Continuous encryption physical layer secure transmission method based on polarization code construction
A technology of physical layer security and transmission method, which is applied in the direction of transmission modification based on link quality, security device, transmission system, etc., can solve the problems of unreachable information transmission rate and weak information transmission capability, and achieve improved spectrum utilization, The effect of increasing the transmission rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments.
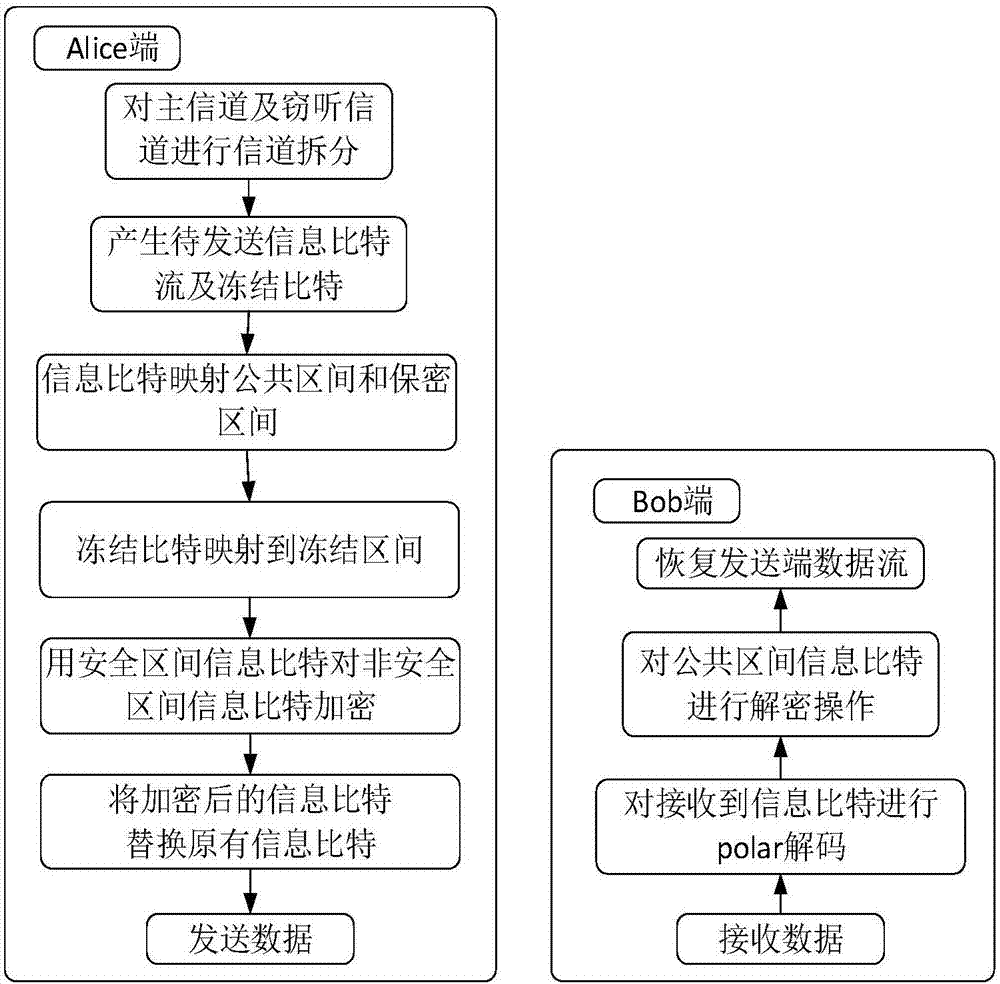
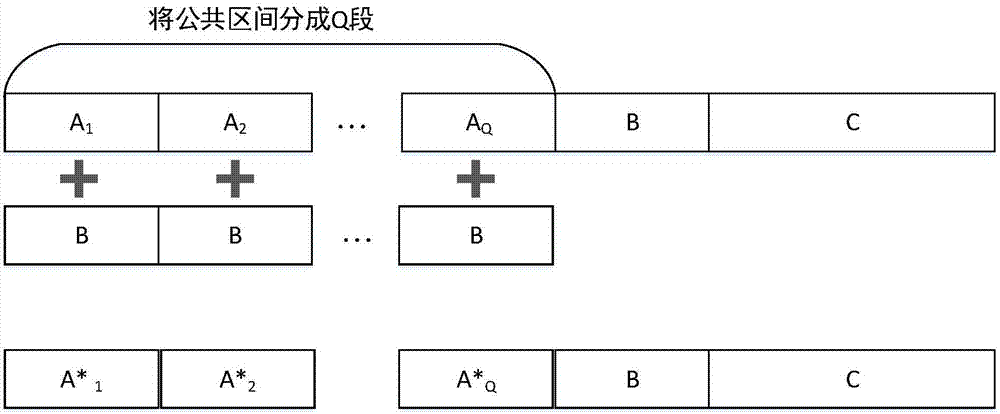
[0029] figure 1 It is a flow chart of realizing the continuous encryption method. The sending end encrypts the public interval by utilizing the security of data transmission in the safe interval, so that the proportion of polar code information bit sub-channels in all polar sub-channels becomes larger, which can enhance The frequency band utilization rate increases the transmission rate, and the receiving end restores the signal through decoding and demapping.
[0030] The following describes how to apply the present invention in combination with specific implementation steps, how to improve system reliability and increase transmission rate under the premise of ensuring safety by constructing polar codes:
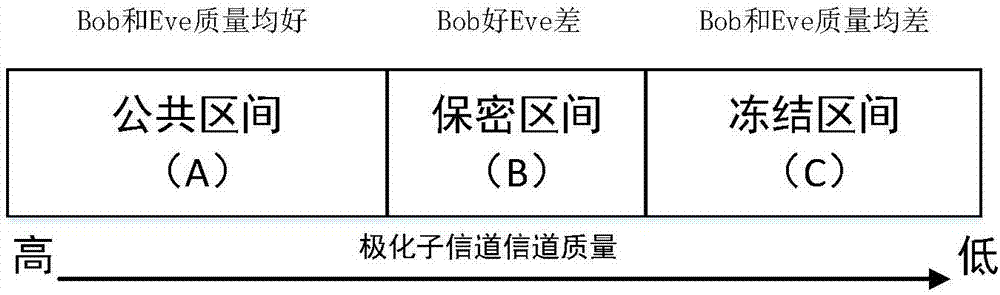
[0031] Step 1: Perform polarization operation on the main channel and the eavesdropping channel to obtain N sub-channels, and divide the N...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com