D2D communication physical layer group key generation method based on base station control
A method for generating a communication group and a technology for a communication group, applied in the field of communication, can solve the problems of difficulty in obtaining authentication of the identity security of user equipment in group communication, difficulty in achieving a key generation rate, low key generation rate, etc., so as to improve the key generation efficiency. , the effect of reducing bandwidth and transmission time, high key generation rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] The present invention will be further described below in conjunction with the accompanying drawings.
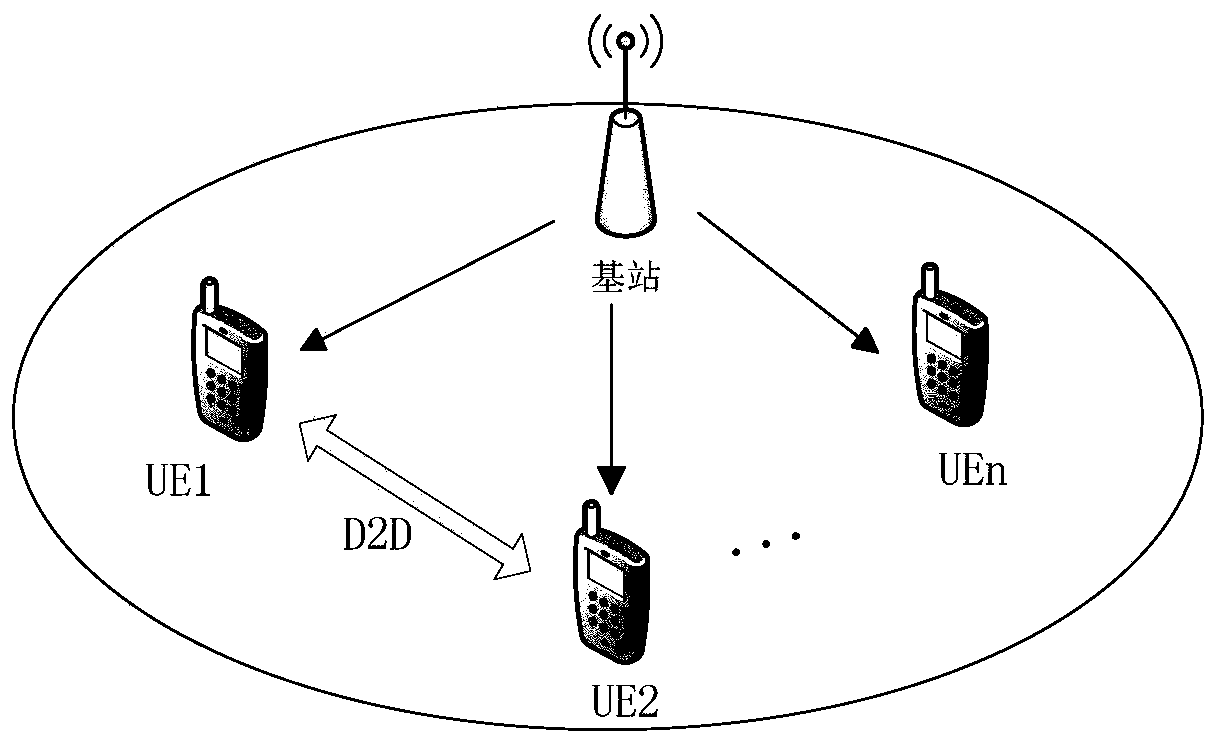
[0021] refer to figure 1 , the scenario used in the present invention includes user equipment UE and base station, wherein, the user equipment UE and the base station can communicate directly, and the communication between the user equipment UE includes two types: one is that the user equipment UE communicates with the base station as an intermediary, The second is that the user equipment UE communicates directly under the control of the base station; the base station can authenticate the identity of the user equipment UE, and control the connection process of the D2D communication and the generation process of the group key.
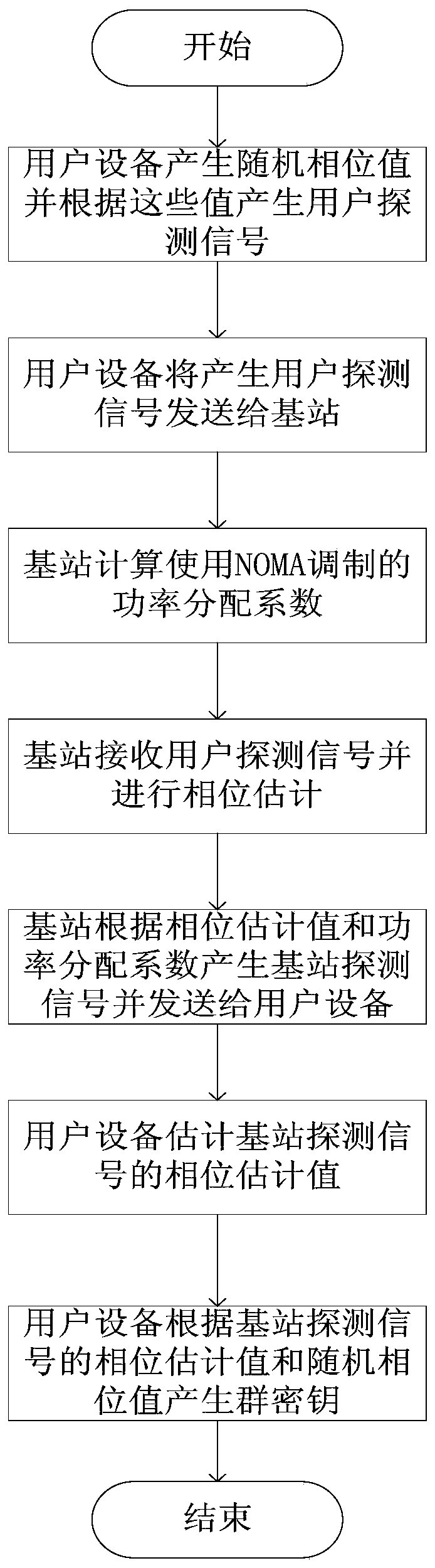
[0022] refer to figure 2 , the implementation steps of the present invention are as follows:
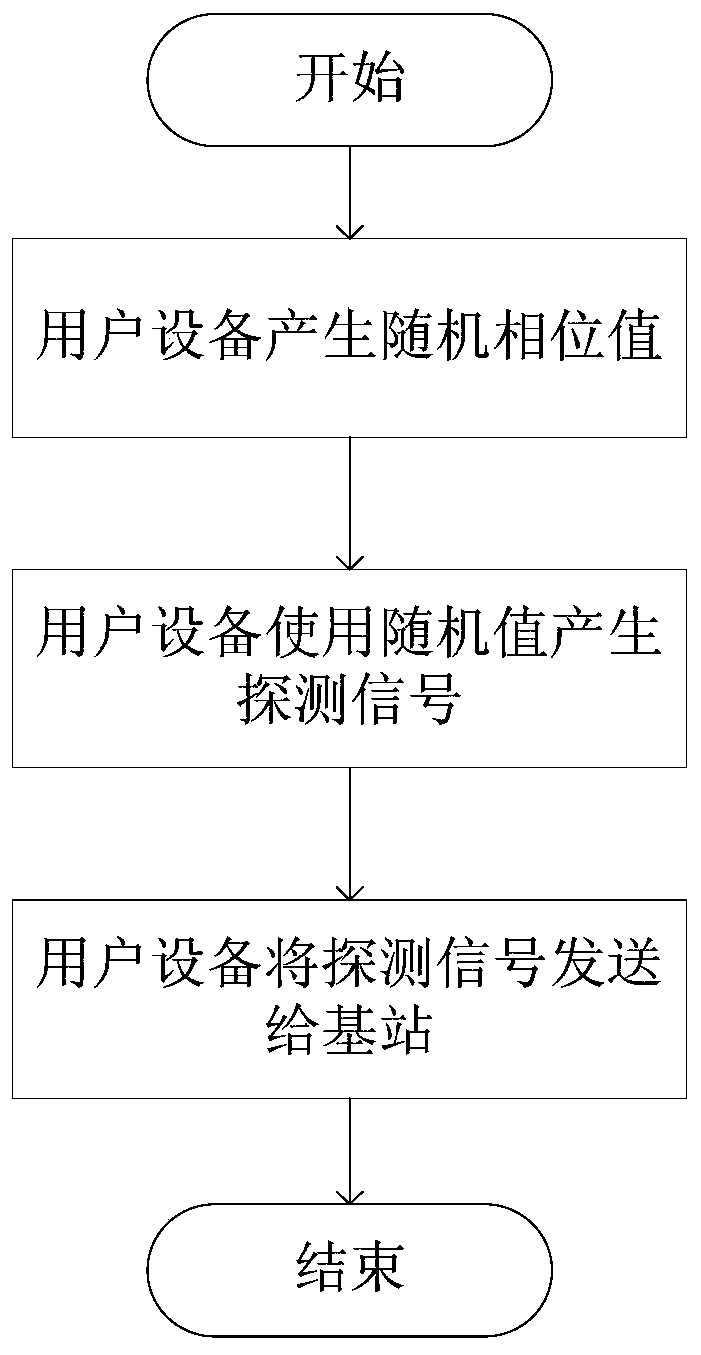
[0023] In step 1, the user equipment UE generates random phase values, and uses these values to generate user sounding signals, which are sent to...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com