Website risk value evaluation method and device based on cloud protection and cloud monitoring system
A monitoring system and value-at-risk technology, applied in the field of network security, can solve problems such as inability to comprehensively monitor website security, and no solutions are proposed, so as to achieve the effect of information sharing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
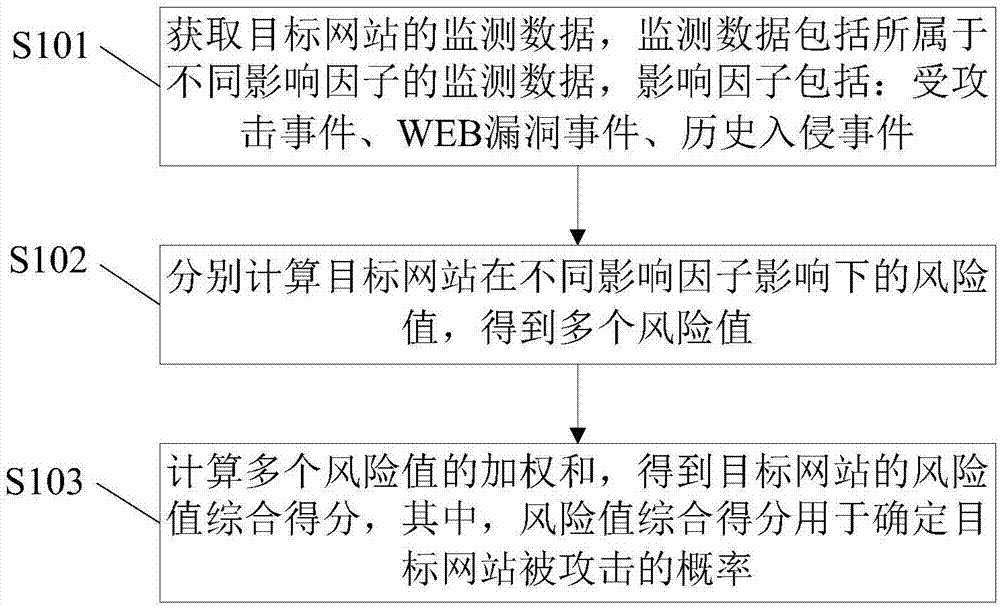
[0054] The embodiment of the present invention provides a method for evaluating the risk value of a website based on a cloud protection and cloud monitoring system, see figure 1 As shown, the method includes the following steps:
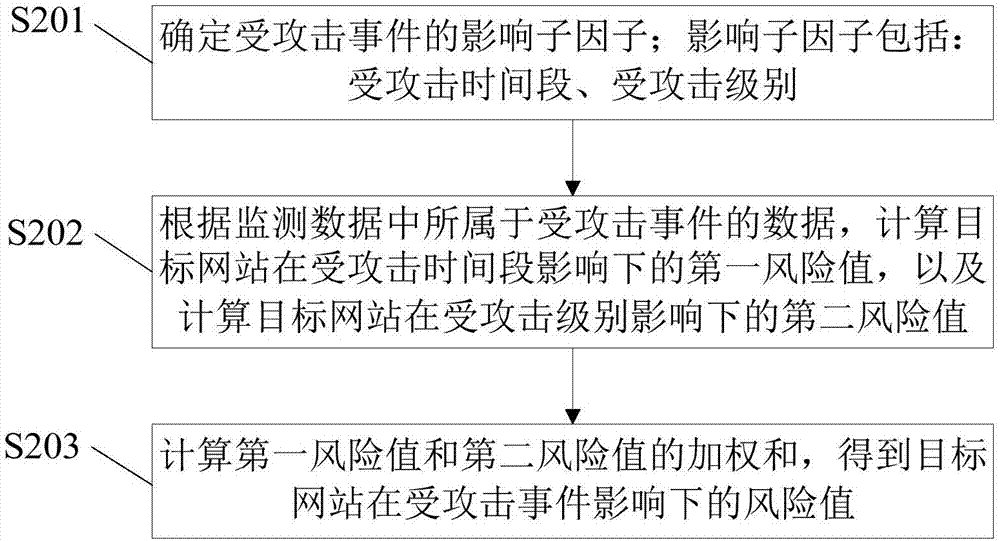
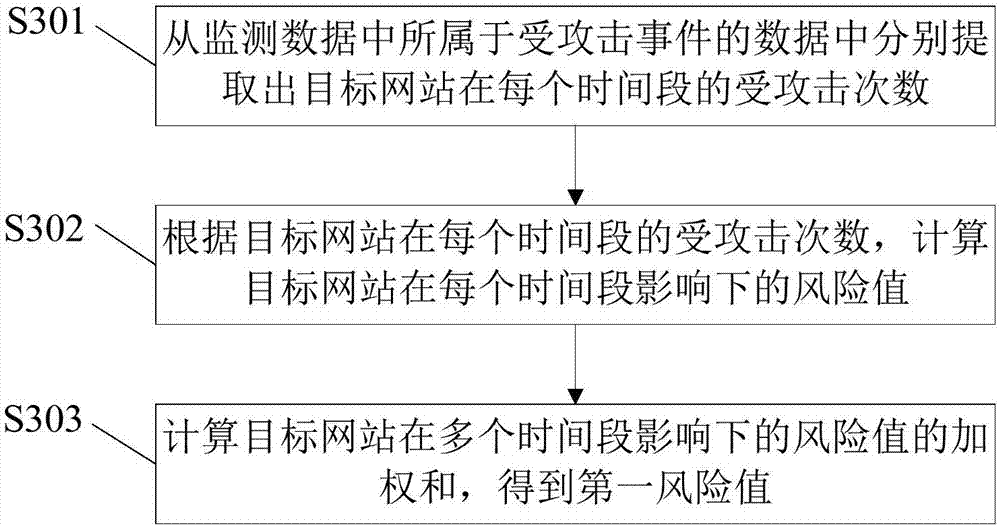
[0055] S101: Obtain monitoring data of the target website. The monitoring data includes monitoring data belonging to different impact factors. The impact factors include: attacked events, WEB vulnerability events, and historical intrusion events.
[0056] The cloud protection platform can effectively analyze, calculate and intercept network attacks and intrusions. Specifically, it can clean the access traffic of hosted websites, intercept attack behaviors, release normal access to ensure the safe operation of rear websites, and pass Real-time stream processing records access and attack records.
[0057] The cloud monitoring system can perform basic resource information detection, security event detection, website vulnerability detection, and website finger...
Embodiment 2
[0106] The embodiment of the present invention provides a website risk value evaluation device based on cloud protection and cloud monitoring system, see Figure 5 As shown, the device includes: an impact factor data acquisition module 51, a risk value calculation module 52 for each impact factor, and a website risk value synthesis module 53.
[0107] Among them, the impact factor data acquisition module 51 is used to acquire the monitoring data of the target website. The monitoring data includes monitoring data belonging to different impact factors. The impact factors include: attacked events, WEB vulnerability events, historical intrusion events; each impact factor risk The value calculation module 52 is used to calculate the risk value of the target website under the influence of different influence factors to obtain multiple risk values; the website risk value synthesis module 53 calculates the weighted sum of multiple risk values to obtain the comprehensive risk value of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com