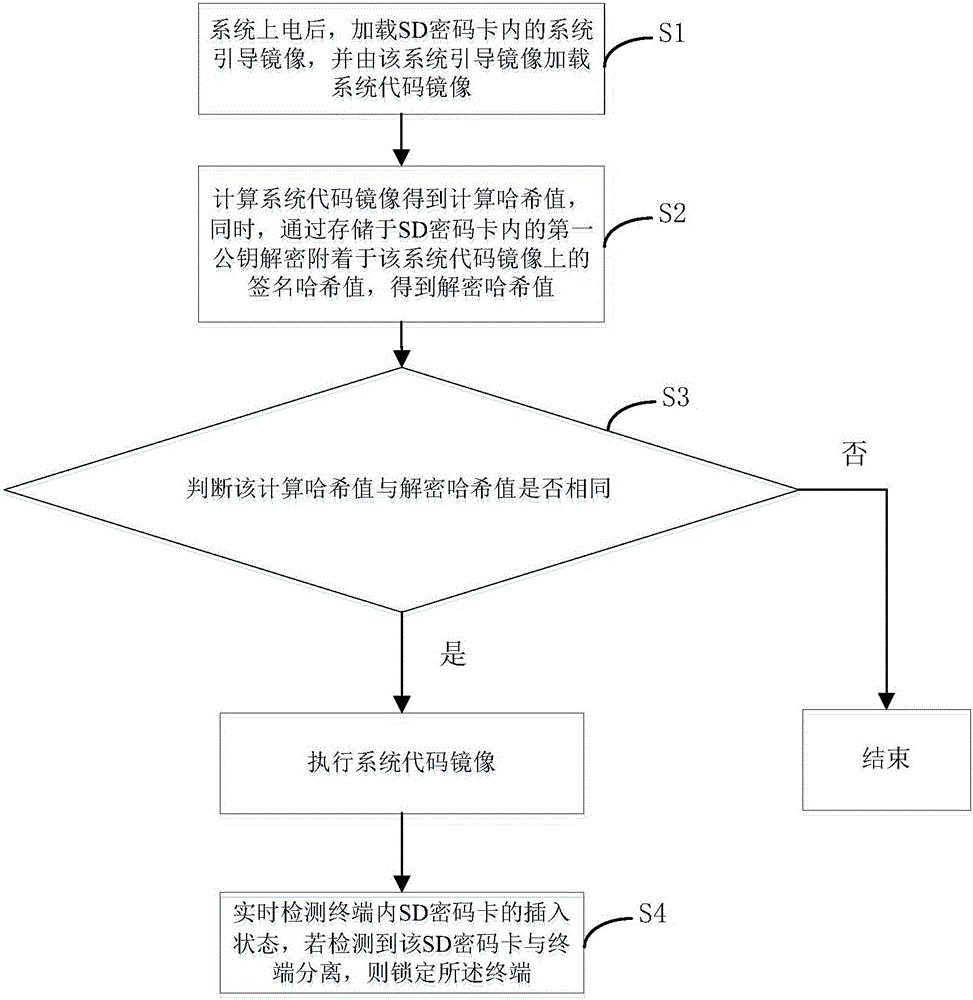
[0077] see image 3 , is a flowchart of the third embodiment of the system startup and guidance method of the present invention. The third embodiment of the system startup and guidance method is based on the above-mentioned first embodiment or the second embodiment, and this embodiment also includes:
[0078] S4, detecting in real time the insertion state of the SD password card in the terminal, and locking the terminal if it is detected that the SD password card is separated from the terminal.
[0079] The terminal system detects the SD encryption card inserted into the terminal in real time, and if it detects that the SD encryption card is separated from the terminal, the terminal is locked. It can be understood that the separation of the SD password card from the terminal may also be caused by damage to the SD password card or improper insertion. And locking the terminal may also be shutting down, locking the screen, and the like.
[0080] Further, in order to prevent the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com