An access control voice coding and decoding system and method
A technology of speech coding and coding algorithm, which is applied in the field of access control speech coding and decoding systems, which can solve the problem that the door control lock control security access control terminal system cannot be used, and achieve the effect of improving security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
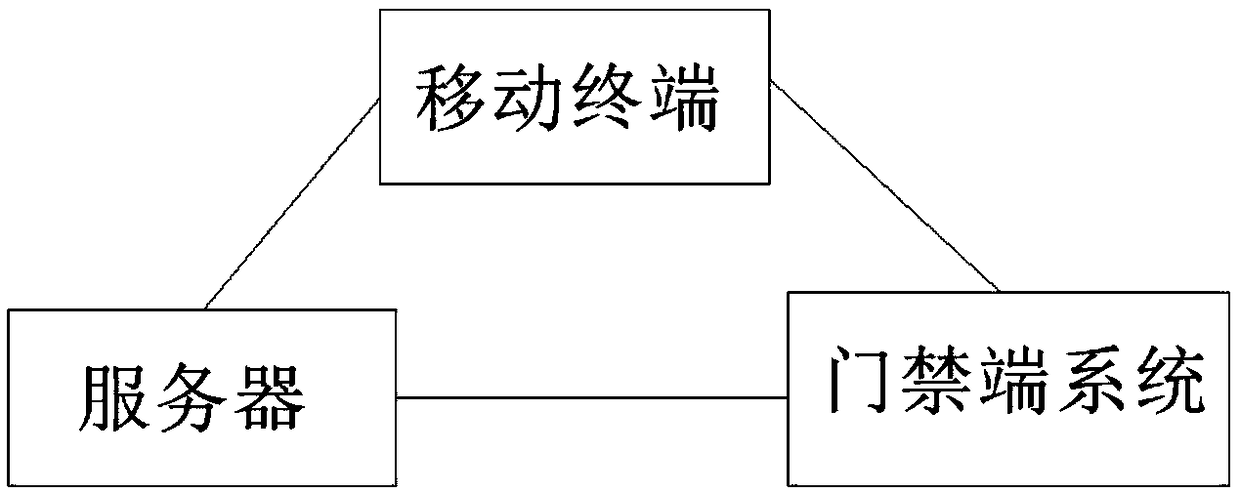
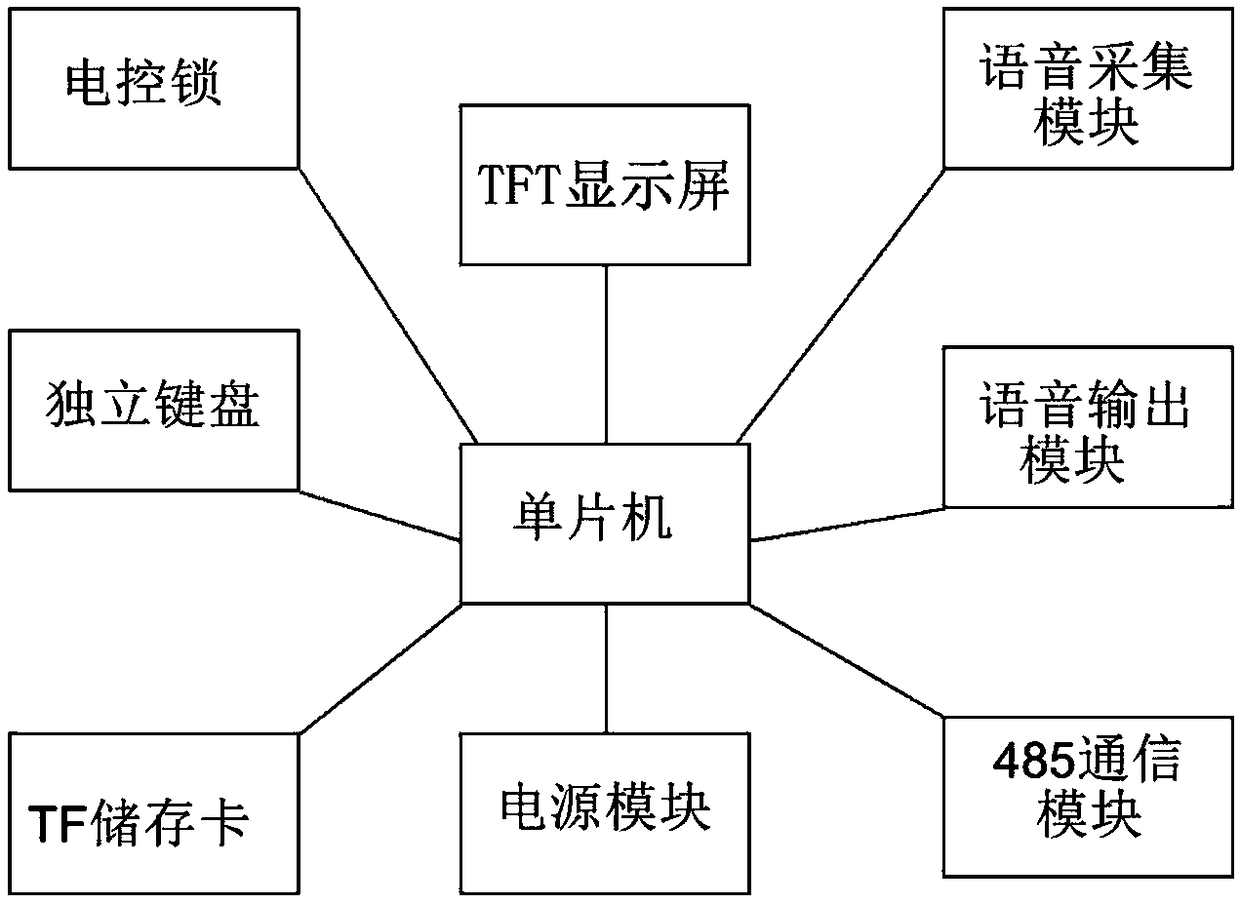
[0048] Such as figure 2 . image 3 Shown: a voice encoding and decoding system for access control, including: a mobile terminal, the mobile terminal is also connected to a server and an access control system, and the server is also connected to the access control system; the access control system includes a voice collection module, and the voice collection module is also connected to a central Processing unit, the central processing unit is also connected with 485 communication module, TF memory card and electric control lock; a further solution is: the access control system also includes an independent keyboard, power module, voice output module and TFT display; independent keyboard, power supply Module, voice output module and TFT display screen are connected with the central processing unit.
[0049] Figure 4 As shown: the central processing unit adopts Freescale's ARM processor MK60DN512; the voice output module adopts the ISD1760 voice module; the mobile terminal is a...
Embodiment 2
[0053] On the basis of the first embodiment, the function mod is a remainder function. mod((T+a1),62) means to take the remainder of the parameter (T+a1) to 62.
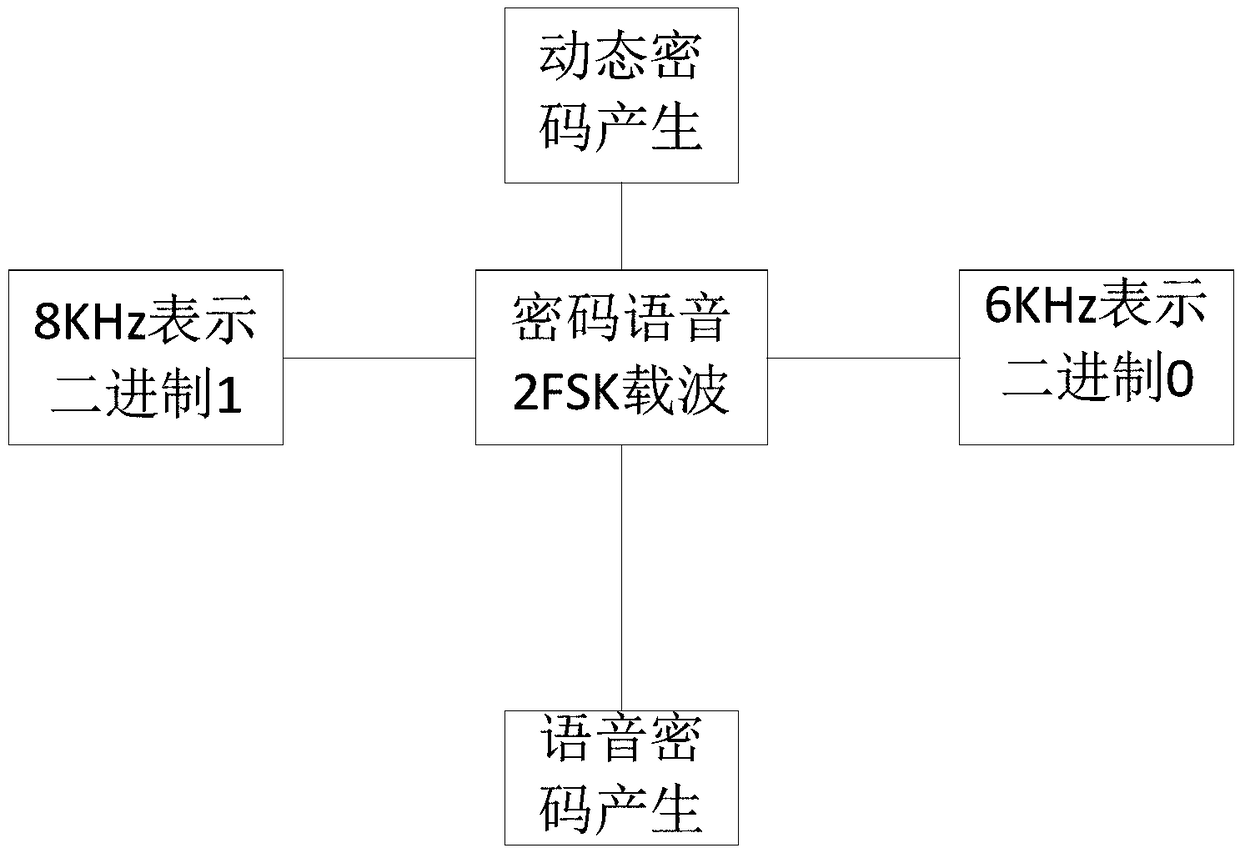
[0054] In order to prevent users from reserving the same access control on the same day to generate the same key, the key is designed as a random encryption code, and the password is composed of A+B+C+D format. Among them, A is three random numbers, B is a 6-digit date format (such as: 161108), C is the reservation access control number (the number of digits is variable), D is the login account data, each random number is 0-9, a-z , A-Z, one of the 62 characters in total, it can be precisely because of this, convert A into the ASCII code value of a 3-digit character string as the encoding variable, use the encoding variable to perform mixed encryption encoding on each digit in time B, and obtain The string X composed of 0-9, a-z, A-Z, such as: 7GmjyiOBO, followed by the access control number and user name is the initi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com