Business risk assessment method and device, and risk control system
A technology of risk assessment and risk assessment model, which is applied in the fields of devices, risk control systems, and business risk assessment methods, can solve problems such as difficult simultaneous judgment, manual experience, time-consuming and labor-consuming, etc., to improve generalization ability and processing efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] In order to make the above objects, features and advantages of the present invention more comprehensible, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
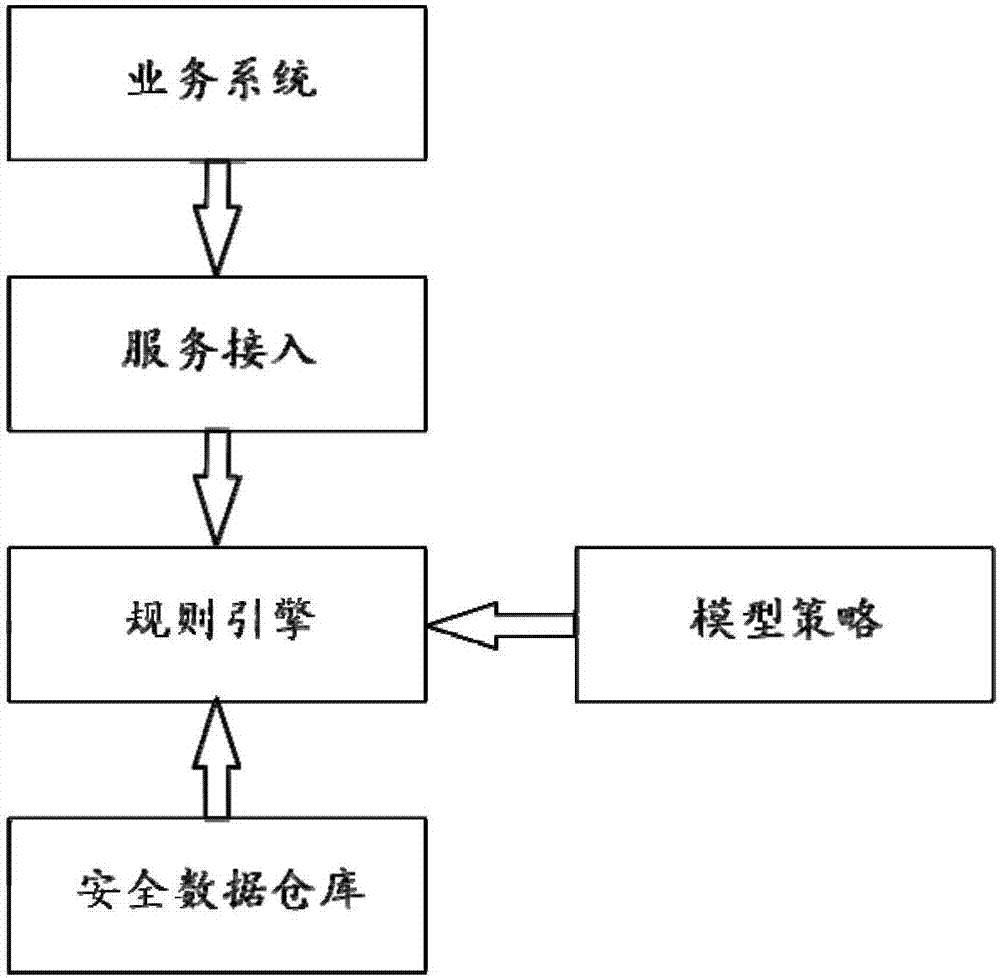
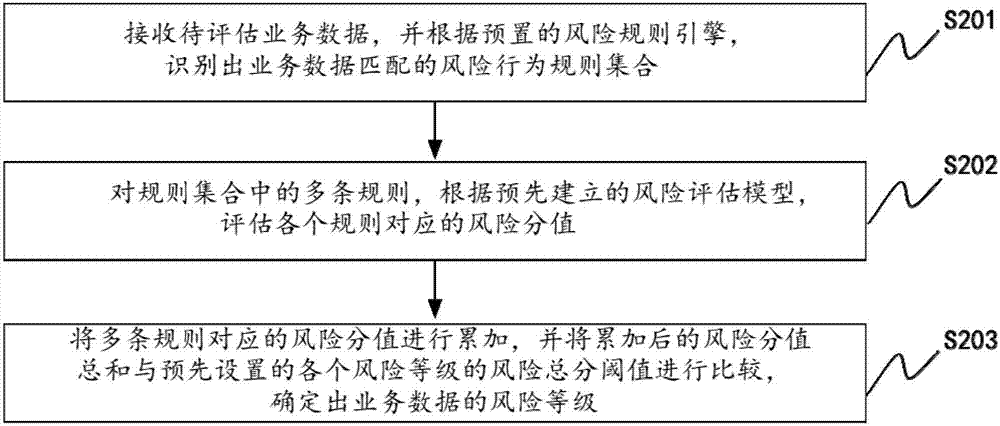
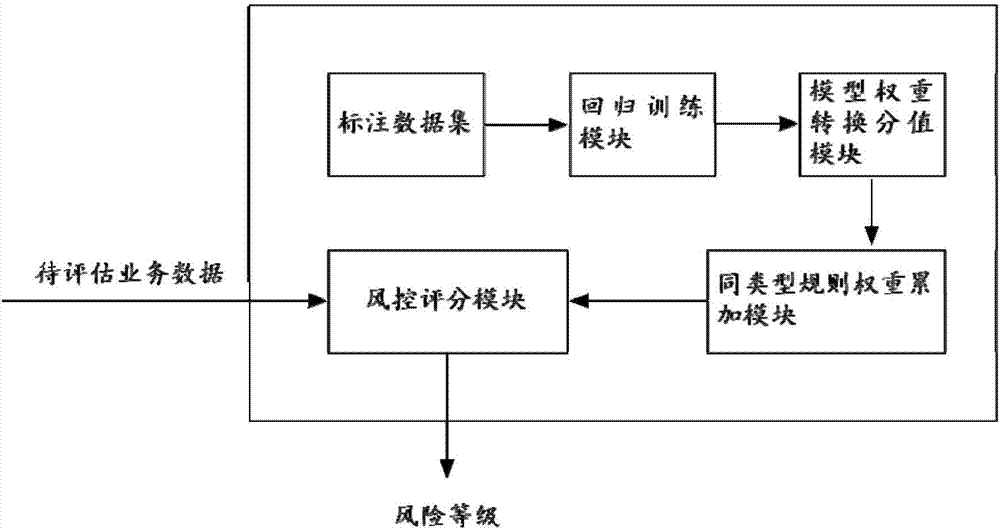
[0029] The embodiment of the present invention proposes a business risk assessment method based on weight accumulation, aiming at the difficulty of making full use of all triggered rule information in the existing risk control system, and the time-consuming and labor-intensive manual setting of rule priority. For example, this method first trains the data obtained by the existing risk control system through the logistic regression algorithm to obtain the model weight, and then converts the model weight into the sub-rule score in the form of weight accumulation according to the risk level of each sub-rule, that is, The low-level scores of the same type of rules are added to the high-level to ensure that the high-level scores of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com