Linux-Kernel associated CVE (Common Vulnerabilities and Exposures) intelligent prediction method based on machine learning
A technology of machine learning and intelligent prediction, applied in the fields of computer software and information technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] Below in conjunction with accompanying drawing, the present invention will be further described through embodiment.
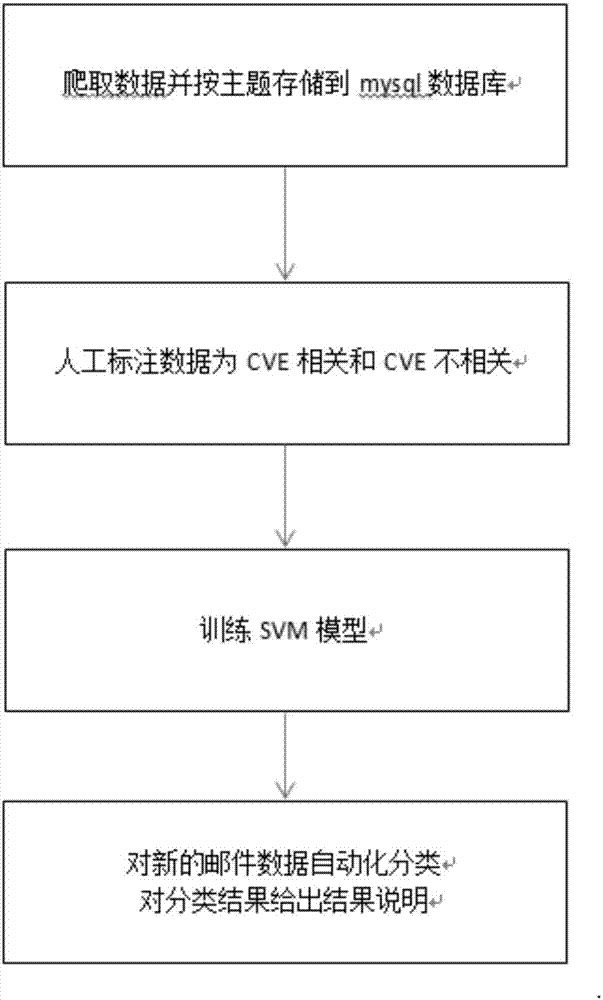
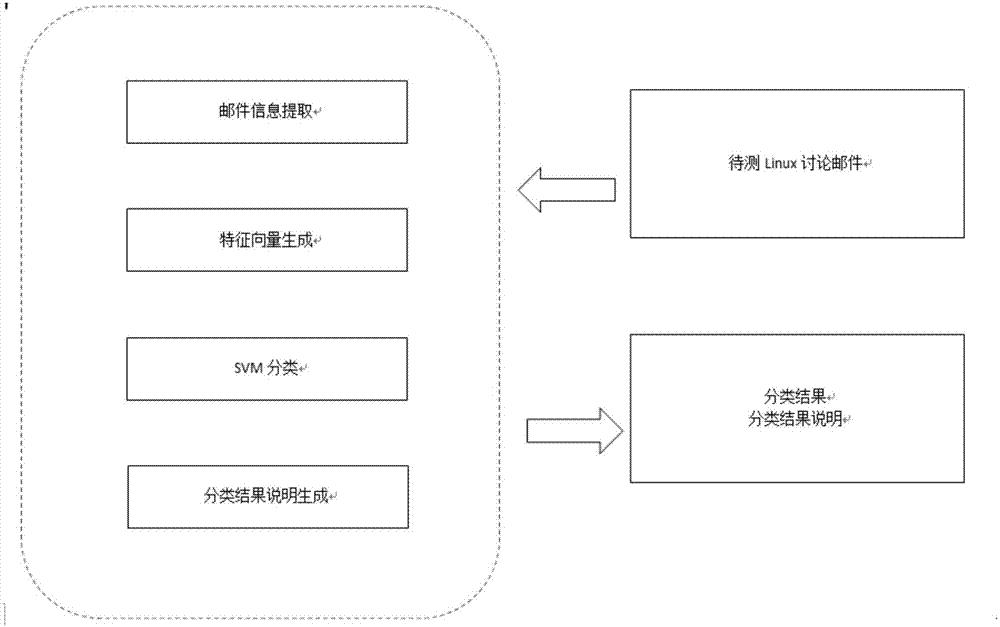
[0026] The Linux-Kernel correlation cve intelligent prediction method based on machine learning of this embodiment, its overall process is as follows figure 1 As shown, each processing module is as figure 2 As shown, the method mainly includes the following steps:
[0027] 1) Crawl the Linux discussion email data, and manually mark it as CVE-related and CVE-irrelevant
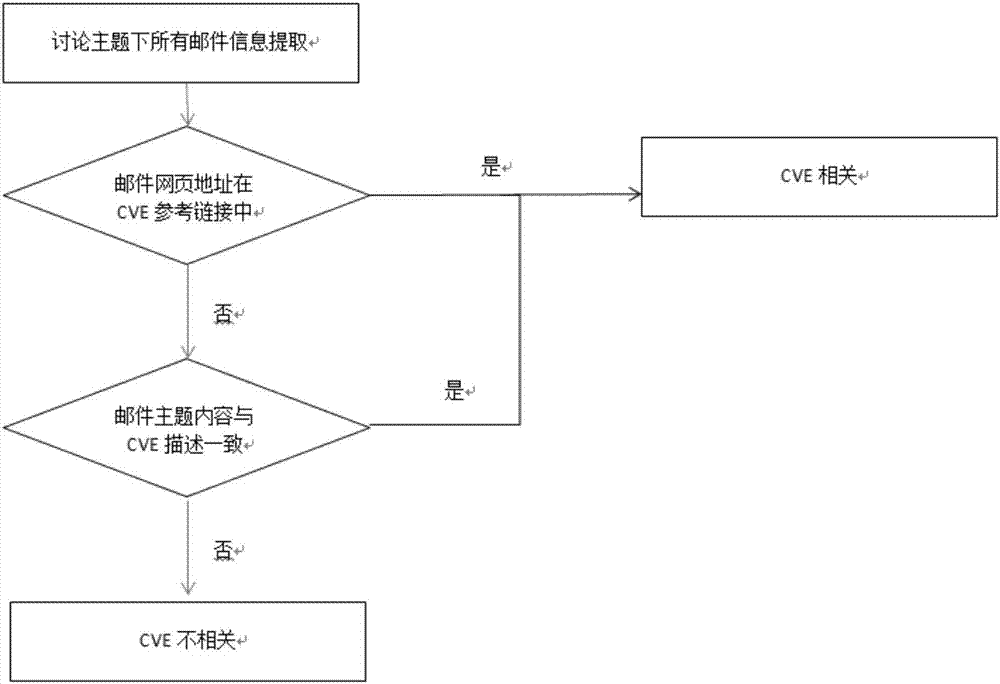
[0028] Specifically, manually mark the crawled Linux discussion email data to form a training data set. The steps are as follows: image 3 As shown, the specific description is as follows:
[0029] 1a) Extract the title, sender, sending time of all emails under the discussion topic, keyword extraction of email content, interval time between replies, and the webpage link where the email is located, and turn to 1b).
[0030] 1b) Determine whether the web page link where the email is lo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com