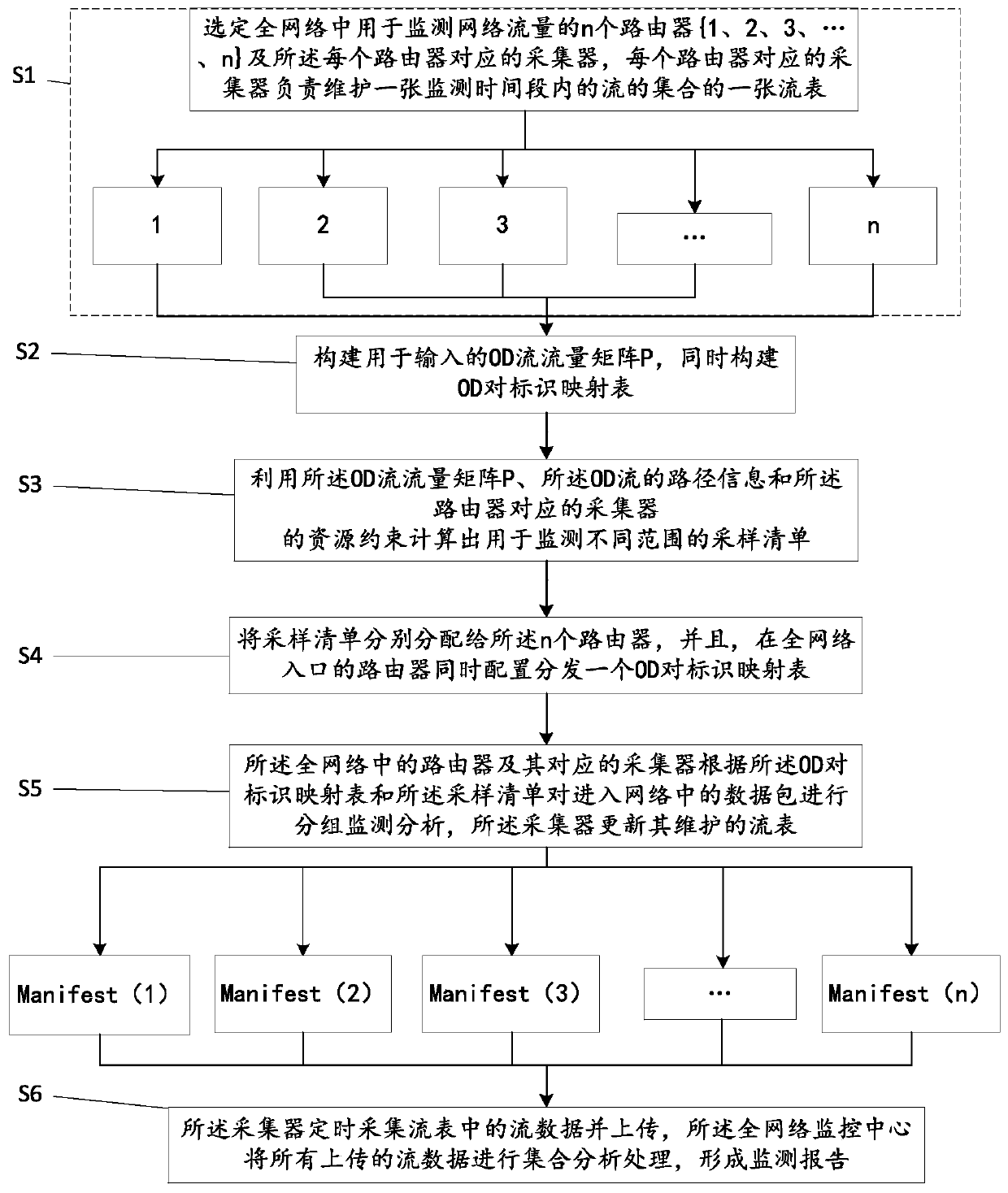
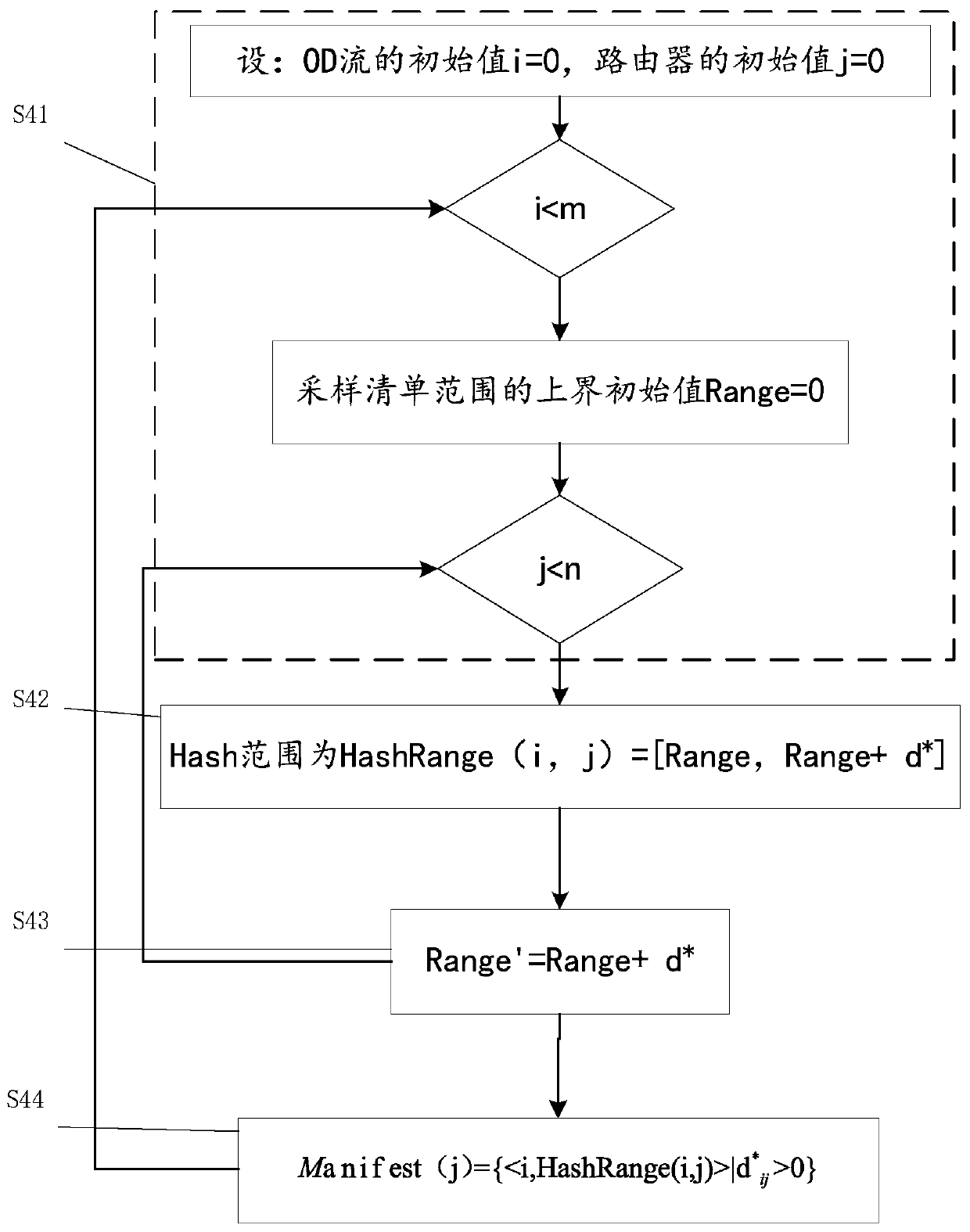
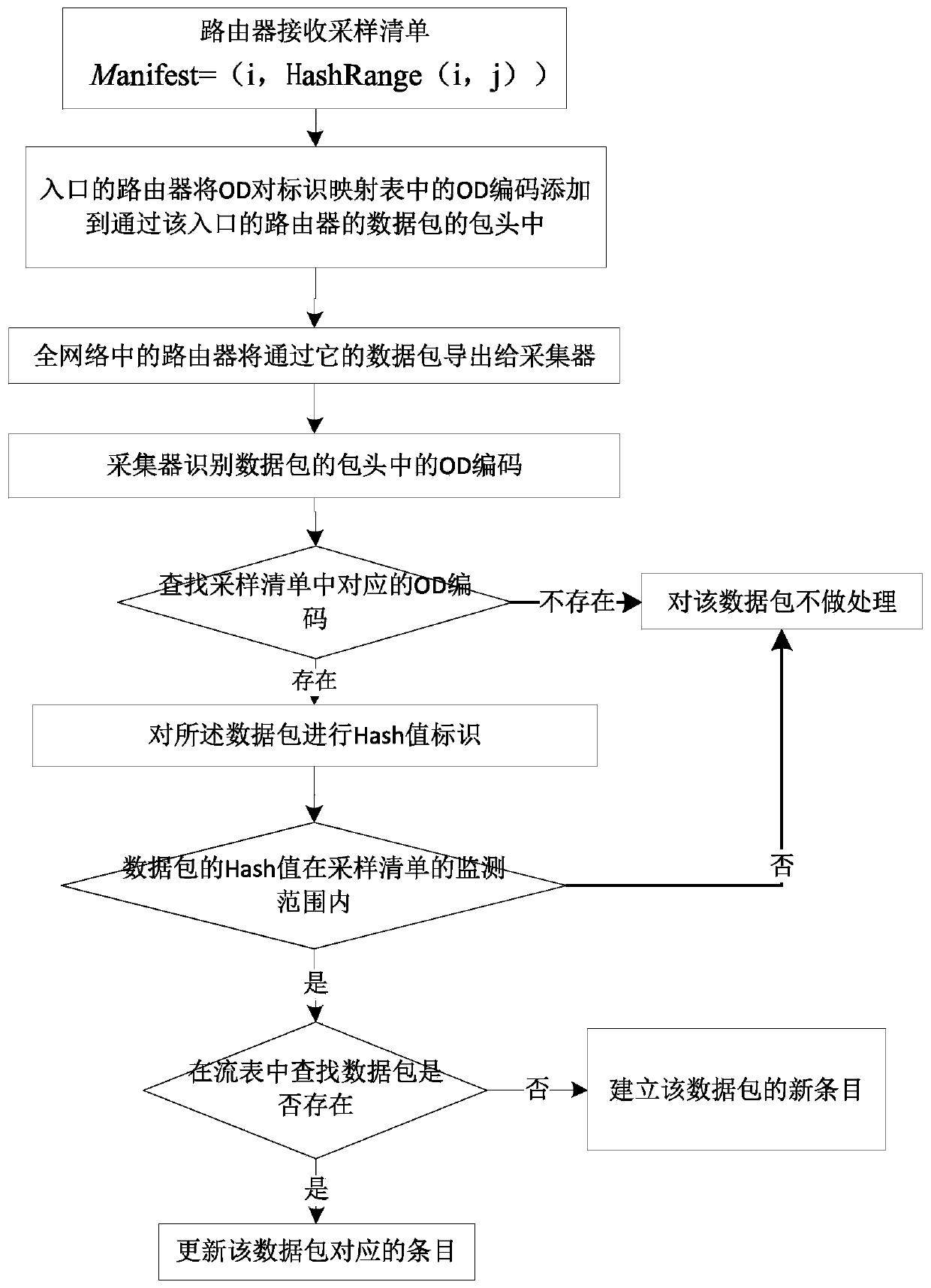
A whole network traffic monitoring method
A network traffic and network monitoring technology, applied in the field of information security, can solve the problems of lack of application, not well applicable to the whole network big data monitoring, and increase the flow coverage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 2
[0115] The difference between this embodiment and Embodiment 1 is that the above sampling list can also be calculated using the directed graph method to solve the edge E of the OD flow to the router 3 , the solution method is as follows: It is known to transform the entire network into a directed graph G, where V represents a node, and E represents an edge connecting each node;
[0116] V={source,sink}∪{OD i} 1≤i≤m ∪{R j} 1≤j≤n , where source represents the source point and sink represents the sink point;
[0117] E=E 1 ∪E 2 ∪E 3 , where E 1 Indicates the edge from the source point to the OD flow, E 2 represents the edge from the router to the sink, E 3 Indicates the edge of the OD flow to the router;
[0118]
[0119] Let f(x, y) represent the flow at the boundary (x, y)∈E, 1≤f≤m, and the constraints used for solving are:
[0120]
[0121]
[0122]
[0123]
[0124] Among them, T f Represents the number of OD flow f, R j Represents the resource con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com