Pluggable type hardware encryption storage method and system
A hardware encryption and storage system technology, applied in the field of storage information security, can solve the problems of complex cryptographic operations, insecure information storage, easy to crack encryption methods, etc., to achieve broad application prospects, ensure security, and highlight substantial characteristics. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] Below in conjunction with accompanying drawing, the present invention is described in further detail:
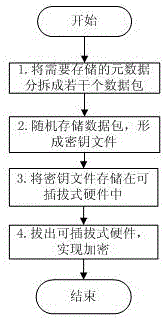
[0030] Such as figure 1 As shown, a pluggable hardware encryption storage method provided by the present invention includes the following steps:
[0031] (1) According to storage encryption requirements, the data to be stored is divided into several data packets. The higher the encryption level, the larger the number of data packets and the smaller the capacity of the data packets. In this embodiment, the metadata size is M bits, The size of each packet is m bits, and the number of splits is N; in this embodiment, M is divisible by m, so N=M / m. In other embodiments of the present invention, when M is not divisible by m, the quotient obtained is N-1, and the remaining part becomes a data packet.
[0032] (2) Mark the split data packet with a sequence number to record the order of the information in the data packet in the original data, and then randomly store the dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com