User authentication method and device
A technology for user verification and user acceptance, applied in the field of user verification and devices
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
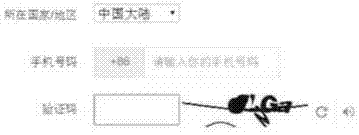
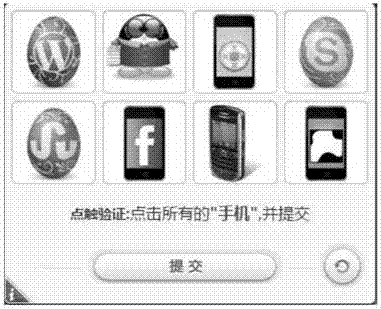
[0069] The present application provides a user verification method, which is generally applied in the environment of user verification. Due to the complexity of today's network environment, there may be many machine behaviors in the complex network environment. In order to prevent the impact of machine behavior on the network environment, verification methods are generally set to avoid machine behavior, and this verification method generally allows natural persons to simply and easily pass. Therefore, the method provided in the embodiment of the present application takes the essential difference between a natural person and a machine as the identification object. A natural person can perform thinking activities on the identified things on the basis of recognition, and judge a certain thing based on the thinking activities, while a machine It can perform recognition actions, but it cannot perform thinking activities. Therefore, the machine's cognition of things is limited to th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com