Prime-domain multi-threshold progressive secret image preservation and reconstruction method
A secret image and prime number field technology, applied in the field of multi-threshold progressive secret image sharing and reconstruction in the prime number field, can solve the problems of being unable to resist micro-noise attacks, limited image visual regulation, and inaccuracies
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
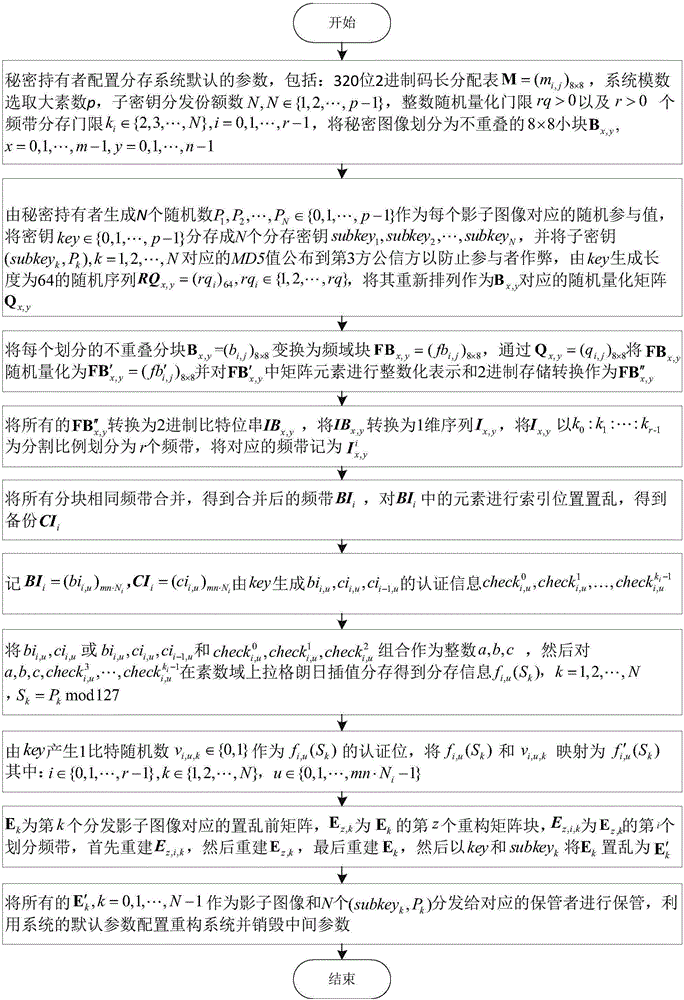
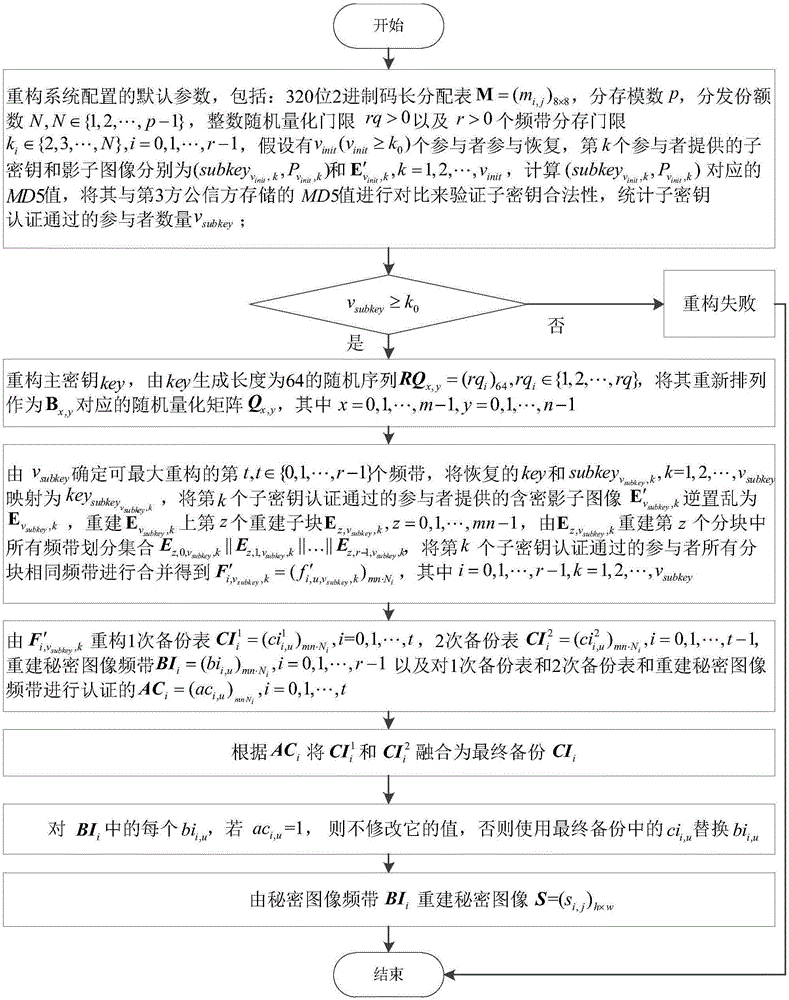
[0167] The following takes JAVA jdk1.8.0_65 as the case implementation environment, and describes the implementation of the present invention in detail in conjunction with the accompanying drawings, but is not limited to this implementation case, where figure 1 It is the flow chart of sharing storage, figure 2 Is the reconstruction flow chart. The following is a specific example to illustrate the sharing process:
[0168] Step 1: The secret holder configures the default 320-bit code length allocation table M of the sharing system, selects a large prime number p=1000000007 as the system default modulus, sets the number of subkey distribution shares N=7, and the integer random quantization threshold rq=12, r=6 sharing threshold is k 0 =3≤k 1 =4≤k 2 =5≤k 3 =6≤k 4 =7≤k 5 =7 and k 0 +k 1 +…+k 5 =32, satisfy the constraints of formula (1) and formula (2), read the secret image S=(s i,j ) 8×8 , divide it into non-overlapping 8×8 small blocks B x,y , x=0, y=0, then B 0,...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com