Hypertext transfer protocol secure (HTTPS) service deployment method
A server and private key technology, applied in the direction of electrical components, transmission systems, etc., can solve problems such as prolonging the handshake process time, reducing user experience, keyserver reliability and performance bottlenecks, and achieving reduced operation and maintenance costs, high security, and weakened effect of influence
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
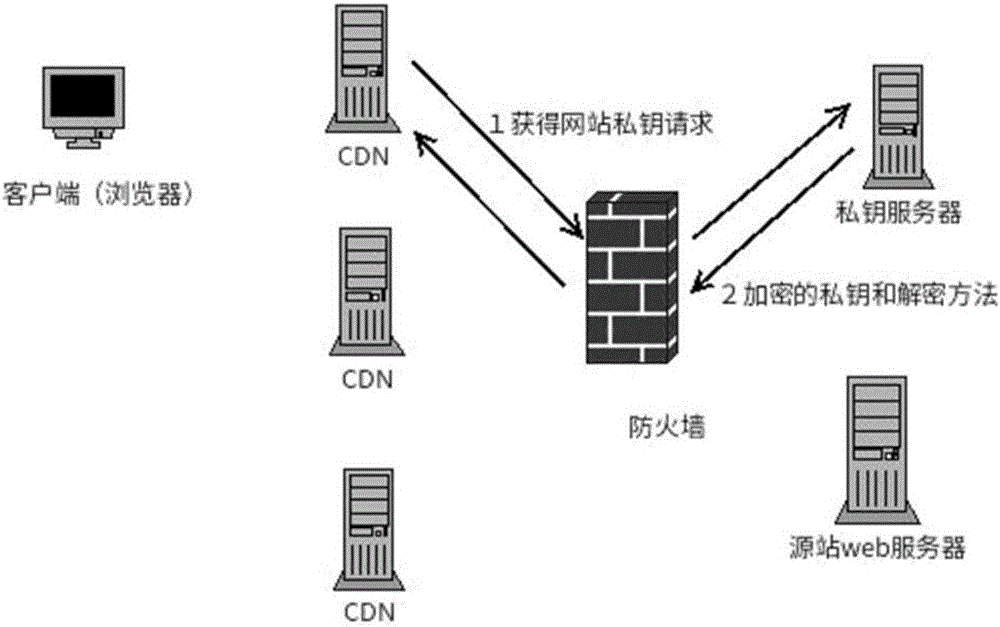
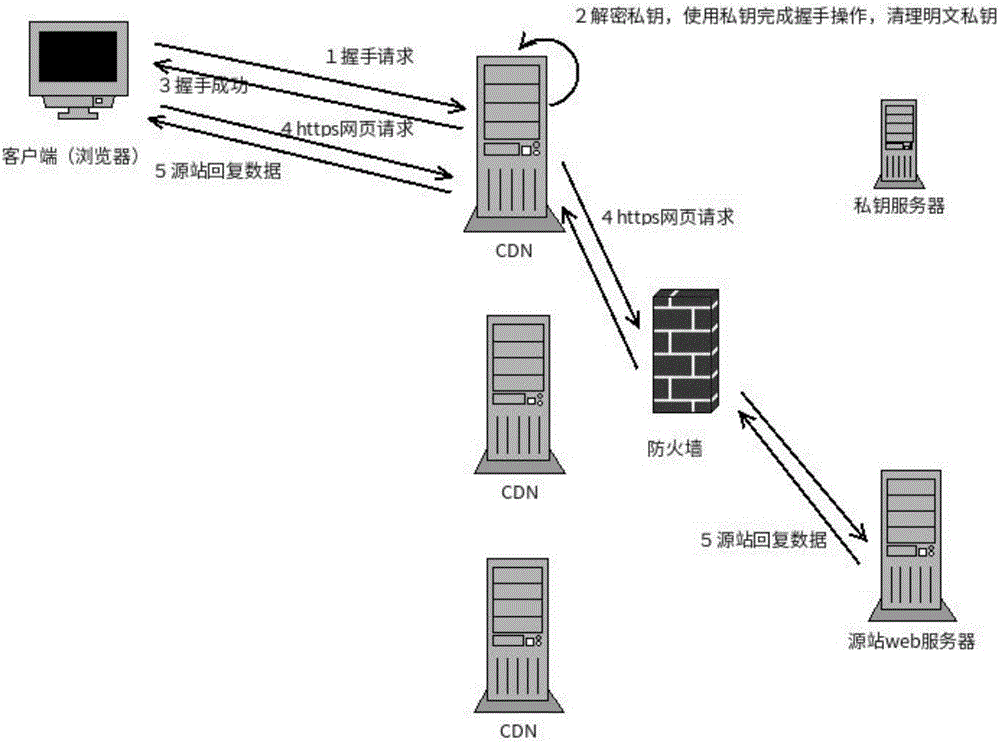
[0025] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments. The method of the present invention does not deploy the private key at the CDN node, but deploys the encrypted private key on the key server, and the CDN node obtains the encrypted key and the decryption method from the key server, and stores them in the memory. During the handshake process, the private key is decrypted for handshake, and it is cleared from the memory immediately after the handshake is completed. Since there is no plaintext private key deployed on the node, there is only a plaintext private key in the memory at the moment of the handshake, even if it is extremely difficult to obtain the private key when logging in to the node. It does not need to interact with the key server every time it is accessed, and has minimal impact on system performance and reliability.
[0026] Such as figure 1 As shown in , the private key...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com