Data security control method and system based on data classification and grading
A data classification and data security technology, applied in the field of data security, can solve problems such as the discovery of abnormal behaviors in document use, the lack of data security assessment, and the lack of indexed representation of data security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] Glossary:
[0043] Windows Session, the operating system session, is composed of processes and other system objects (such as window stations, desktops, and windows), which represent a user's workstation login session.
[0044]JSON, is a lightweight data interchange format that is easy to read and write, as well as easy to machine parse and generate. JSON uses a text format that has nothing to do with programming languages, and borrows the habits of C-like languages. These characteristics make JSON an ideal data exchange format.
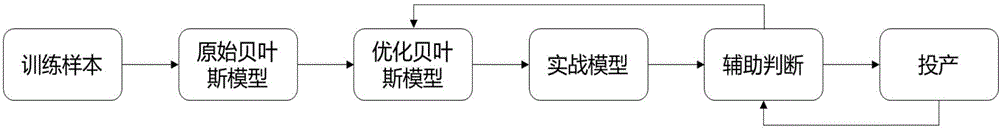
[0045] Bayes' theorem is a theorem about the conditional probability of random events A and B. where P(A|B) is the probability of A happening given B happening.
[0046] Bayesian classification is a classification method of statistics. It is a class of algorithms that use probability and statistics knowledge for classification.
[0047] Naive Bayesian algorithm is a classification method based on Bayesian theorem and the independent assumpti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com