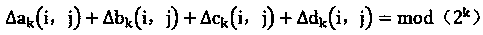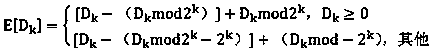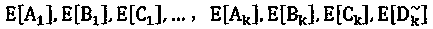Reversible watermarking algorithm of ciphertext image
An image and ciphertext technology, applied in the field of image information security, can solve problems such as high distortion, low embedding capacity, and insufficient security, and achieve the effect of strong confidentiality and high embedding capacity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0008] Below, describe the present invention in detail, its concrete implementation steps are as follows:
[0009] Step 1: Image Encryption
[0010] Images, videos and other information must be encrypted before being uploaded to the cloud. After encryption, select λ as the private key and (N, g) as the public key. The plaintext image F is encrypted, and the ciphertext image is C, assuming random large prime numbers p, q, N=p*q; λ=lcm(p-1, q-1), yes in all with N 2 coprime sets of integers, is less than N 2 The integer set of , then the encryption formula of the ciphertext image C is:
[0011] C=E[F,r]=g F r N modN 2
[0012] Step 2: High frequency DWT wavelet transform of ciphertext image
[0013] The ciphertext image is subjected to wavelet transformation with integer conditions, and the image is subjected to DWT transformation. In order to solve the decimal problem, according to the integer constraint conditions:
[0014] Δa k (i,j)+Δb k (i,j)+Δc k (i,j)+...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com