IO efficient detection method of large-scale system loop
A large-scale, loop technology, applied in fault hardware testing methods, error detection/correction, detection of faulty computer hardware, etc., can solve problems such as memory algorithms are not very practical, reduce memory jitter and reduce complexity Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] In order to facilitate those skilled in the art to understand the technical content of the present invention, the content of the present invention will be further explained below in conjunction with the accompanying drawings.
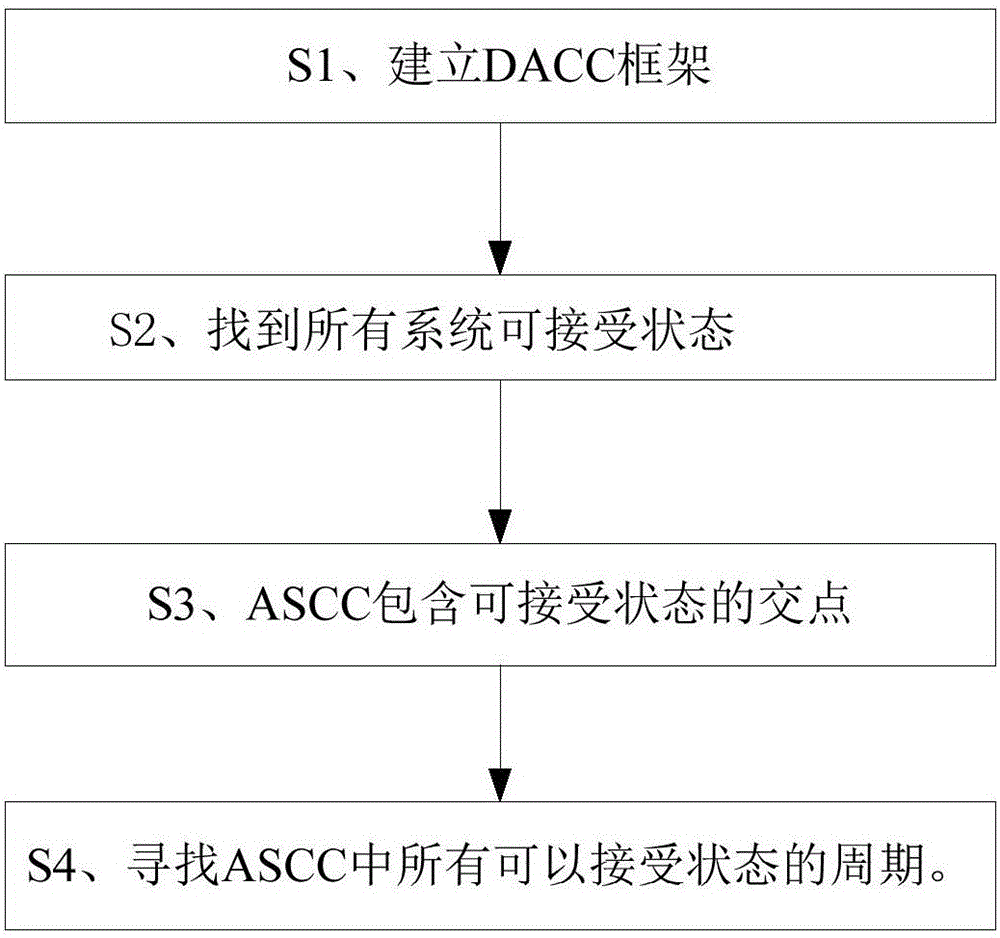
[0034] like figure 1 Shown is the scheme flow chart of the present invention, the technical scheme of the present invention is: a kind of IO high-efficiency detection large-scale system loop method, comprising:
[0035] S1. Establish a DACC framework and traverse all acceptable state sets. For each acceptable state, first use the SFA algorithm to find the acceptable state contained in the ASCC, and then use FACA to find the acceptable loop of the ASCC. Accepting states have been traversed, and all acceptable cycles have been found.
[0036] S2. Use the external breadth-first algorithm BFS by calling enumerateBFS(), and then use the algorithm EPH to form MPHF; according to the DACC framework established in step S1, DACC finds all acceptable state...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com