A method and system for access control authorization management based on credit information system
A technology of authorization management and access control, which is applied in the direction of transmission system, digital transmission system, data exchange network, etc., can solve the problems of unreasonable management, single authority level and irresponsibility of maintenance staff, so as to reduce operation management cost and manage reasonable effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
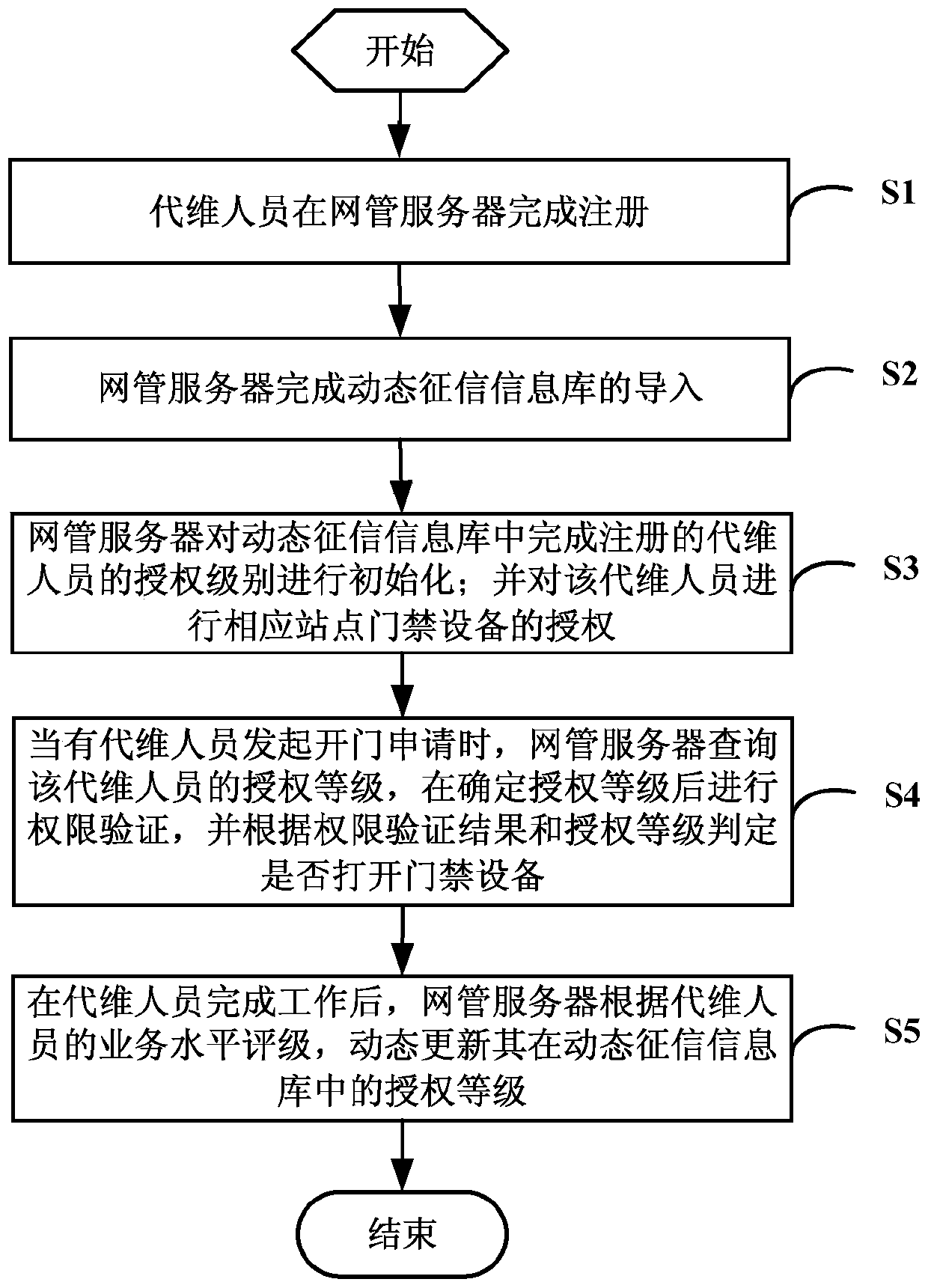
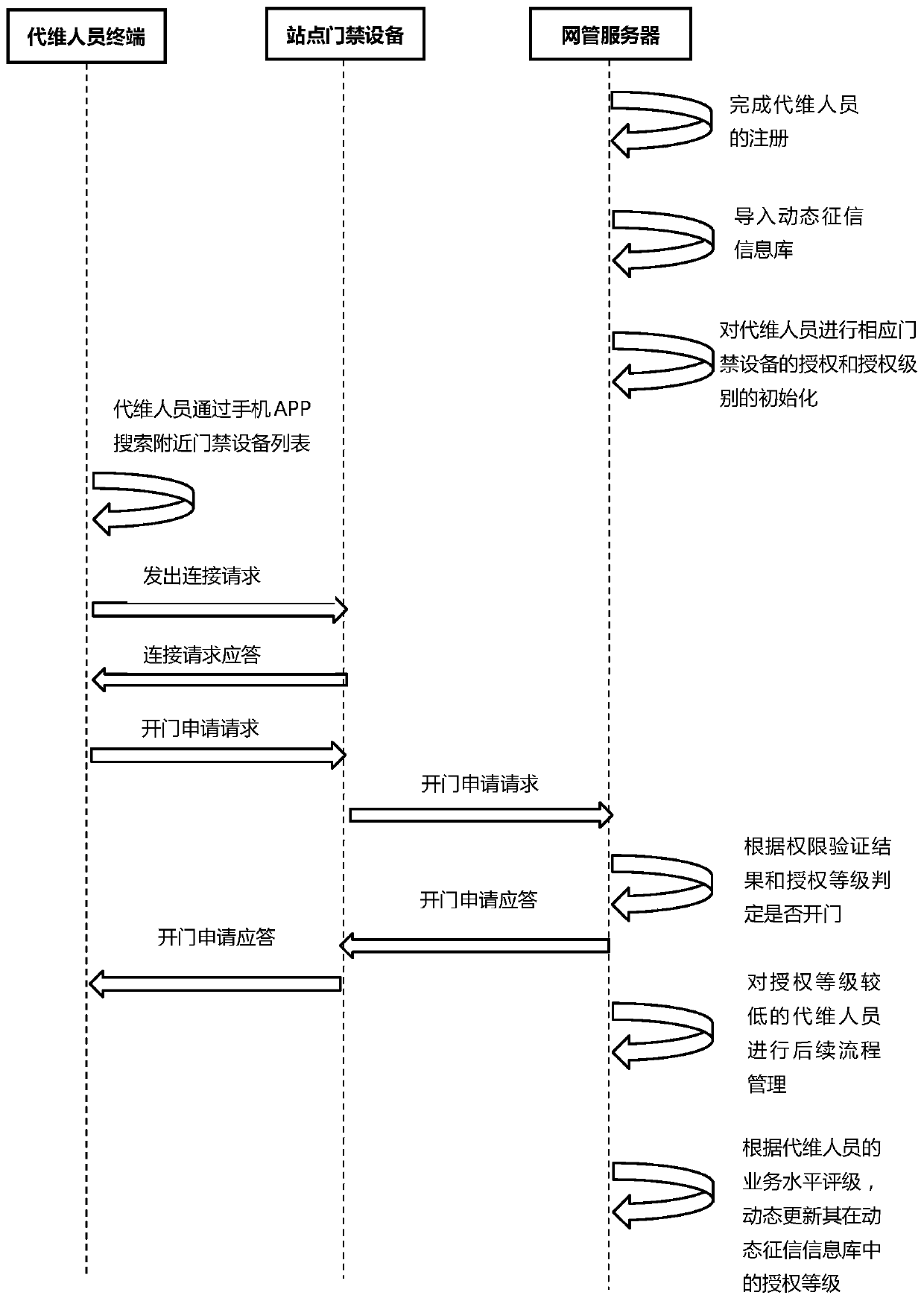
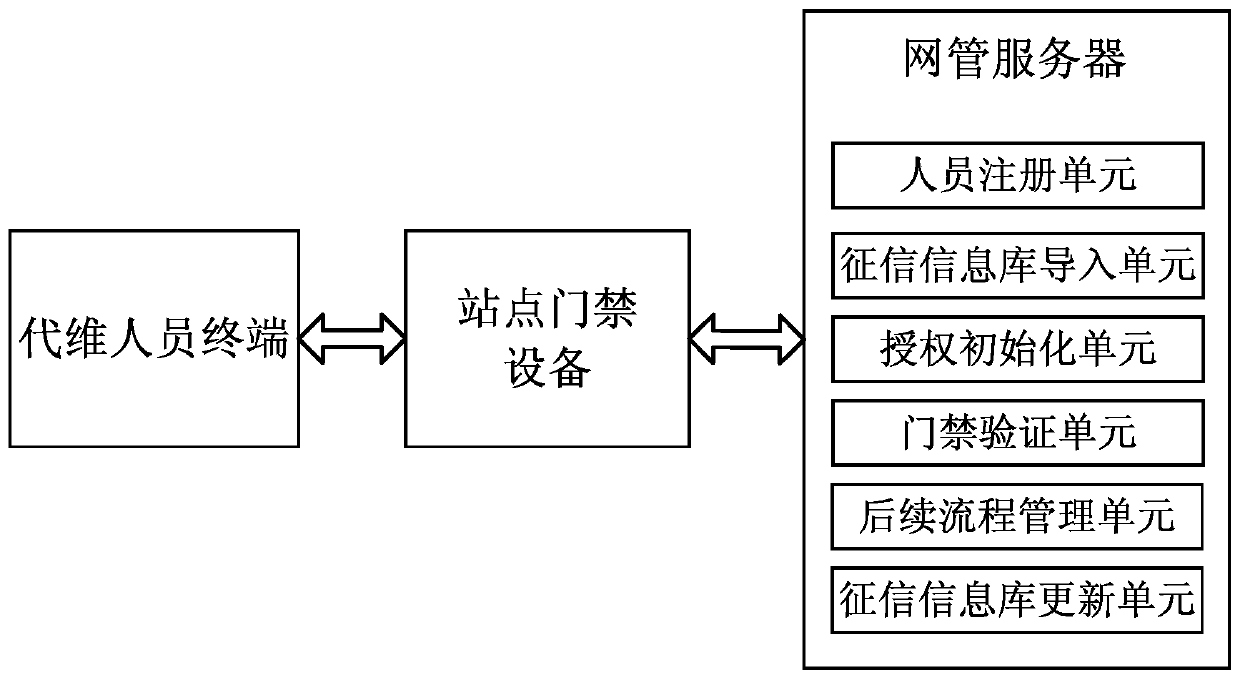
[0026] see figure 1 and figure 2 As shown, the embodiment of the present invention provides a method for access control authorization management based on the credit investigation system, including the following steps:
[0027] Step S1: The maintenance agent completes the registration on the network management server.
[0028] Step S2: The network management server completes the import of the dynamic credit information database. The dynamic credit information database is used to record the authorization level corresponding to each maintenance agent. The level of authorization determines the level of authorization authority of the maintenance personnel, which can be The upper limit of authorized access control and the length of validity period.
[0029] In this embodiment, the authorization levels are divided into three types: 1. Good level: indicates that the maintenance agency has good credit, no accidents and high customer satisfaction; 2. Normal level: indicates that the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com