Encryption storage method for tampering-resistant files
A technology of encrypted storage and encryption algorithm, which is applied in the direction of public key, electrical components, and digital data protection of secure communication, which can solve problems such as server throughput bottlenecks, meet file storage requirements, meet high security requirements, and improve The effect of sensitivity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] Through the following description of the embodiments, it will be more helpful for the public to understand the present invention, but the specific embodiments given by the applicant cannot and should not be regarded as limitations on the technical solutions of the present invention, any components or technical features Changes to the definition and / or formal but not substantive changes to the overall structure should be regarded as the scope of protection defined by the technical solutions of the present invention.
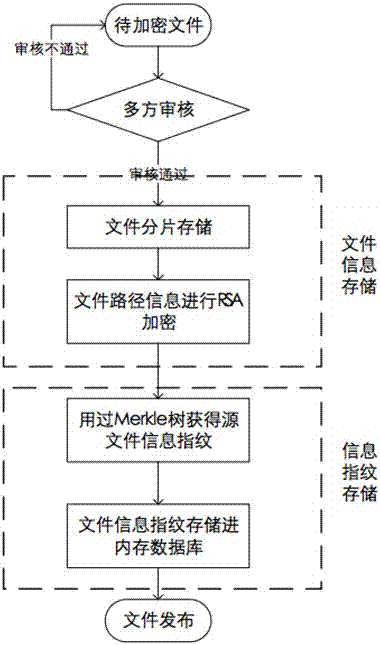
[0017] The present invention mainly provides a new distributed encrypted tamper-proof storage strategy, which improves the sensitivity to tampered data from file information storage and an information fingerprint storage. At the same time, the operation authority control of the file adopts the method of partial signature.
[0018] First of all, before uploading the file to be encrypted to the distributed storage system, a user multi-signature authentication...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com