Data traffic monitoring method for cloudstack
A monitoring method and data flow technology, applied in the field of cloud computing, can solve the problems that traditional information security is difficult to deal with, and achieve the effect of easy deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The technical solution of the present invention will be specifically described below in conjunction with the accompanying drawings.
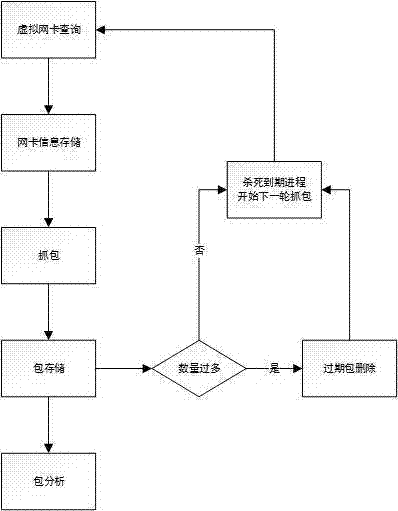
[0017] The present invention provides a cloudstack-oriented data flow monitoring method, which is deployed on each Hypervisor cluster host of the cloudstack, and calls the packet capture tool in the form of a script file for 24 hours for all virtual network cards on each host Uninterrupted automatic packet capture, and the packet is stored in a folder in a unified command format, so as to monitor the data traffic at the virtual network card level on the cloudstack.
[0018] Furthermore, in the cloudstack network architecture, CloudStack designs management, public, customer, and storage networks according to different types of data traffic. When a virtual machine needs to access the Internet or an external network, it needs to go through the public network; when the end user runs the virtual machine instance created by CloudStack, guest tr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com