Cloud computing environment intrusion detection system configuration and method thereof
An intrusion detection system and cloud computing environment technology, applied in transmission systems, electrical components, etc., can solve problems such as low detection performance, architectural redundancy, and potential security risks, and achieve the effect of simplifying user interface and reducing the amount of calculation.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
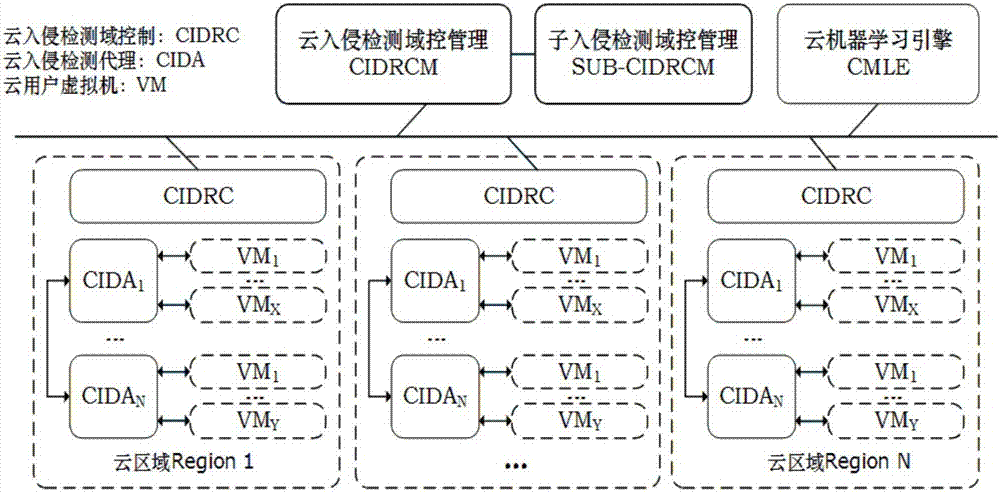
[0072] In order to solve the existing problems introduced in the background technology, the present invention provides a cloud computing environment intrusion detection system architecture. The system framework of the present invention is designed from four aspects of distribution, scalability, real-time and self-adaptability, effectively reducing various risks that may occur in the cloud computing environment, continuously learning for new types of attacks, and improving security technology while improving Quality of Cloud Services.
[0073] In order to achieve the above object, the present invention adopts the following technical scheme:
[0074] Such as figure 1 as shown,
[0075] A cloud computing environment intrusion detection system architecture CIDaaS, the system architecture CIDaaS includes:
[0076] Cloud intrusion detection proxy layer, the cloud intrusion detection proxy layer is set at the virtual machine level, and is used to provide accompanying monitoring se...
Embodiment 2
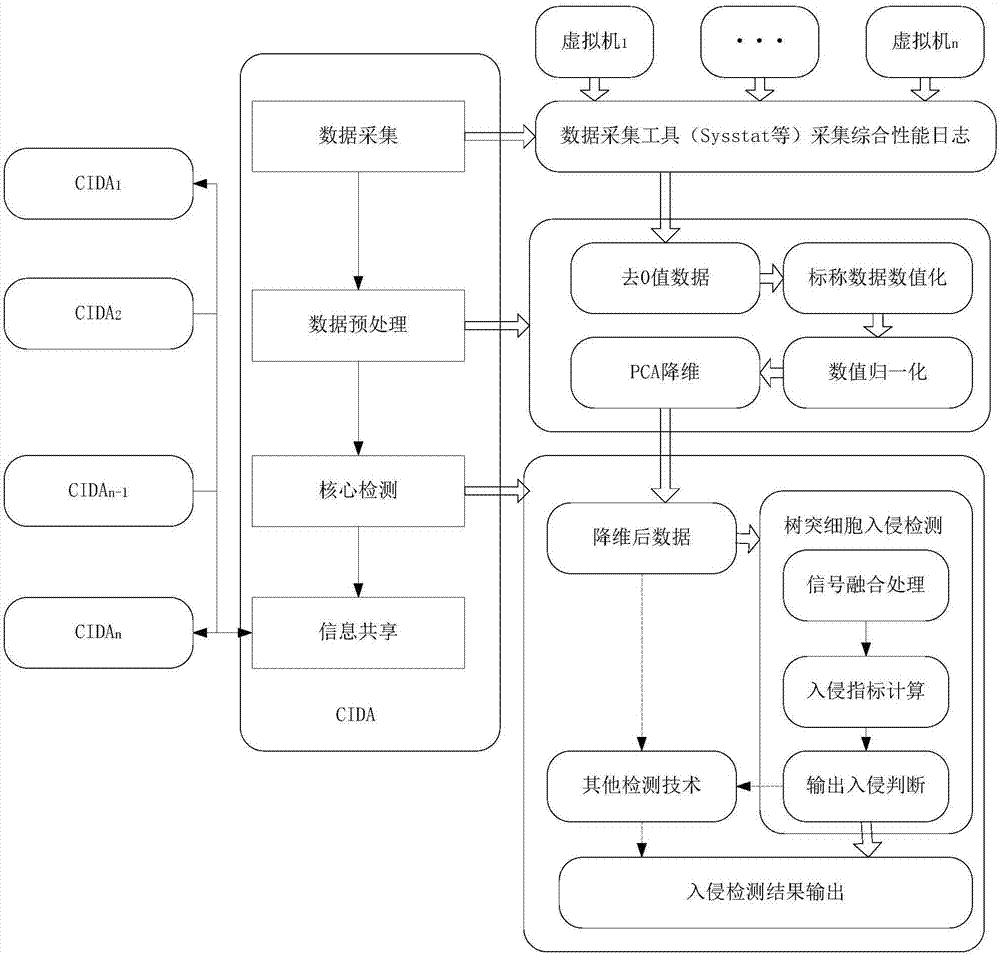
[0101] In order to solve the problem of intrusion detection of abnormal conditions in a dynamic and changeable cloud environment, the present invention provides an intrusion detection method for a cloud computing environment. The intrusion detection method is based on the above-mentioned intrusion detection system architecture for a cloud computing environment CIDaaS.
[0102] In order to achieve the above object, the present invention adopts the following technical scheme:
[0103] Such as figure 2 As shown, the cloud computing environment intrusion detection method is executed in the cloud intrusion detection agent module CIDA,
[0104] A cloud computing environment intrusion detection method, the method comprises the following steps:
[0105] (1) Data collection: use the Sysstat tool to collect the comprehensive performance log of the cloud computing environment of the virtual machine VM, and unify the collection format during the collection process;
[0106] (2) Data pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com