Wireless network authentication method and core network element, access network element, and terminal
A wireless network and access network technology, applied in the field of communication, can solve the problems of not being able to support business well and taking a long time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
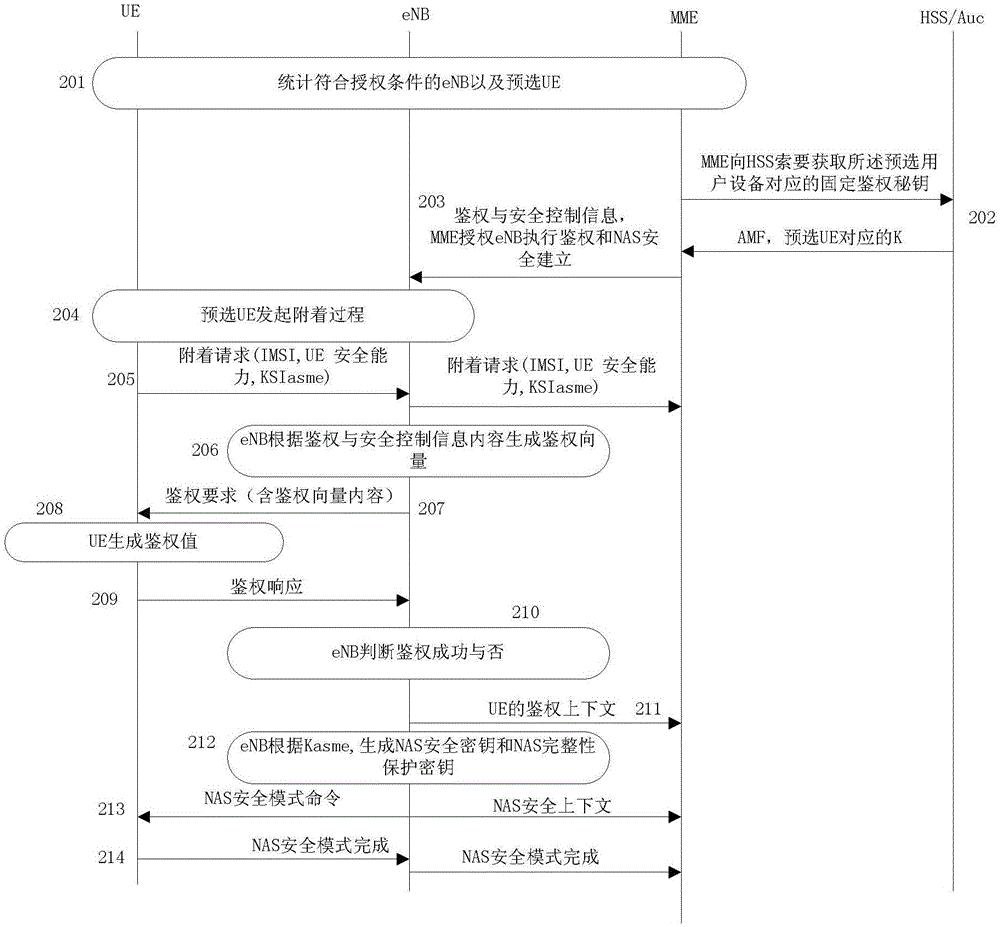
[0167] Taking the 3GPP EPC architecture combined with the LTE access network as an example, the authentication vector generator and the key derivation function KDF are loaded for the eNB (evolved base station), so that the eNB has the ability to calculate the authentication vector and generate the secret key. Such as figure 1 shown, including the following steps:
[0168] Step 201, select the eNB that meets the authorization conditions and pre-select the UE, the feasible selection methods and rules include:
[0169] The time that a UE resides in a certain eNB range exceeds the preset threshold one, and the time can be continuous or cumulative; then the UE can be used as a pre-selected UE, and the eNB can be considered to meet the authorization conditions;
[0170] If the frequency of the same UE entering the range of an eNB exceeds the preset threshold two, the UE can be used as a pre-selected UE, and the eNB can be considered to meet the authorization conditions;
[0171] T...
Embodiment 2
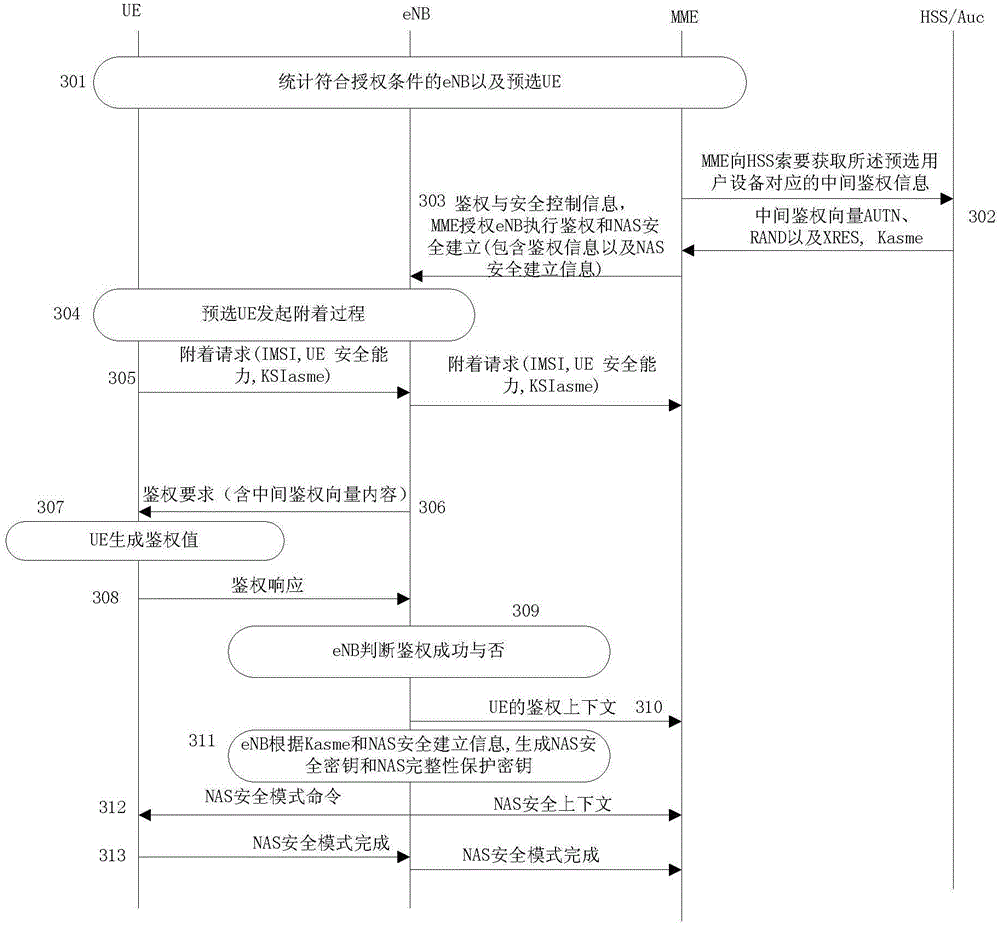
[0202] Taking the 3GPP EPC architecture combined with the LTE access network as an example, the key derivation function KDF is loaded for the eNB, so that the eNB has the ability to generate a key. Such as figure 2 shown, including the following steps:
[0203] Step 301, count the eNBs and pre-selected UEs that meet the authorization conditions, the feasible statistical methods and rules can refer to Embodiment 1, and will not be repeated here.
[0204] Step 302: The MME asks the HSS for authentication information in the HSS corresponding to the qualified pre-selected UE, specifically including: an intermediate authentication vector corresponding to the target UE; the HSS sends the authentication information to the MME.
[0205] Step 303, the MME sends authentication and security control information to the eNB that meets the authorization conditions, including:
[0206] The eNB can perform authentication authorization on the user equipment;
[0207] The eNB can execute the...
Embodiment 3
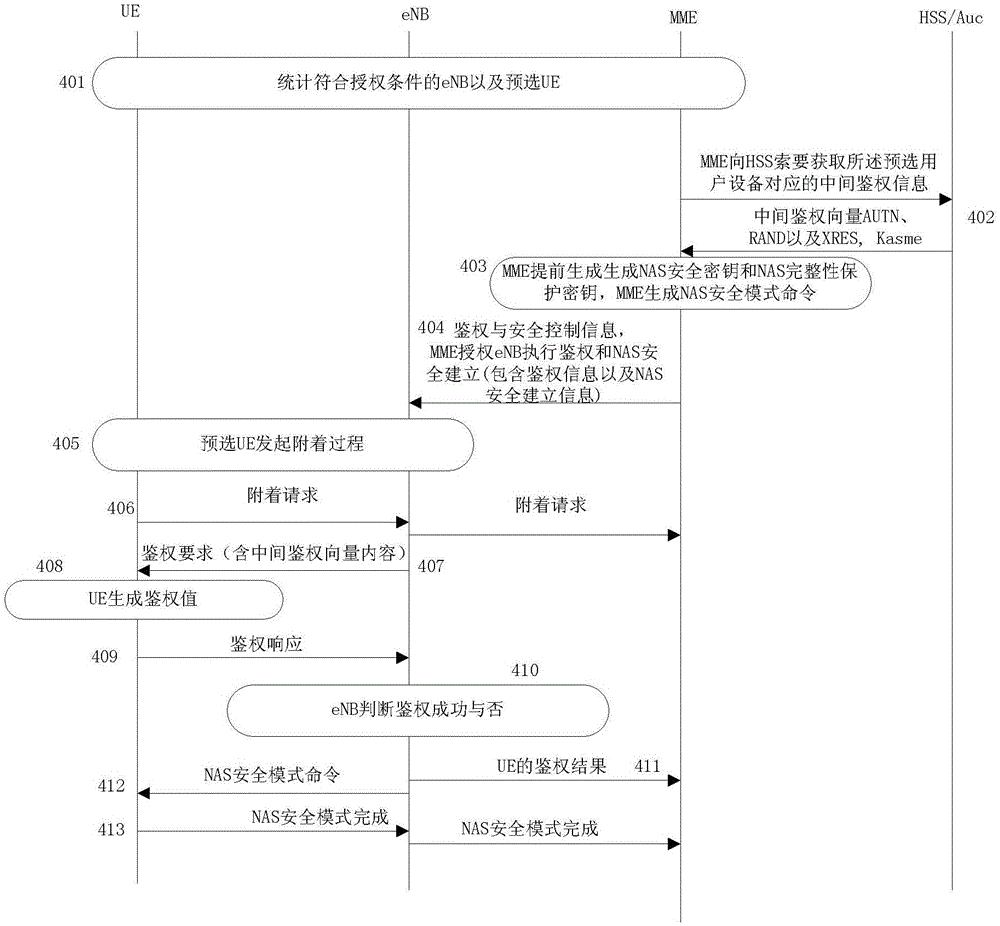
[0229] Embodiment 3 adopts the same flow process as Embodiment 2, and its difference is:
[0230] In Embodiment 2, the authentication information and NAS security establishment information in the authentication and security control information received by the eNB in step 303 may remain valid until updated or deauthorized by the MME.
[0231] In Embodiment 3, the authentication information and NAS security establishment information in the authentication and security control information received by the eNB in step 303 are only valid once, and before the next authentication of the pre-selected UE starts, the MME acquires the UE from the HSS in advance The intermediate authentication vector, MME updates the selection of NAS encryption and integrity protection algorithms to form new authentication and NAS security establishment information and sends it to eNB; eNB uses the updated authentication in the next UE authentication Information and NAS security establishment informatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com