Video data security encryption transmission method and system
A technology for secure encryption of video data, applied in the field of video data secure encryption transmission methods and systems, can solve problems such as hidden safety hazards, inconvenient operation, and illegal access to sensitive data, and achieve reduced workload, high security, and high safety factor Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
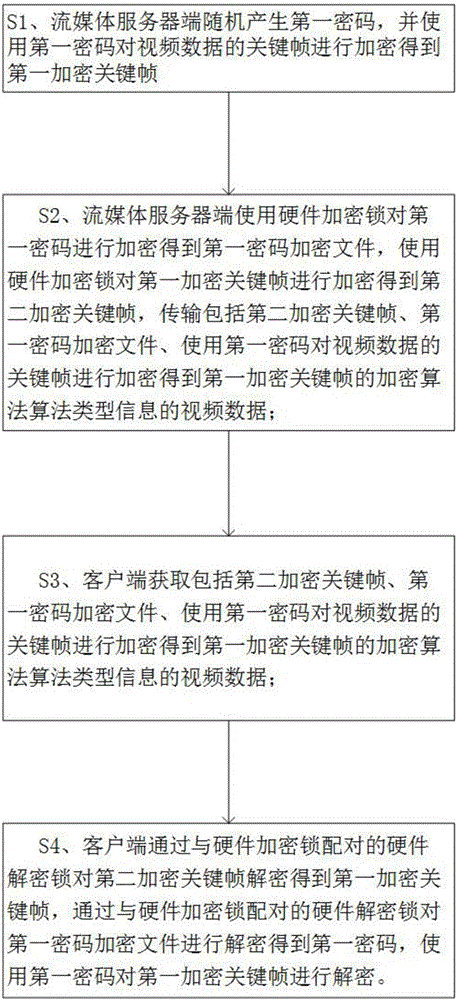
[0029] Embodiment 1: the present invention proposes a kind of video data safe encrypted transmission method, it is characterized in that, comprises steps:
[0030] S1. The streaming media server randomly generates a first password, and uses the first password to encrypt key frames of video data to obtain a first encrypted key frame;
[0031] Encrypting only key frames reduces the workload of encryption, and videos without key frames cannot be played, and good encryption effects can still be achieved.
[0032] S2. The streaming media server uses a hardware encryption lock to encrypt the first password to obtain a first password encrypted file, uses a hardware encryption lock to encrypt the first encrypted key frame to obtain a second encrypted key frame, and the transmission includes the second encrypted key frame, The first password encrypts the file, uses the first password to encrypt the key frame of the video data to obtain the video data of the encryption algorithm algorit...
Embodiment 2
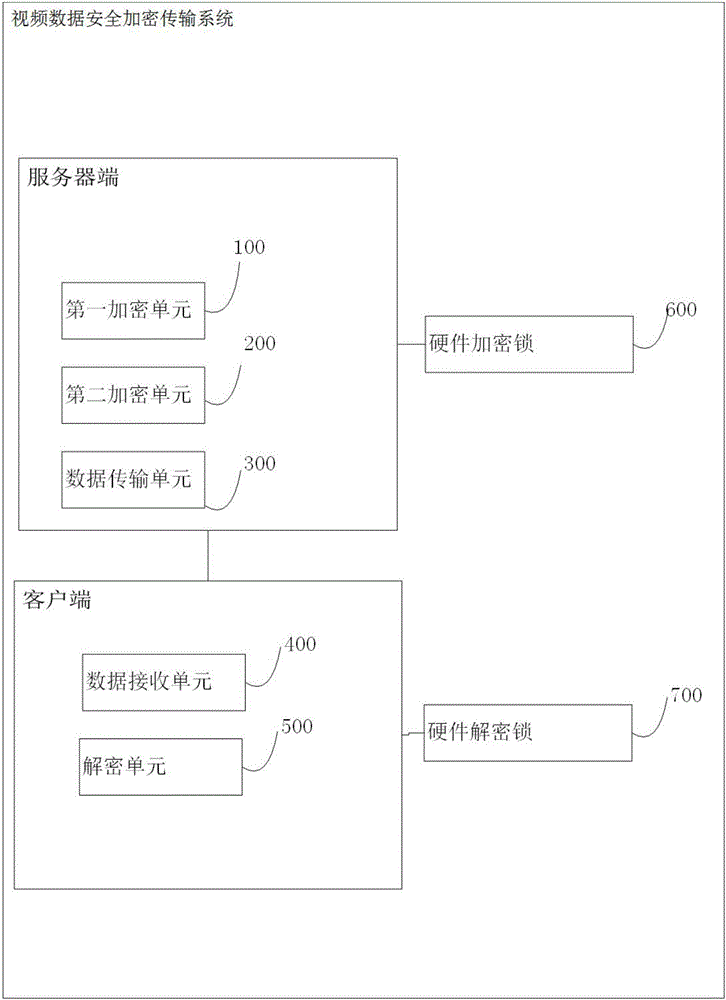
[0041] Embodiment 2: the present invention also provides a kind of video data safe encryption transmission system, comprises following unit:
[0042] The first encryption unit 100 for the streaming media server side to randomly generate the first password, and use the first password to encrypt the key frame of the video data to obtain the first encrypted key frame;
[0043]Encrypting only key frames reduces the workload of encryption, and videos without key frames cannot be played, and good encryption effects can still be obtained.
[0044] The second encryption unit 200 is used for the streaming media server to encrypt the first password to obtain the first password encrypted file by using the hardware dongle 600 , and to encrypt the first encrypted key frame by using the hardware dongle 600 to obtain the second encrypted key frame.
[0045] Using hardware encryption for the first encrypted key frame and the first password increases the security of the system. The random pas...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com