Method and device for image authentication
An image and authentication technology, applied in the field of image authentication, to achieve the effect of improving the level, optimizing blind spots, and satisfying real-time detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] Below, in conjunction with accompanying drawing and specific embodiment, the present invention is described further:
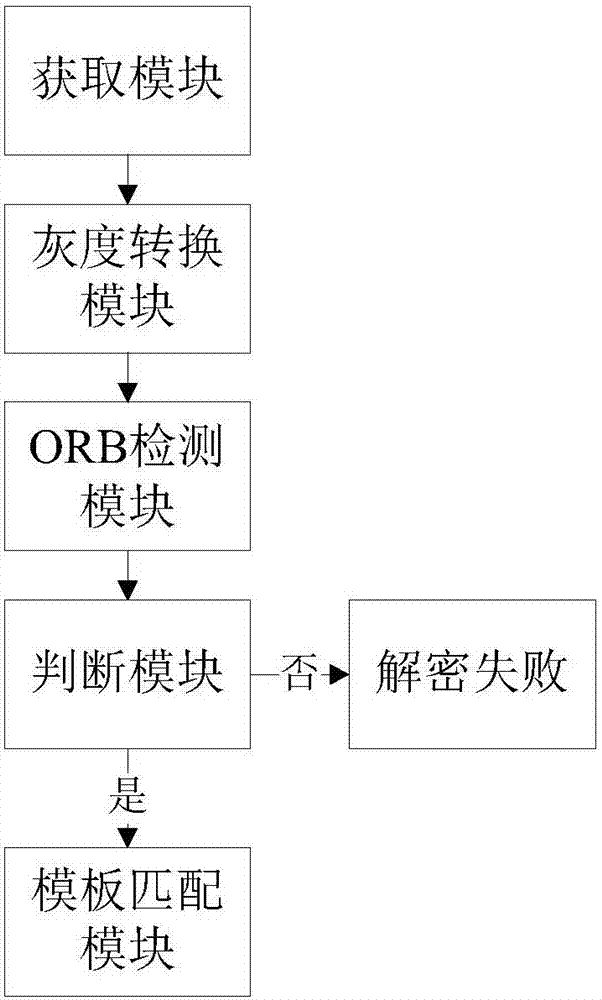
[0051] like figure 1 As shown, the present invention provides a method for image authentication, comprising the following steps:
[0052] S1: Acquire matching images and image keys; before performing the program work of the present invention, an image needs to be set as the image key first, and the image format is the mainstream format png or jpg; the image can be stored in the computer or mobile terminal Locally, or it can be saved on the server or cloud, and the security of the transmission process and transmission channel needs to be ensured when saving on the server; when performing image authentication, you can call the system album or camera of the computer or mobile terminal to obtain the decrypted image The original image, the original image is the matching image mentioned in the embodiment of the present invention, the original image can be se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com