User identification method, user identification system, user identification device, user identification processing method, and user identification processing device
A user identification and user technology, applied in the communication field, can solve problems such as poor user experience, and achieve the effect of improving technical effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
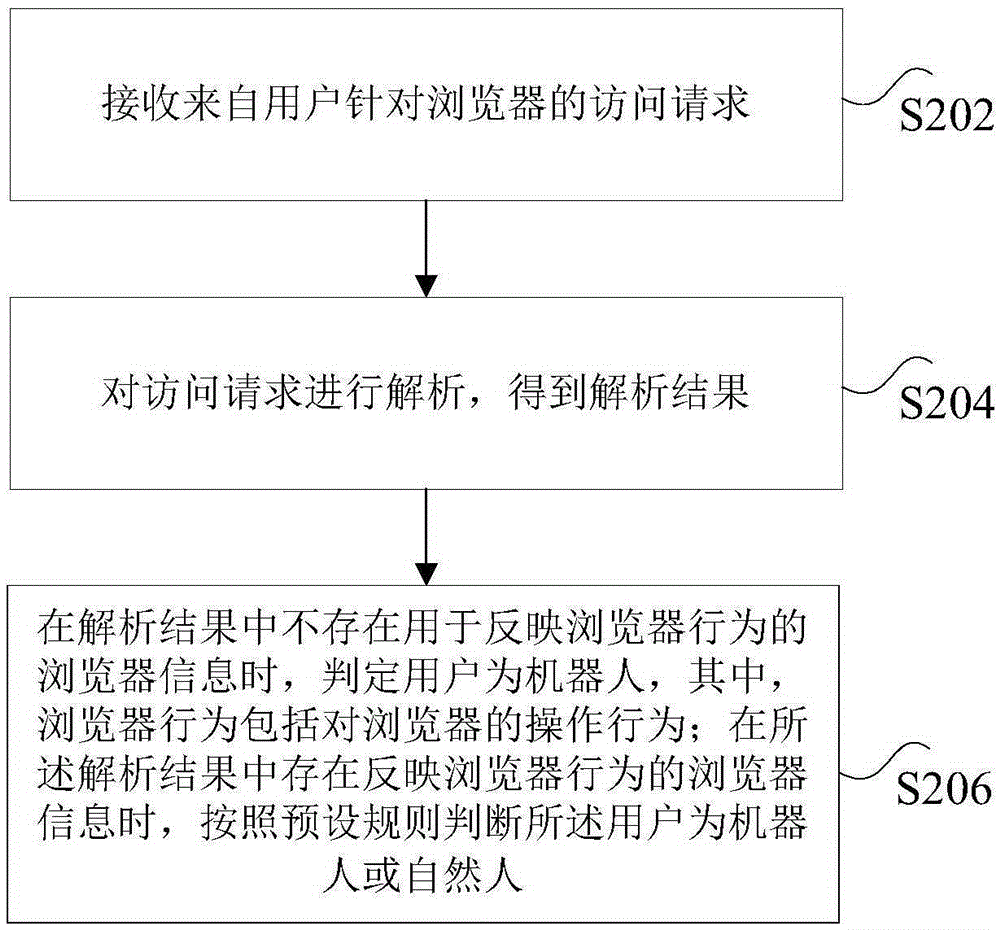
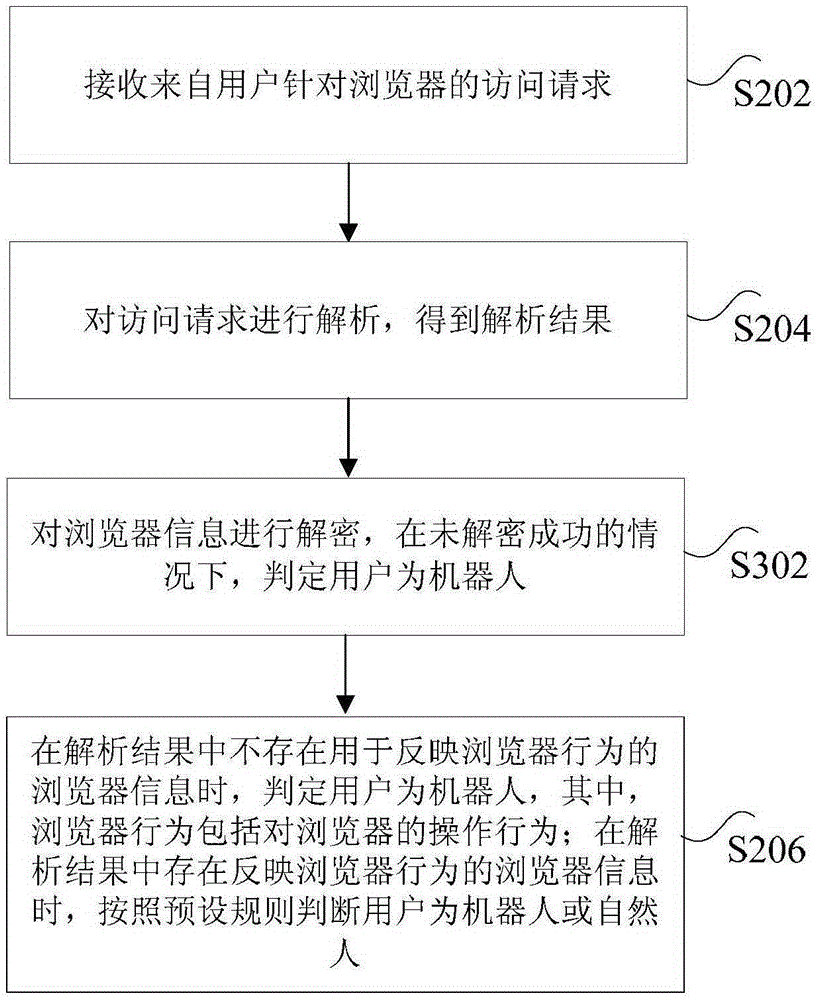
[0048] According to an embodiment of the present invention, an embodiment of a method for user identification is also provided. It should be noted that the steps shown in the flowcharts of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, and, Although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
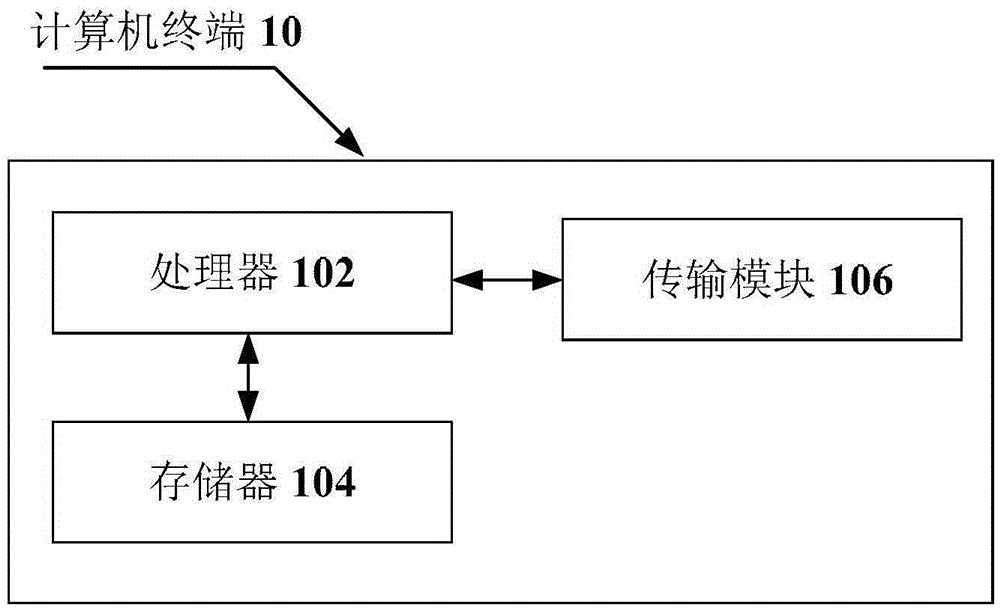
[0049] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. Take running on a computer terminal as an example, figure 1 It is a hardware structure block diagram of a computer terminal of a user identification method in an embodiment of the present invention. Such as figure 1 As shown, the computer terminal 10 may include one or more (only one is shown in the figure) processors 102 (the process...
Embodiment 2
[0112] According to an embodiment of the present invention, a user identification system is also provided, Figure 5 is a schematic diagram of a user identification system according to an embodiment of the present invention Figure 1 ,Such as Figure 5 As shown, the system includes: a network resource service component 52, a human-machine identification component 54;
[0113] The network resource service component 52 is used to receive the user's access request for the browser, and send the access request to the machine identification component 54;
[0114] In an optional embodiment of the present invention, the above-mentioned network resource service component includes but is not limited to at least one of the following: member registration server, mail server, transaction server, content management server, real-time communication server, payment server, and forum server.
[0115]In the embodiment of the present invention, taking a user posting a new post in a forum as an ...
Embodiment 3
[0135] According to an embodiment of the present invention, a device for implementing the user identification method in Embodiment 1 is also provided, Figure 8 is the structural frame of the user identification device of the embodiment of the present invention Figure 1 ,Such as Figure 8 As shown, the device includes:
[0136] A receiving module 82, configured to receive an access request from a user for a browser;
[0137] In the embodiment of the present invention, taking a forum to publish a new post as an example, the access request includes a form of page information filled in by the user, such as the title of the forum post filled in by the user, the content of the post, etc., and may also include browser information. Browser information includes browser operation behavior information, such as mouse and keyboard operation information performed by users when filling in post titles or post content. The operation information may refer to the number of operations, but is...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com