Intrusion detection method by use of improved self-organizing feature neural network clustering algorithm
A clustering algorithm and neural network technology, applied in the field of machine learning and intrusion detection, intrusion detection, can solve the problem of neuron position deviation and reduce the possible effect of human control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
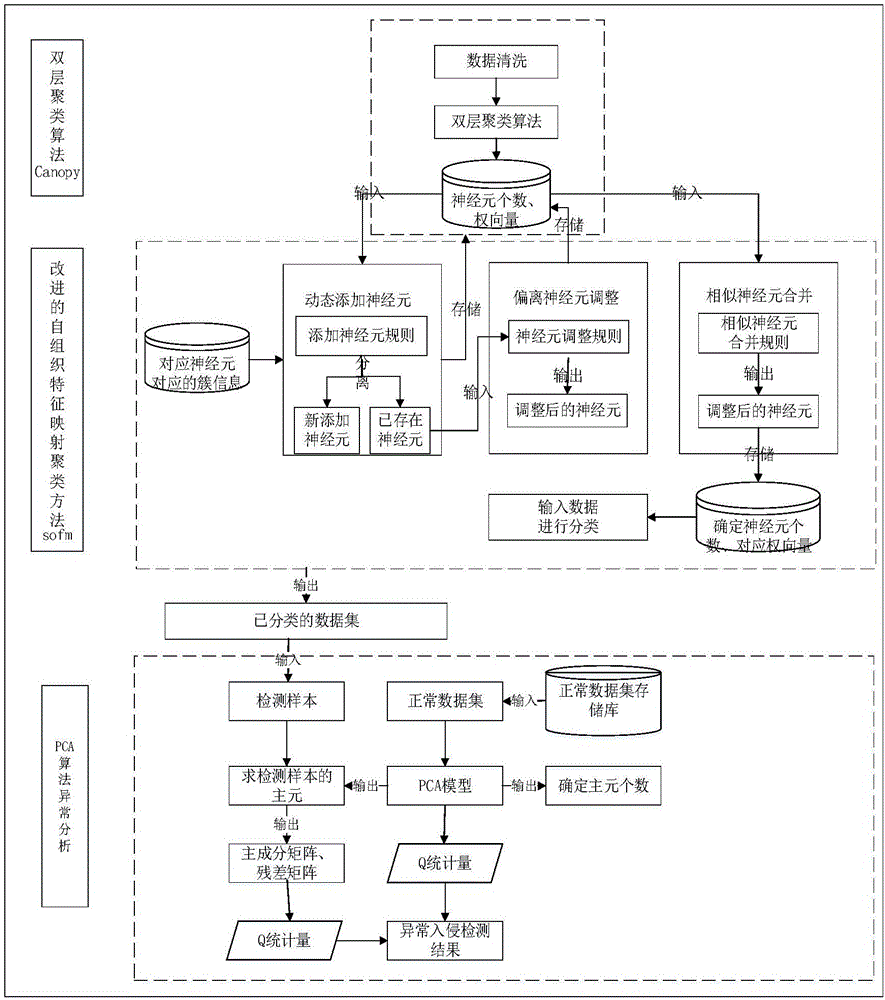
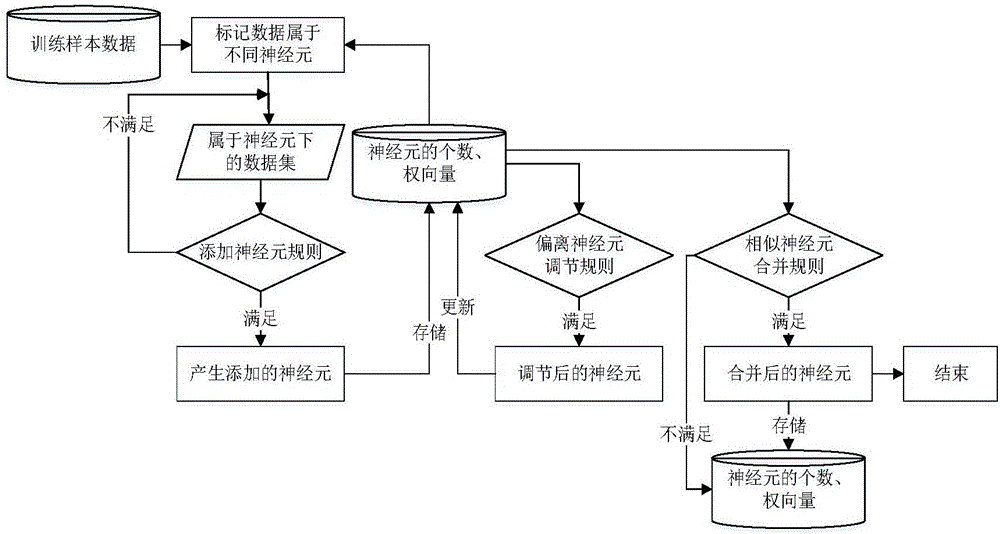
[0020] Such as figure 1 As shown, the present invention provides a kind of intrusion detection method that adopts improved self-organizing feature neural network clustering algorithm to comprise: by data cleaning, two-level clustering algorithm (Canopy) and improved self-organizing feature mapping neural network clustering method (SOFM) and abnormal intrusion detection, as follows:
[0021] 1.1 Data cleaning
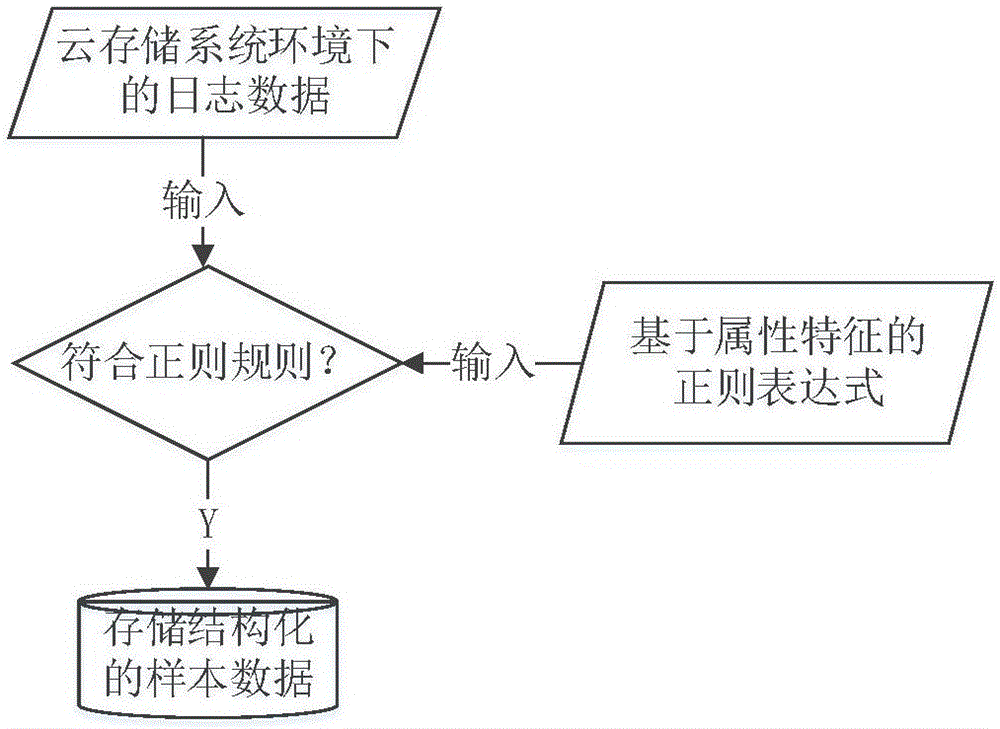
[0022] Such as figure 2 As shown, the data to be detected comes from log files in the cloud storage system environment. For unstructured log files, data structure initialization processing is required here to make the data to be detected meet the input format. The algorithm description is shown in Algorithm 1.
[0023] Algorithm 1. Data cleaning algorithm description
[0024] Input: the log file log_file.txt under the cloud storage system, the regular expression reg for extracting feature attributes
[0025] Output: structured training data dataSet
[0026] 1. Tra...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com