Network intrusion detection method based on double adaptive regularization online extreme learning machine
An extreme learning machine and intrusion detection technology, applied in the field of machine learning, can solve problems such as lowering efficiency, difficulty in satisfying real-time intrusion detection, and difficulty in detecting malicious intrusions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
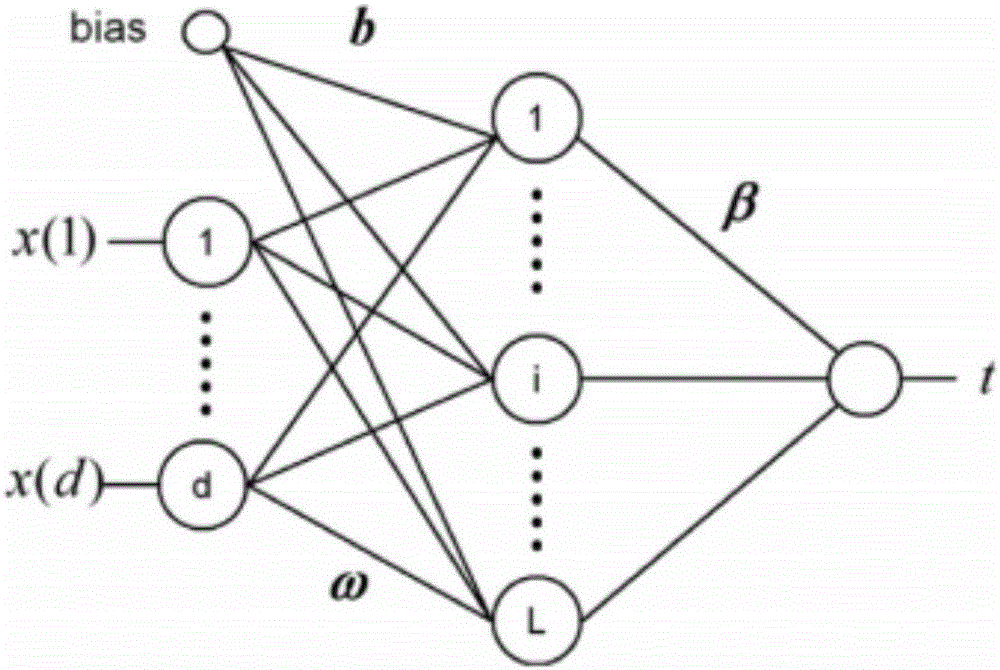
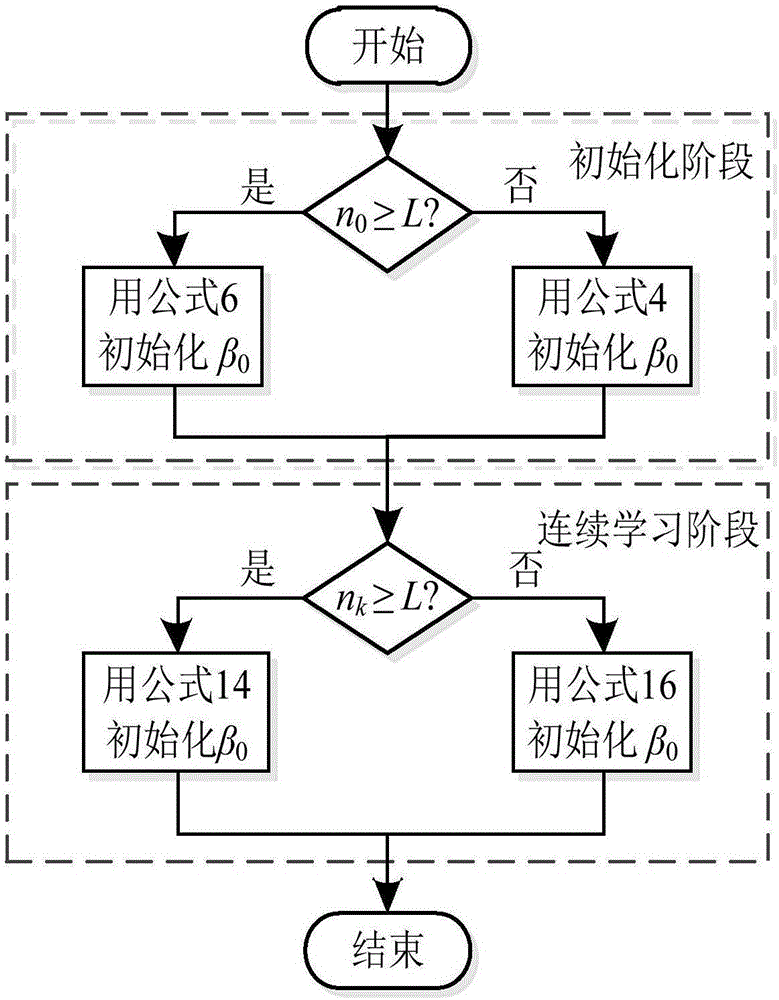
[0060] This embodiment is divided into two parts: training and detection. Training is to train an extreme learning machine classifier using a labeled network data set, and detection is to use a trained classifier to detect network intrusion data in the data to be detected.
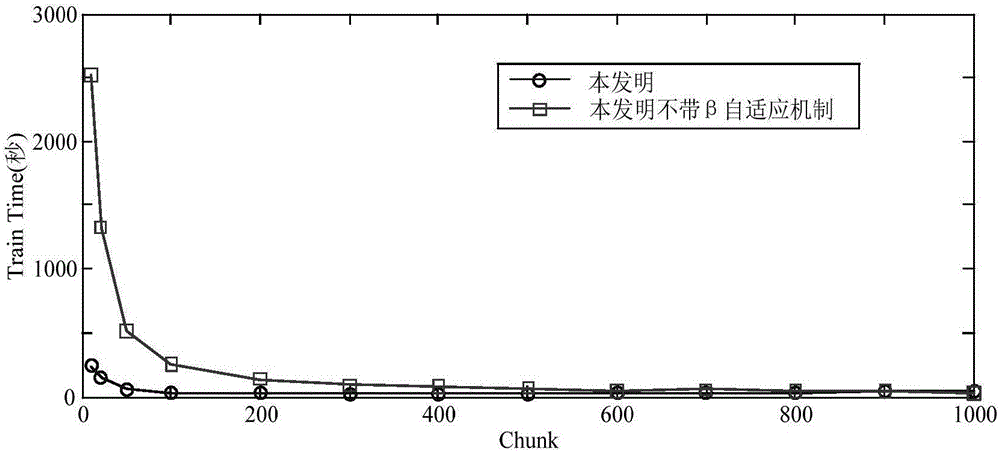
[0061] The effectiveness of the present invention is illustrated by simulating the training and detection process on the NSL-KDD data set. The NSL-KDD data set is an improved version of the famous KDD network data set. This data set deletes redundant data in the KDD data set, so the classifier will not be biased towards more frequent data, and the training set and test set data are more reasonable , So that the data set can be fully utilized. The KDD data set is the network data set used in the KDDCUP competition held in 1999. Although it is a bit old, the KDD data set is still the de facto benchmark in the field of network intrusion detection, laying the foundation for the research of network intrusion detec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com