Database structure random change-based SQL injection defense method and system
A technology of random change and defense system, applied in the field of network information security, to increase the difficulty, reduce the probability of success, and deploy flexible methods
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
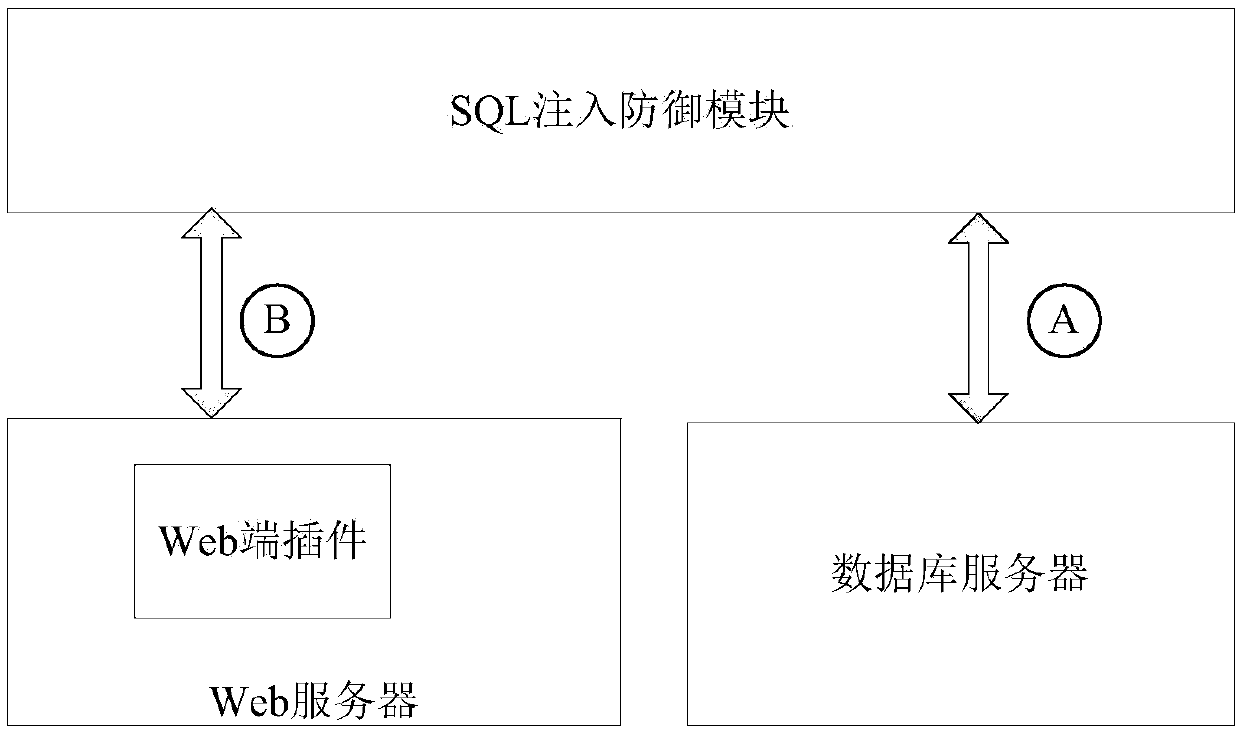
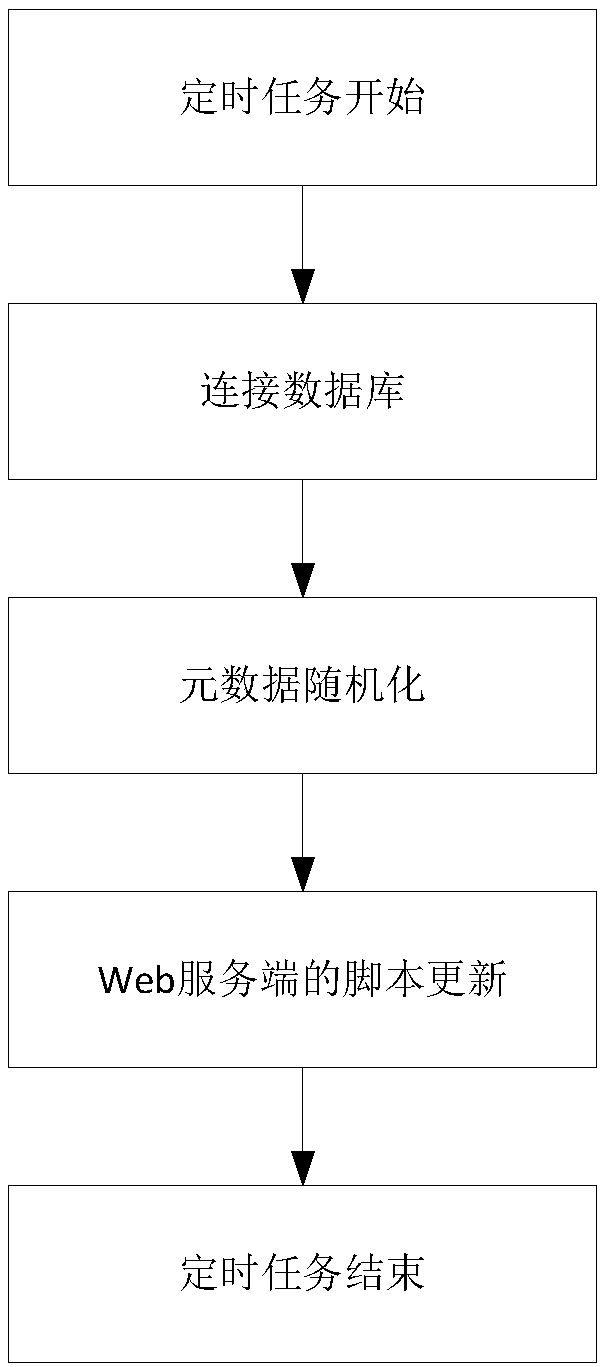
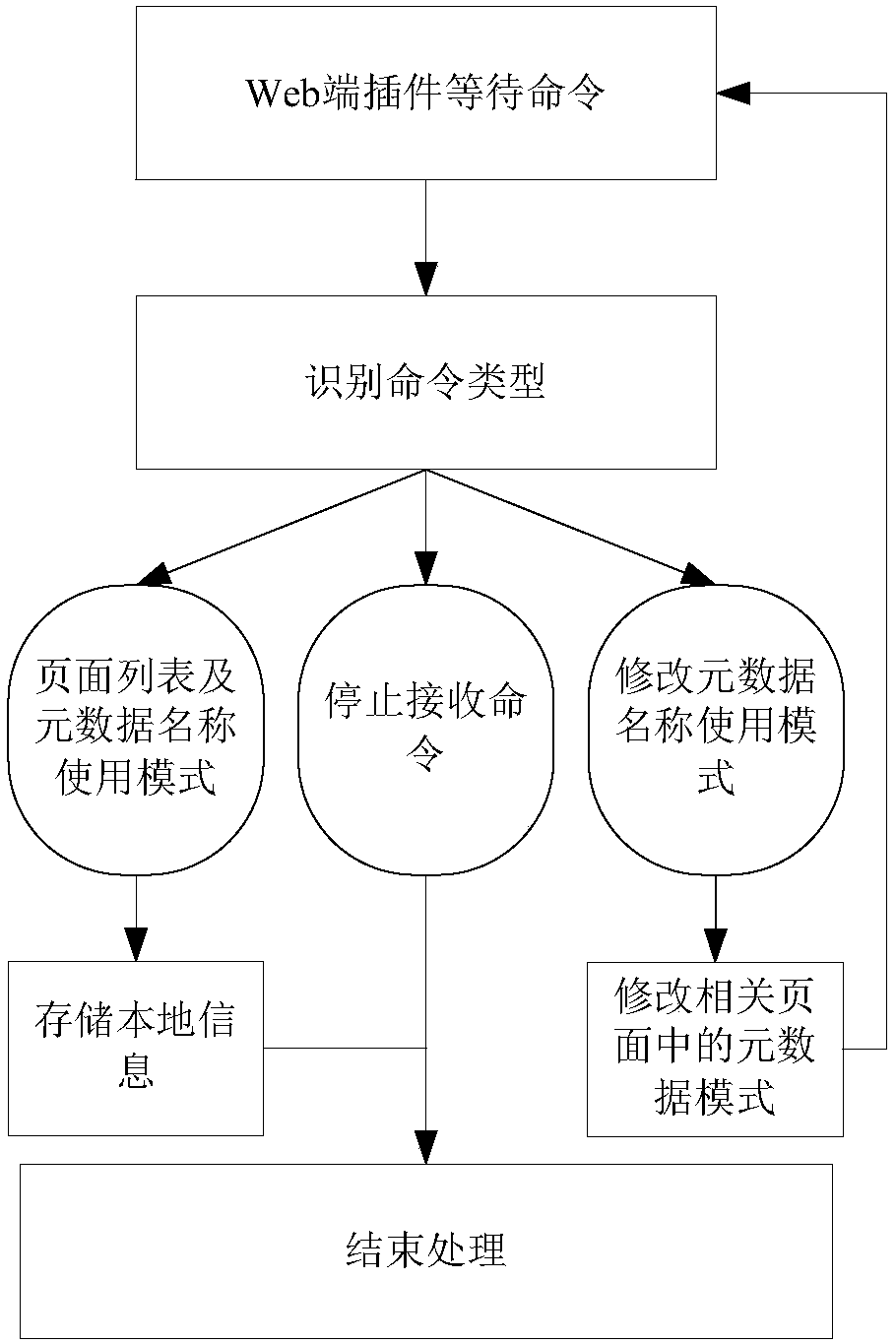
[0046] The following is a detailed description of the key technologies and implementation methods in the overall architecture of the invention, mainly including the management and maintenance of metadata and system parameters, the randomization of metadata names, the modification of metadata names, the script update of the Web server, the Web Terminal plug-ins and scheduled tasks.
[0047] 1. Management and maintenance of metadata and system parameters
[0048] In the management and maintenance function, set the list of metadata names that need to be randomized. Generally speaking, it is not necessary to record all the metadata names of the entire database into the SQL injection defense module, because different metadata have different impact on the attack. The roles of the two are not the same. Two key files are maintained here, namely system configuration files and metadata files.
[0049] System parameters can be stored in a simple system configuration file format. The ba...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com