Ransomware processing method and system
A processing method and software technology, applied in the field of information security, can solve the problems of not clearing, taking a long time, occupying, etc., and achieve the effect of preventing further infringement and narrowing the scope of judgment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
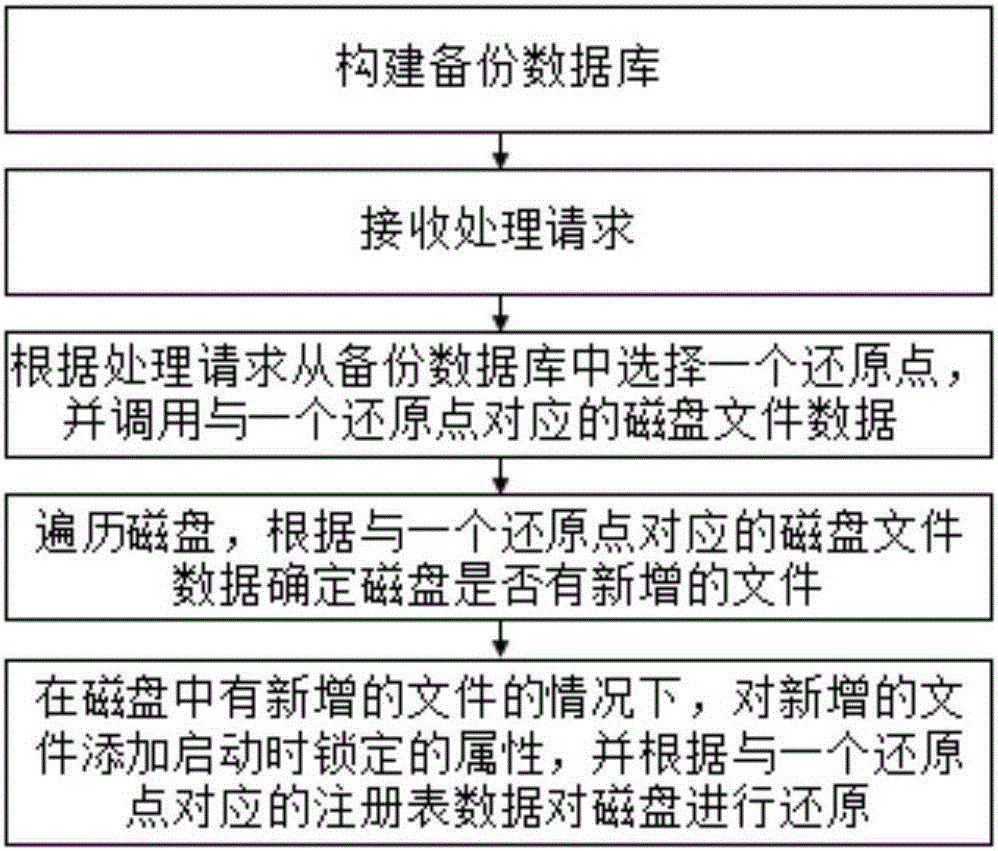
[0030] figure 1 It is a schematic flow chart of an optional processing method for ransomware in Embodiment 1 of the present invention Figure 1 .
[0031] Such as figure 1 As shown, a processing method against ransomware, including:
[0032]Step S100, constructing a backup database, wherein the backup database includes at least one restoration point and restoration data corresponding to each restoration point, and the restoration data includes registry data and disk file data.
[0033] Specifically, the registry data in the restoration data may be data in key parts of the registry, including data in the self-starting information part and other registry data that may be changed by ransomware.
[0034] Specifically, the disk file data may be hash values of file paths and file contents of all files in the disk.
[0035] Preferably, if the registry data recorded in the backup database is only the data of key parts in the registry and the hash values of the file paths of al...
Embodiment 2
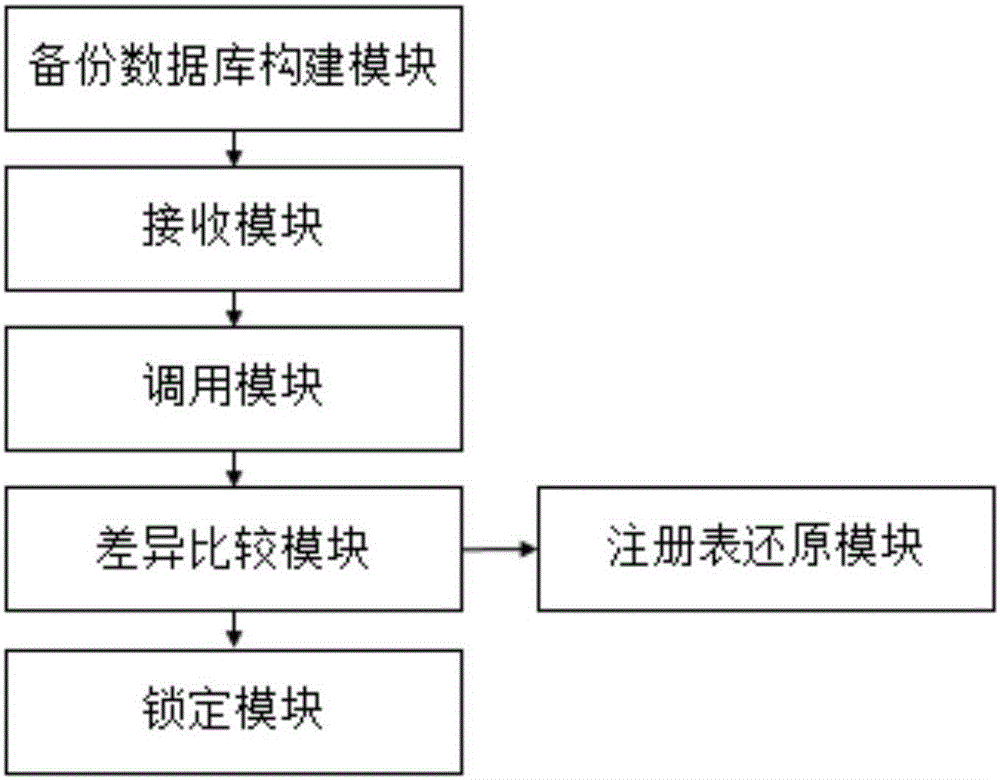
[0058] image 3 It is an optional processing system structure meaning for ransomware in Embodiment 2 of the present invention Figure 1 .
[0059] In combination with the above method, the present invention also proposes image 3 The shown processing system against ransomware includes a backup database building module, a receiving module, a calling module, a difference comparison module, a locking module and a registry restoring module.
[0060] Wherein, the backup database construction module is used to construct the backup database, wherein the backup database includes at least one restoration point and restoration data corresponding to each restoration point, and the restoration data includes registry data and disk file data.
[0061] The receiving module is used for receiving and processing requests.
[0062] The calling module is used for selecting a restore point from the backup database according to the processing request, and calling the disk file data corresponding...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com