Radius-based video monitoring platform security certification method
A technology of security authentication and video surveillance, applied in electrical components, transmission systems, etc., can solve problems such as business data theft, disallowed diffusion and dissemination, hidden dangers of platform system security, etc., to improve security, prevent intrusion, and reduce security risk effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
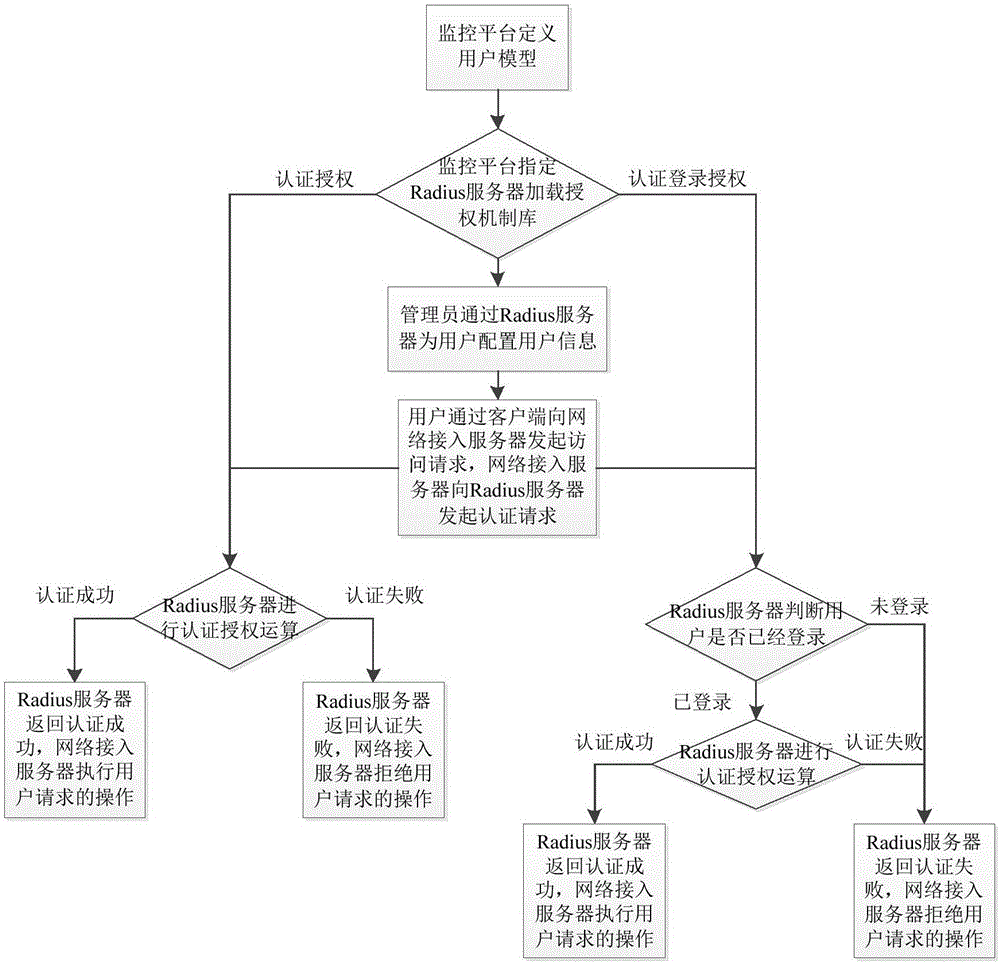
[0051] S1: The monitoring platform defines user names, passwords, roles, and management domains, and loads the authority library.
[0052] S2: The monitoring platform designates the Radius server to load the authorization mechanism library for authentication and login authorization.
[0053] S3: The administrator configures user names, passwords, roles, and management domains for users through the Radius server.
[0054] S4: The role of a user is A, and the management domain is section S. The user initiates a request to access the historical monitoring records of video source 1 to the network access server through the client, and the network access server initiates an authentication request to the Radius server. The authentication request In it, the value of the authentication authority is history browsing, and the authentication domain resource list is video source 1.
[0055] S5: The Radius server first judges whether the user has logged in; if logged in, judges whether the...
Embodiment 2
[0061] Under the user model of Embodiment 1, the monitoring platform designates the Radius server to load the authorization mechanism library for authentication and authorization.
[0062] S1: The administrator configures user names, passwords, roles, and management domains for users through the Radius server.
[0063] S2: The role of a user is A, and the management domain is section S. The user initiates a request to access the historical monitoring records of video source 1 to the network access server through the client, and the network access server initiates an authentication request to the Radius server. The authentication request In it, the value of the authentication authority is history browsing, and the authentication domain resource list is video source 1.
[0064] S3: The Radius server first judges whether the user name exists; if the user name exists, then judges whether the password matches; if the password matches, then sends an authentication request to the aut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com