An Active Security Guarantee Method for Linux Servers
An active security and server technology, applied in the direction of electrical components, transmission systems, platform integrity maintenance, etc., can solve the problems of system resource management firewall management, user management file management, and insufficient monitoring of log security audit status
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The present invention will be further explained below in conjunction with the accompanying drawings.
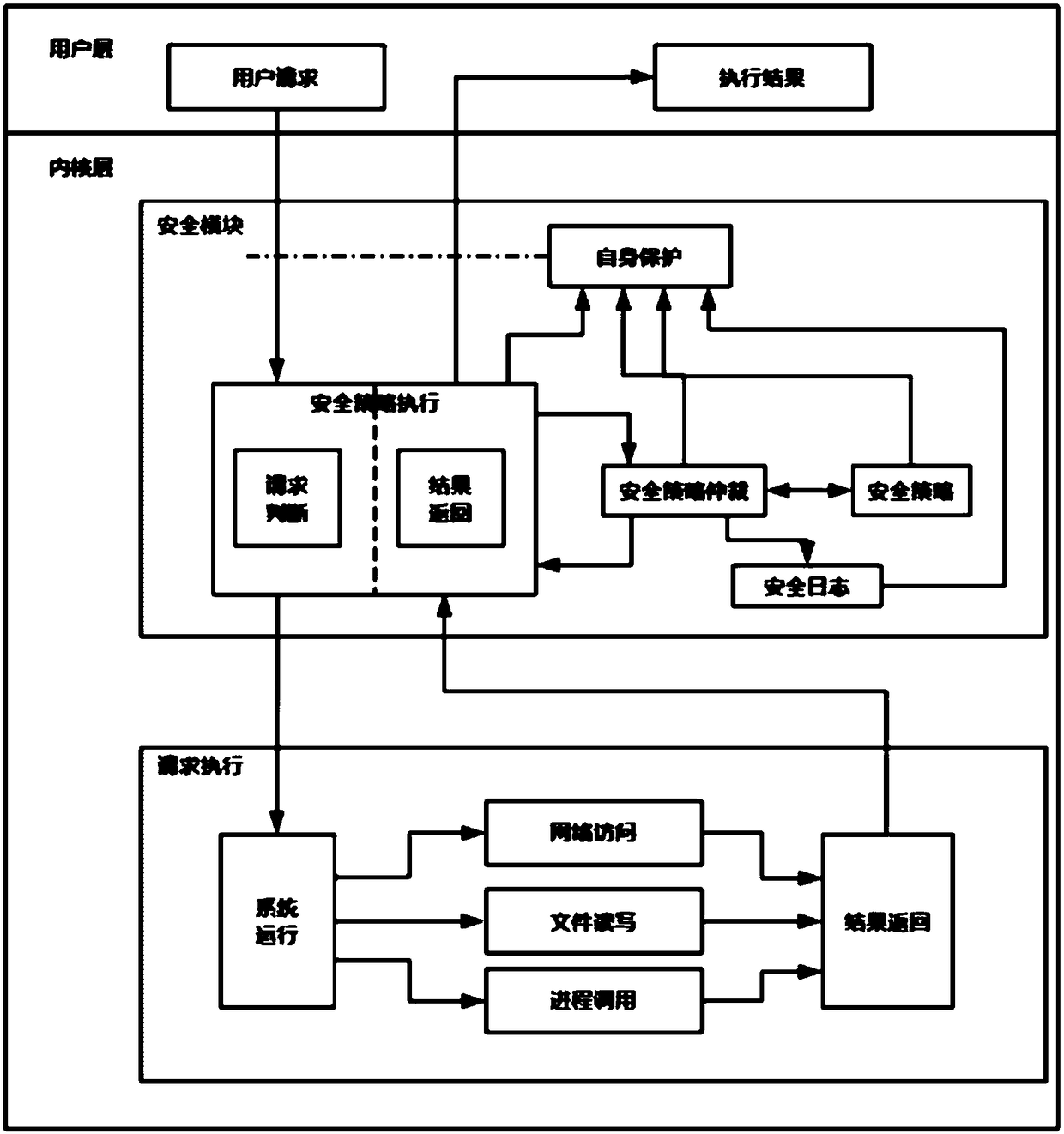
[0043] The security guarantee method of the present invention provides a kind of global security policy, mainly comprises following 9 aspects:
[0044] 1. Recompile the kernel and embed the security module into the Linux kernel.
[0045] 2. The system security module is loaded in the Linux system kernel loading stage.
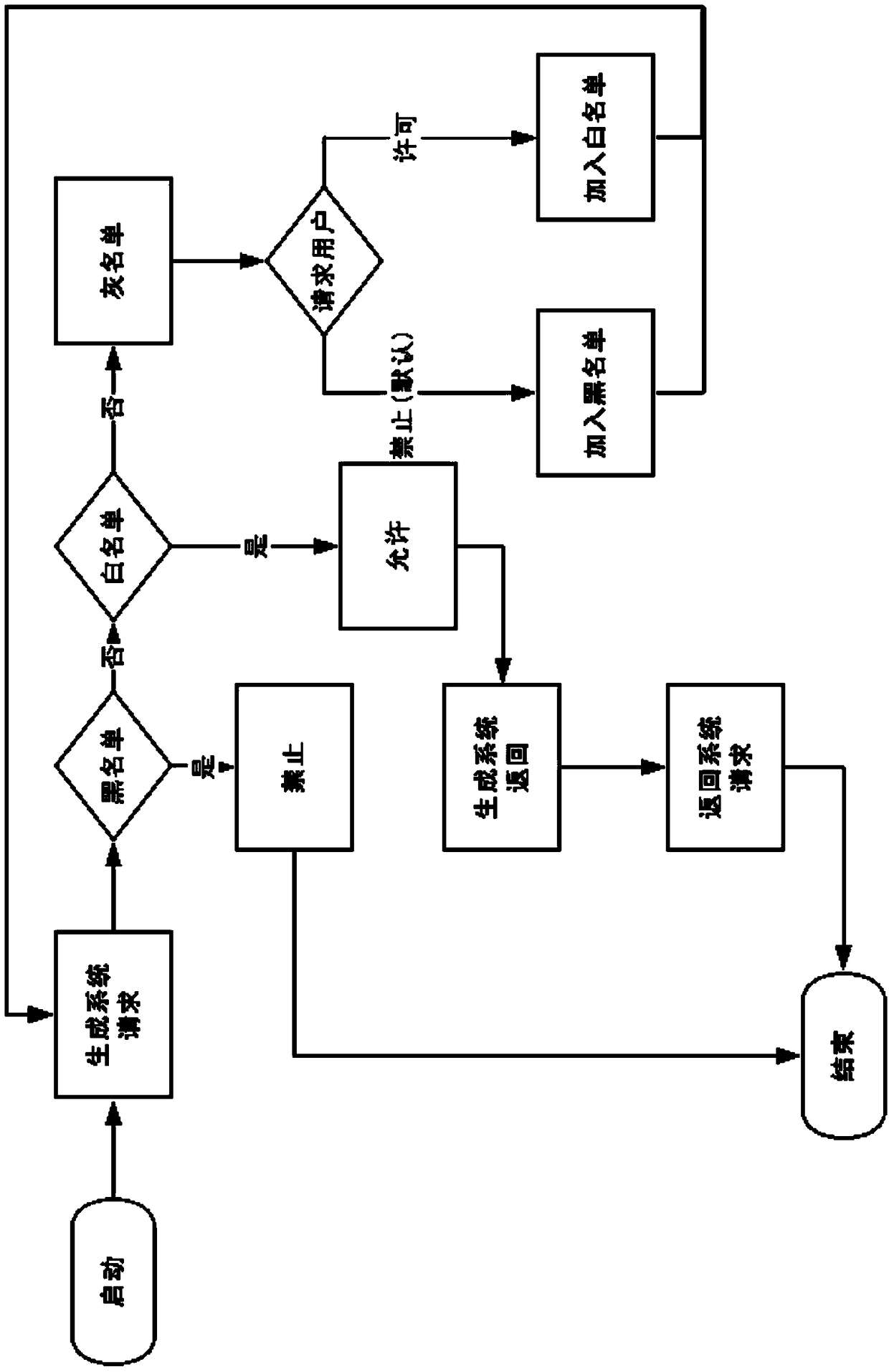
[0046] 3. The security policy execution module intercepts all user requests (including process execution, network access, file reading and writing, etc.) and submits them to security policy arbitration for judgment.
[0047] 4. When the policy arbitration is a whitelist item, the execution module releases the request.
[0048] 5. When the policy arbitration is a blacklist item, the execution module will prohibit the request.
[0049] 6. When the policy arbitration is a gray list item, the execution module will prohibit the request, and then ask the u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com