Method for generating attack graphs based on status transition network attack model
A network attack and state transfer technology, applied in data exchange networks, digital transmission systems, electrical components, etc., can solve problems such as state explosion, attack graph differences, and increase the scale of attack graphs to improve accuracy, high accuracy, Intuitive effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
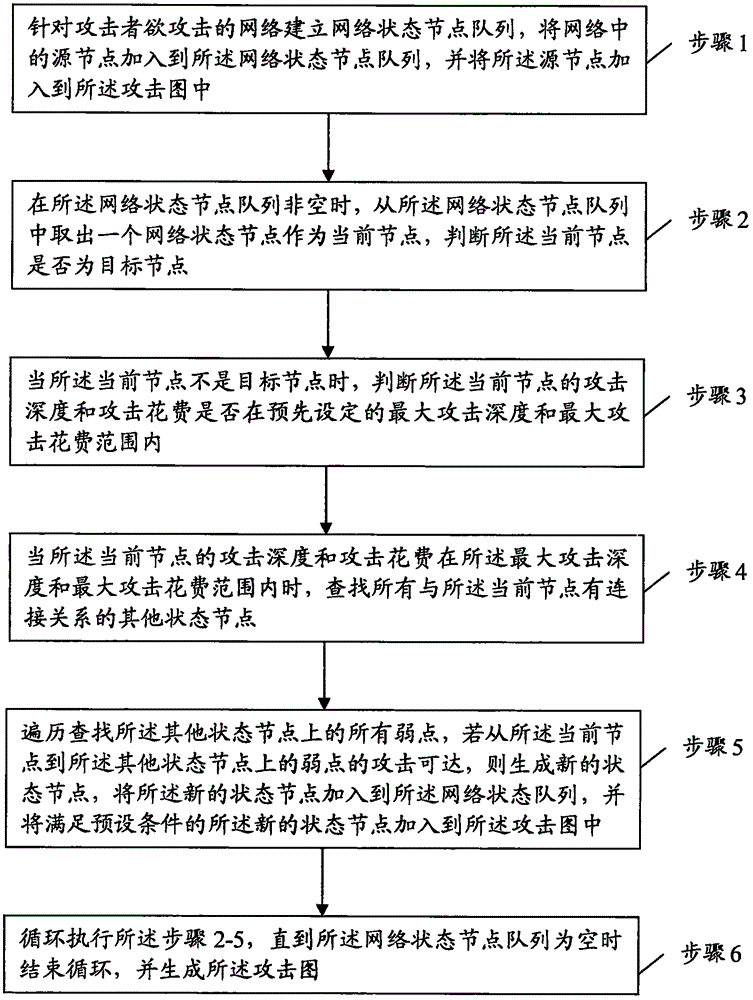
[0050] In order to make the purpose, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
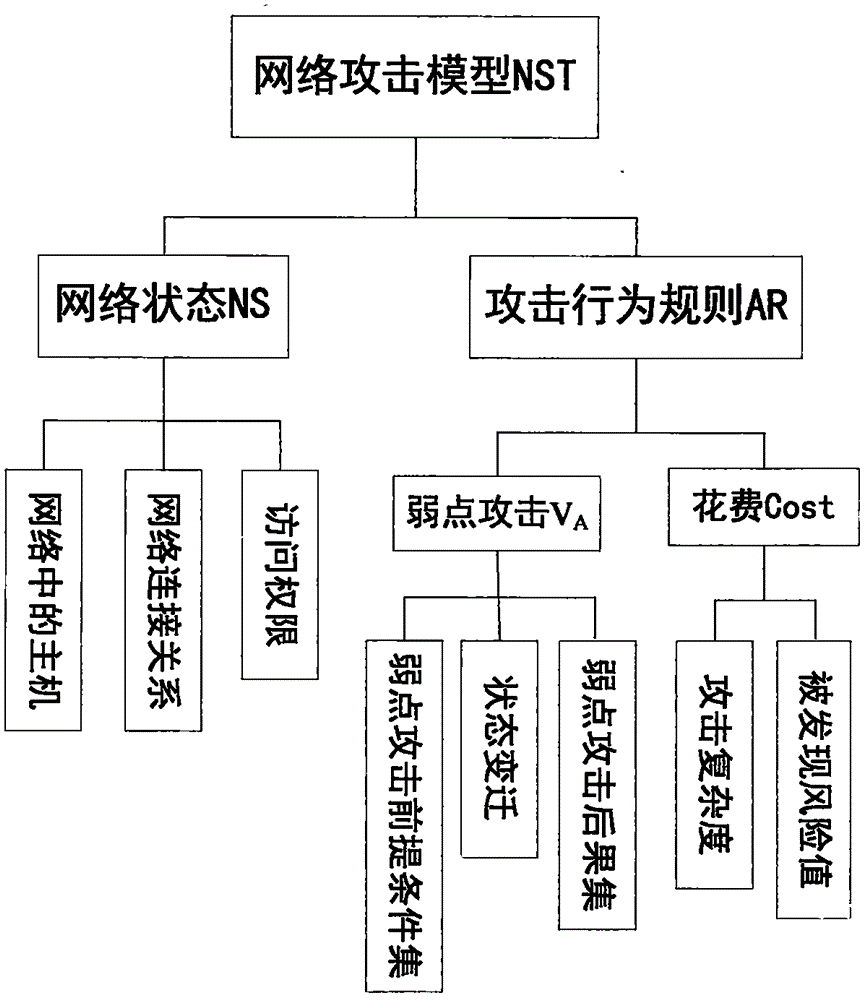
[0051] figure 1 It is a network attack model (NST model) based on state transition. The NST model can be represented by a two-tuple, that is, NST=(NS, AR). Among them, NS is the set of network states that make up the model, and AR is the set of attack behavior rules.
[0052] The network state set NS is represented by the following triplet: NS=(Hd, Nl, Crol).
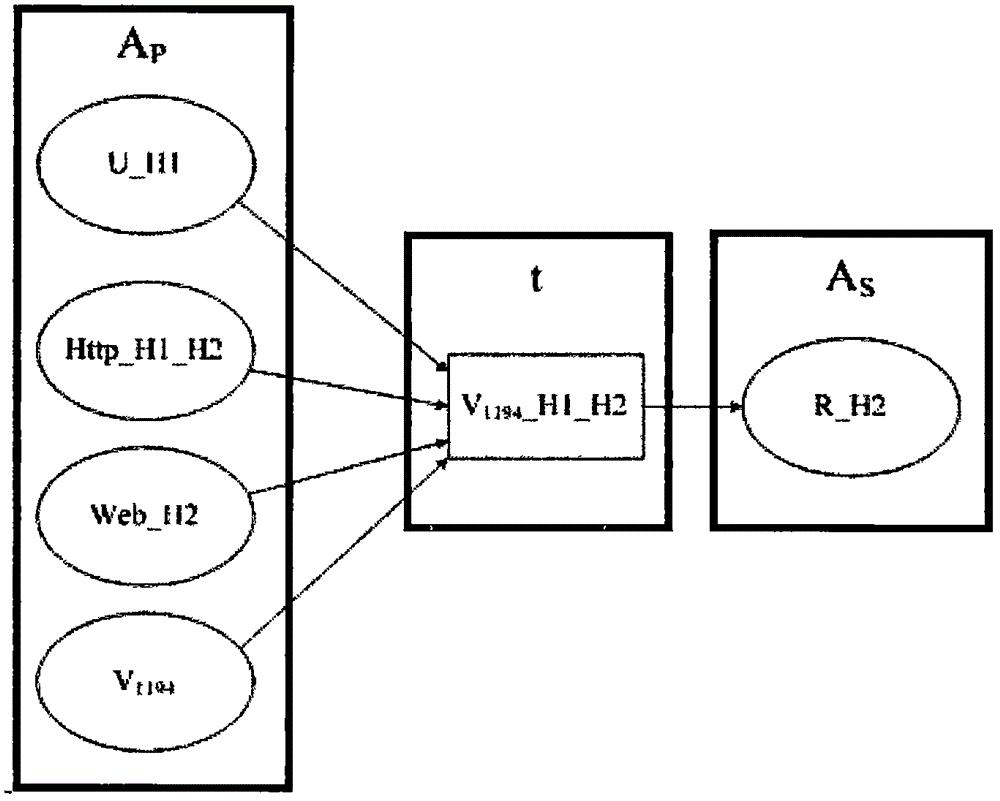
[0053] Hd is the host in the network, namely Hd=(hostid, os, sers, v). hostid is the unique identifier for distinguishing hosts in the network, which can be expressed by IP address; os is the version information of the operating system running on the host; sers indicates the open service of the host, which can be expressed by port number; v indicates the list of weaknesses on th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com