Patents
Literature
45results about How to "Reduce business impact" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
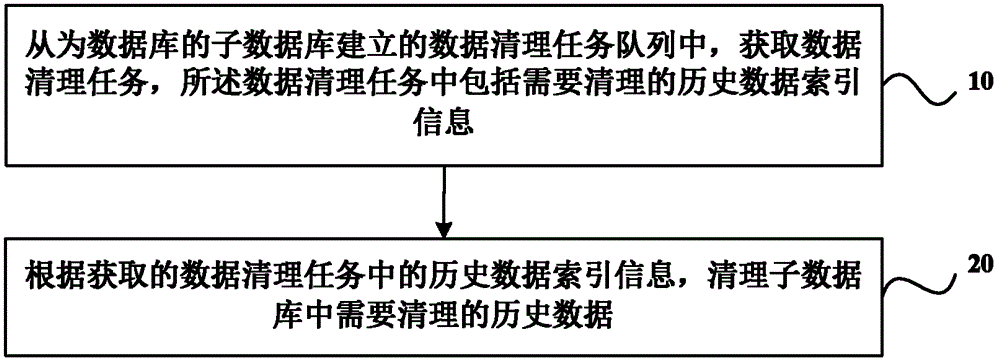
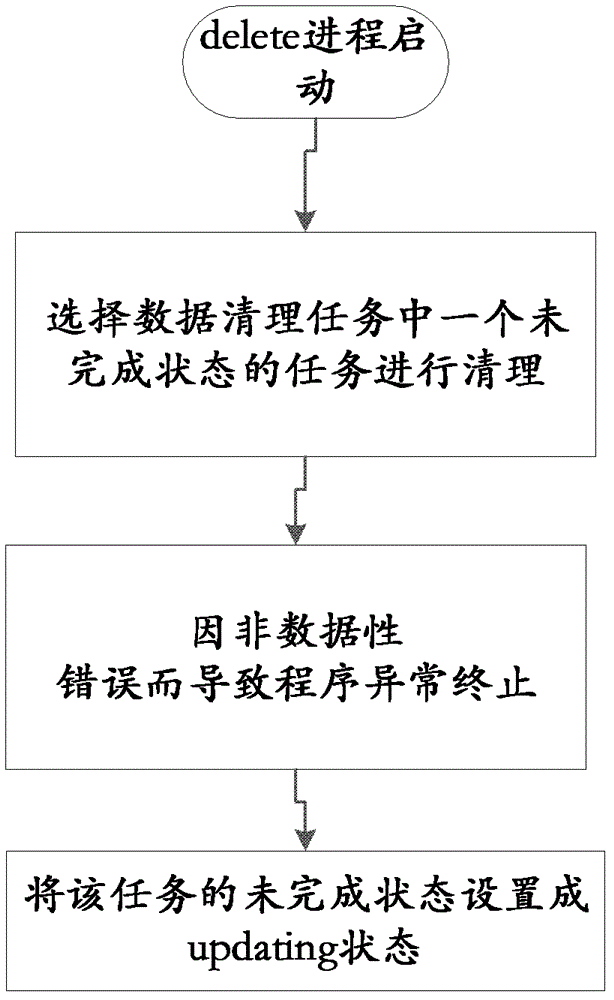
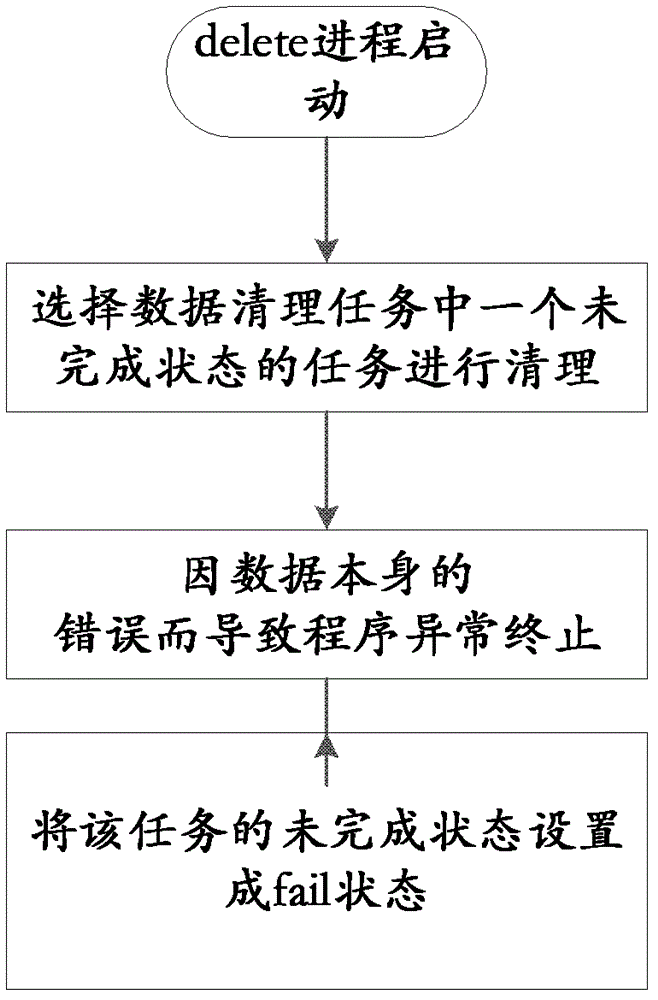
Method of cleaning database history data and system thereof
The invention discloses a method of cleaning database history data and a system of the method of cleaning the database history data. The method of cleaning the database history data includes the following steps: obtaining a data cleaning task from a data cleaning task queue established by a sub-data base of the database, wherein the data cleaning task comprises history data index information needing cleaning, the data base is divided into more than two sub-data base, and each sub-data base of all the sub-data base corresponds to the data cleaning task queue established by each sub-data base; cleaning history data needing cleaning in the database according to the obtained history data index information of the data cleaning task. Due to the technical scheme, efficiency of cleaning the data is improved.
Owner:ADVANCED NEW TECH CO LTD
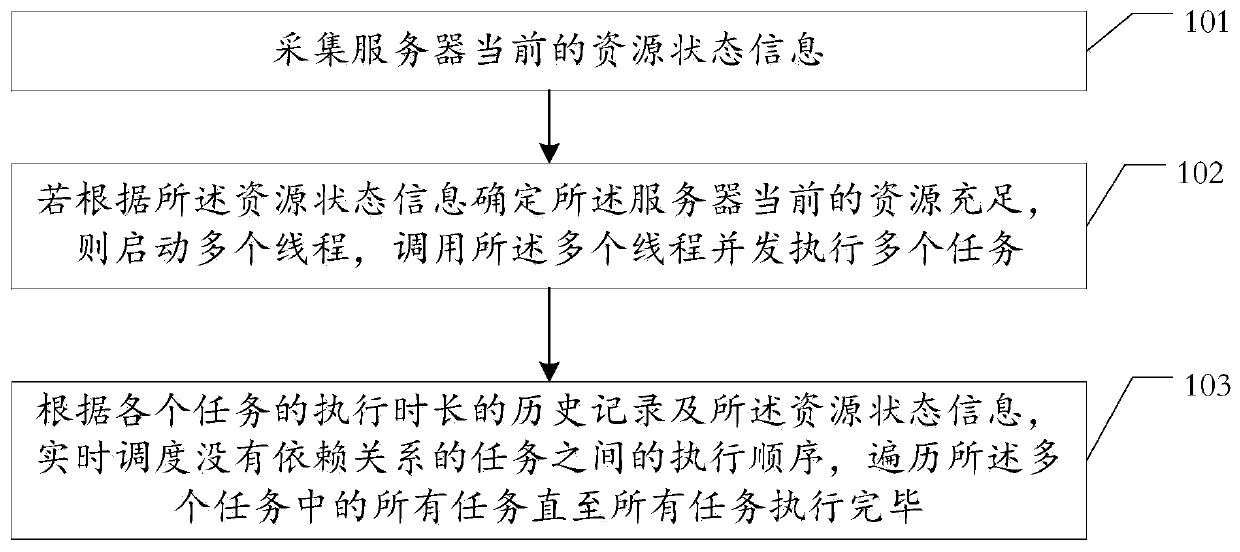
A method for scheduling an application task based on a big data behavior, server and storage medium
PendingCN109901926AImprove execution efficiencyReduce processing timeResource allocationDependency relationHistorical record
The invention discloses a method for scheduling an application task based on a big data behavior. The method comprises the steps that current resource state information of a server is collected, if itis determined that current resources of the server are sufficient according to the resource state information, a plurality of threads are started, the threads are called to execute a plurality of tasks concurrently, and no dependency relationship exists among the tasks; Wherein the dependency relationship at least comprises one of the following items: the execution sequence of the tasks has a sequential order and a dependency relationship triggered in parallel at the same time, and the execution dependency of one task depends on a relationship that the previous task is executed; And accordingto the historical records of the execution durations of the tasks and the resource state information, the execution sequence among the tasks without the dependency relationship is scheduled in real time, and all the tasks in the plurality of tasks are traversed until all the tasks are executed. The task execution efficiency can be improved, and the service influence caused by the fact that the task is not executed completely is reduced.
Owner:PING AN TECH (SHENZHEN) CO LTD
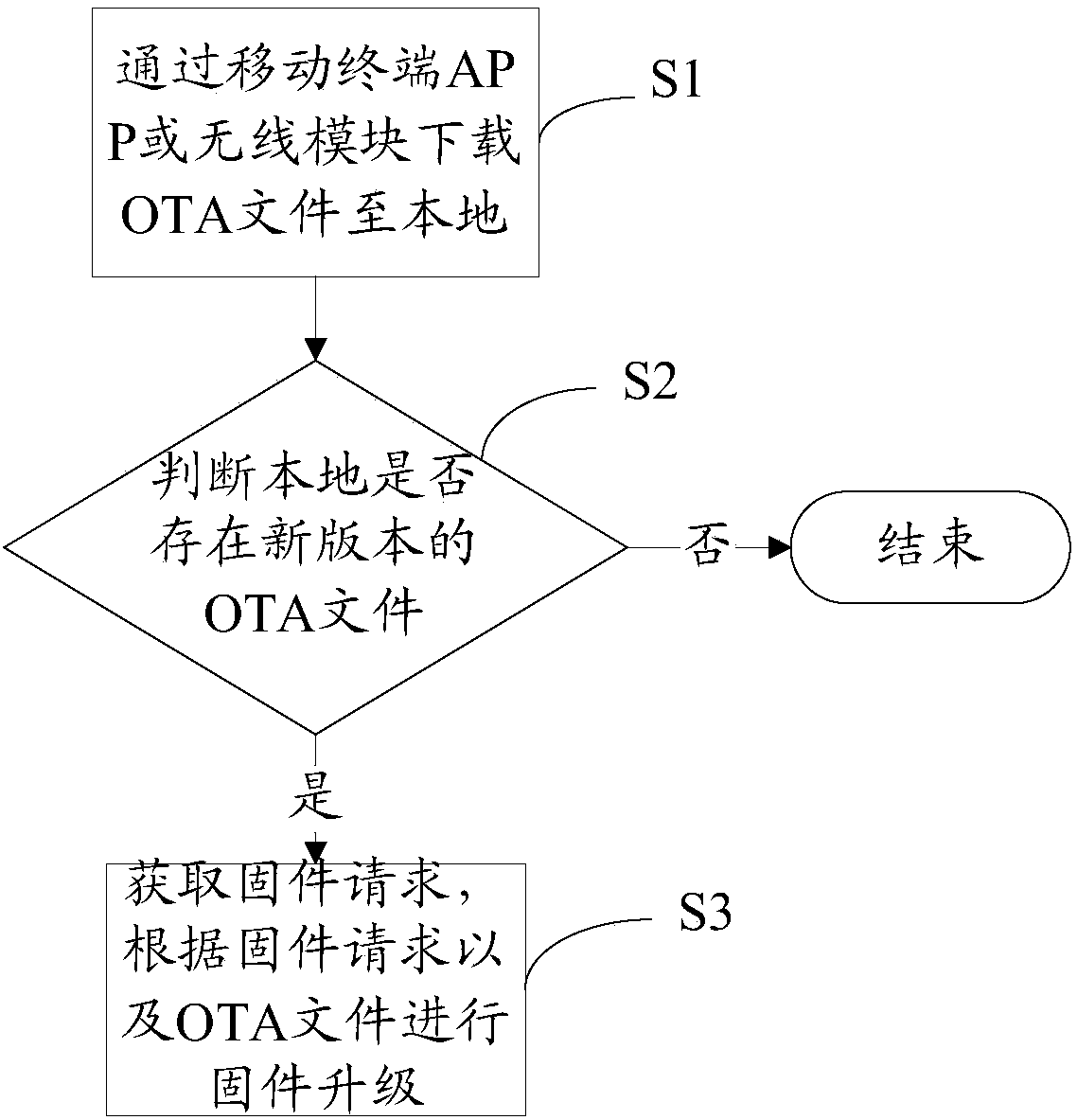
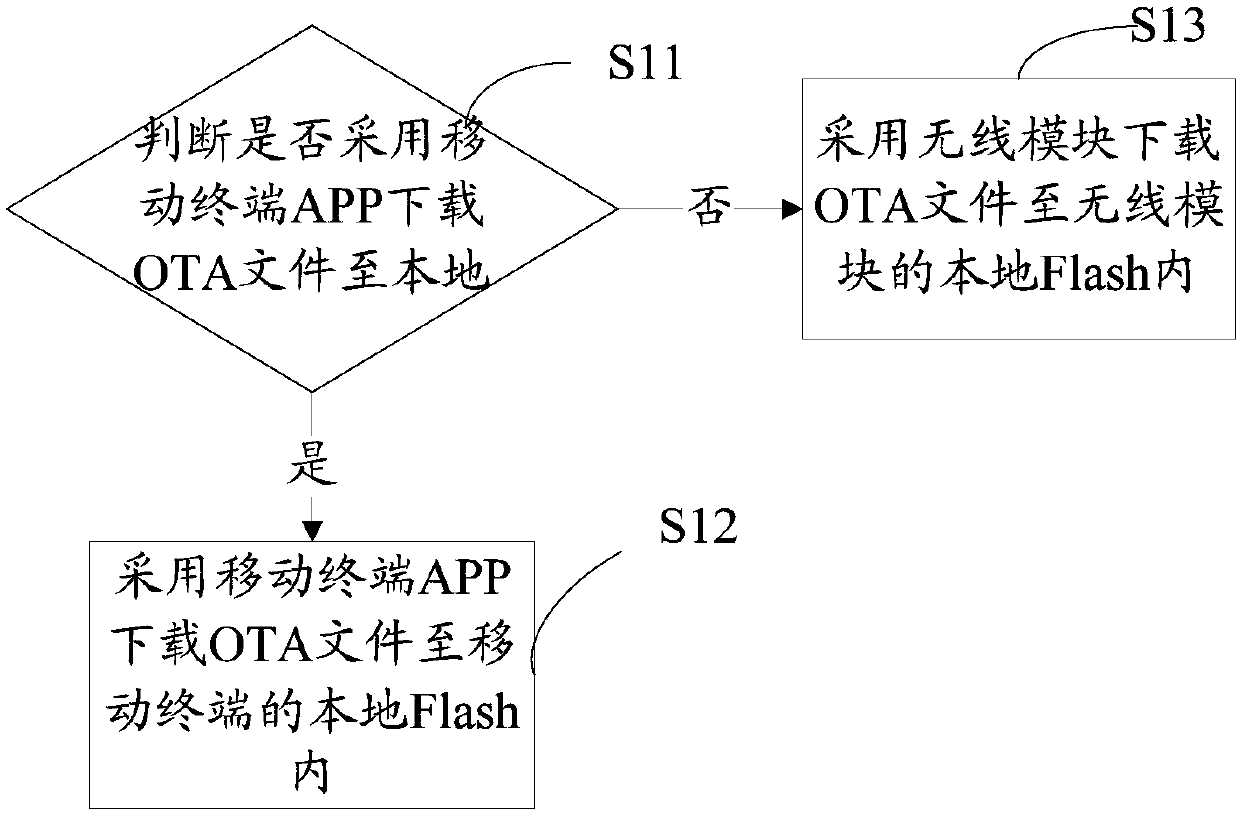
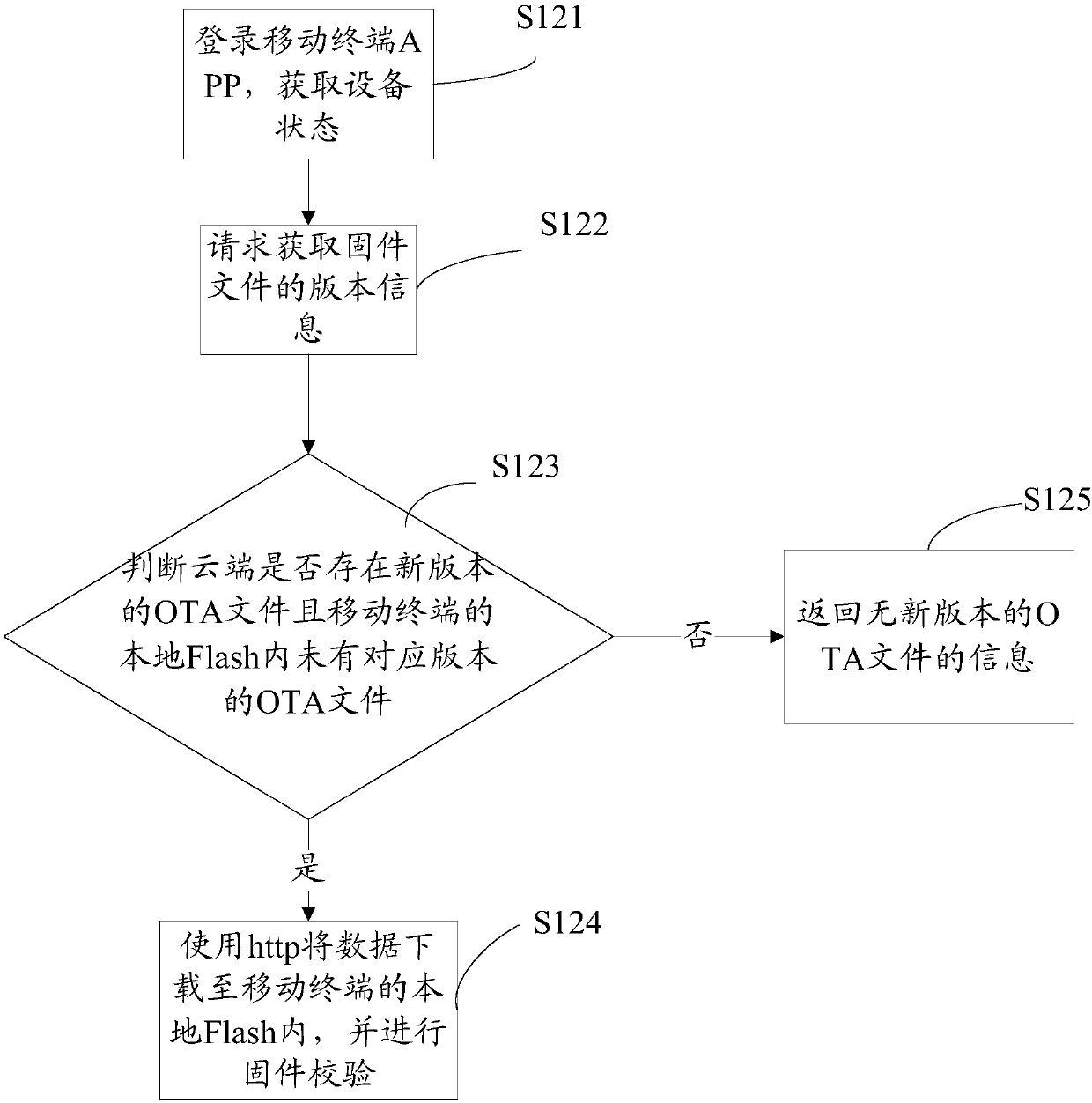
Firmware upgrading method and system
InactiveCN108023778AReduce business impactData switching networksNetwork data managementIdle timeMultiple device
The invention relates to a firmware upgrading method and system. The method comprises the steps of: downloading an OTA file to the local through a mobile terminal APP or a wireless module; judging whether a new version of OTA file exists in the local or not; if so, obtaining a firmware request, and performing firmware upgrading according to the firmware request and the OTA file; and if not, ending. According to the firmware upgrading method and system disclosed by the invention, downloading of the OTA file is carried out by adoption of the mobile terminal APP and the wireless module respectively; in the idle time, the file is downloaded to the local; the downloaded OTA file is utilized for firmware upgrading; parallel upgrading of multiple devices can be carried out at the same time; the upgrading modes of two channels are used simultaneously; influence on the normal service of a door lock can be reduced; and parallel upgrading of multiple door locks can be carried out.
Owner:SHENZHEN SPOTMAU INFORMATION TECH CO LTD
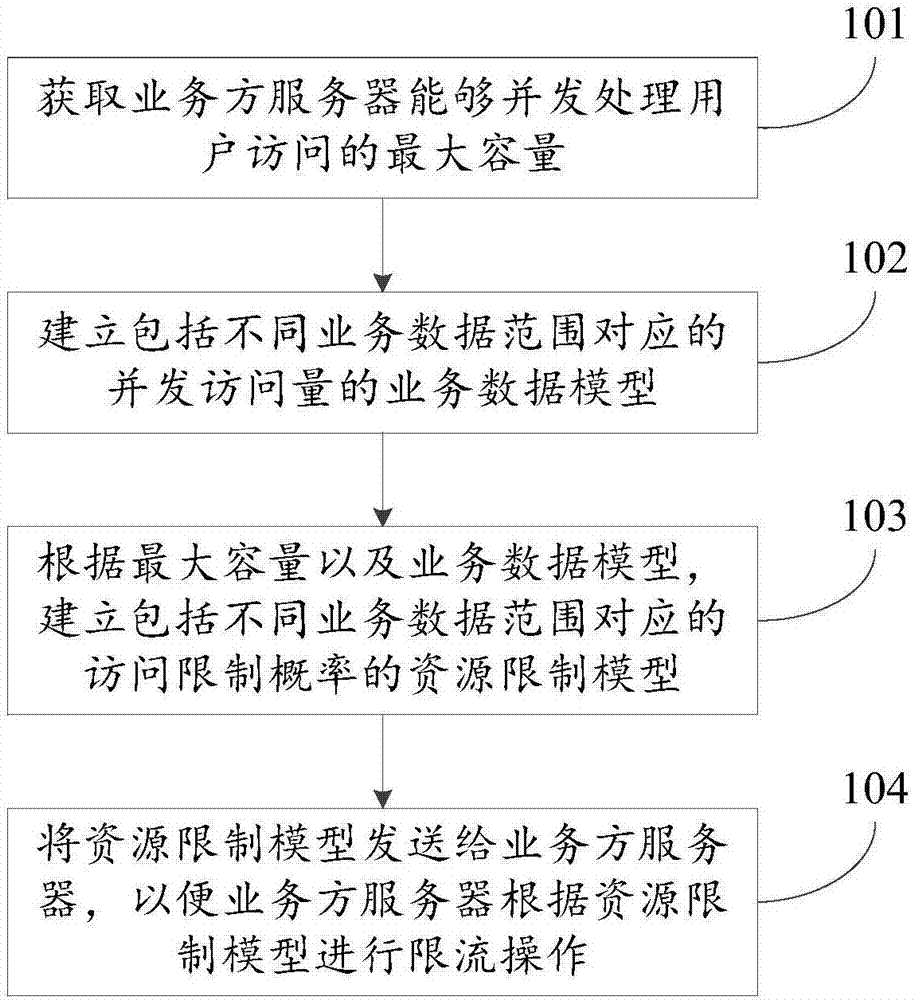
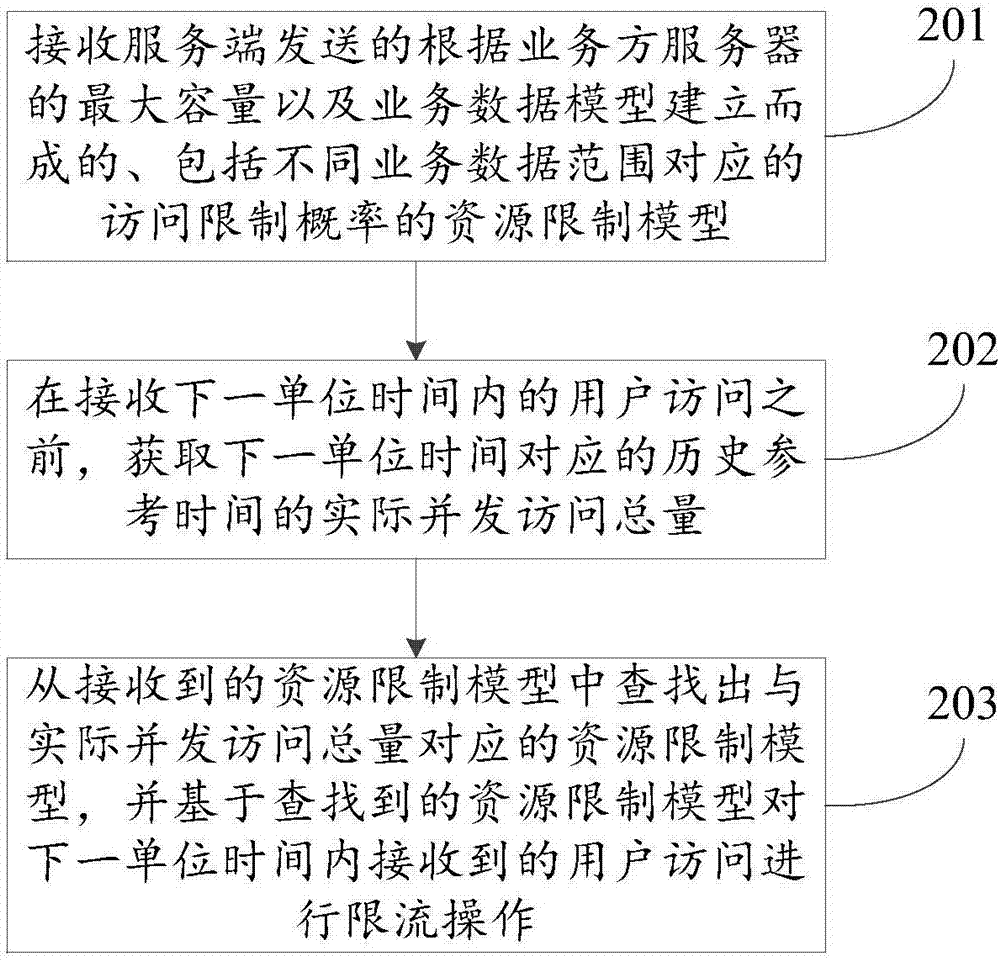
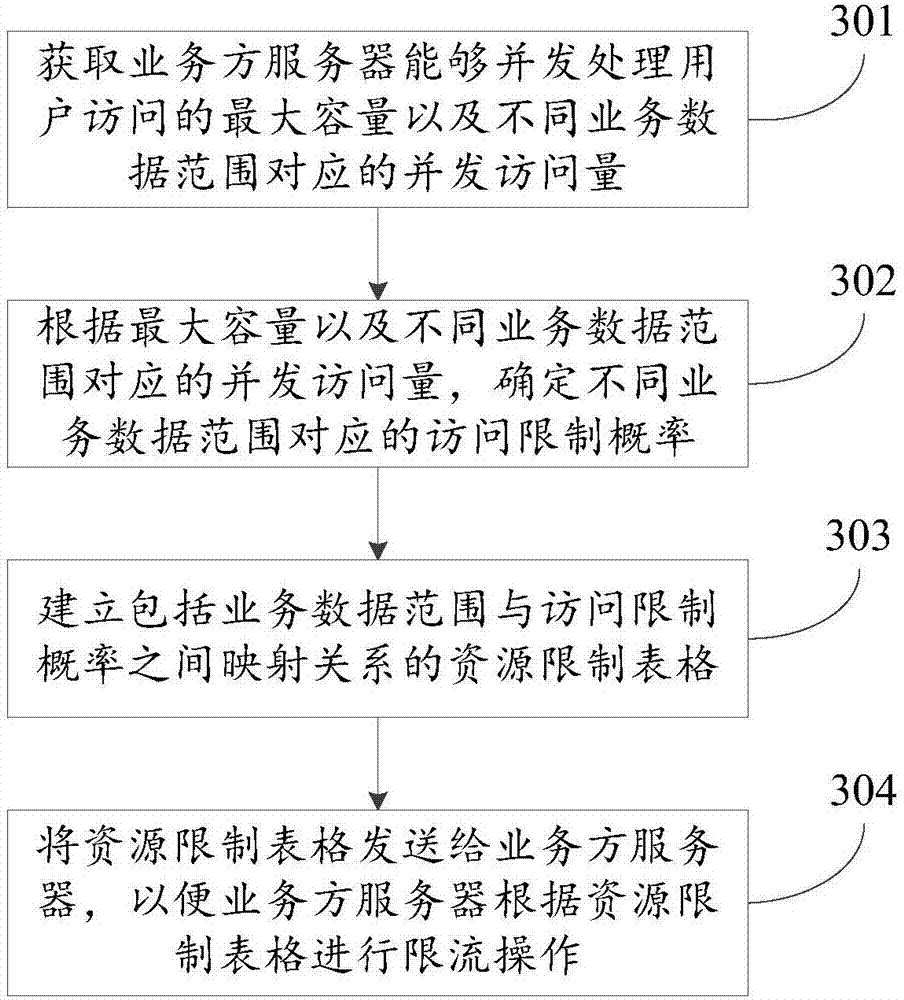
Data processing method, device and system
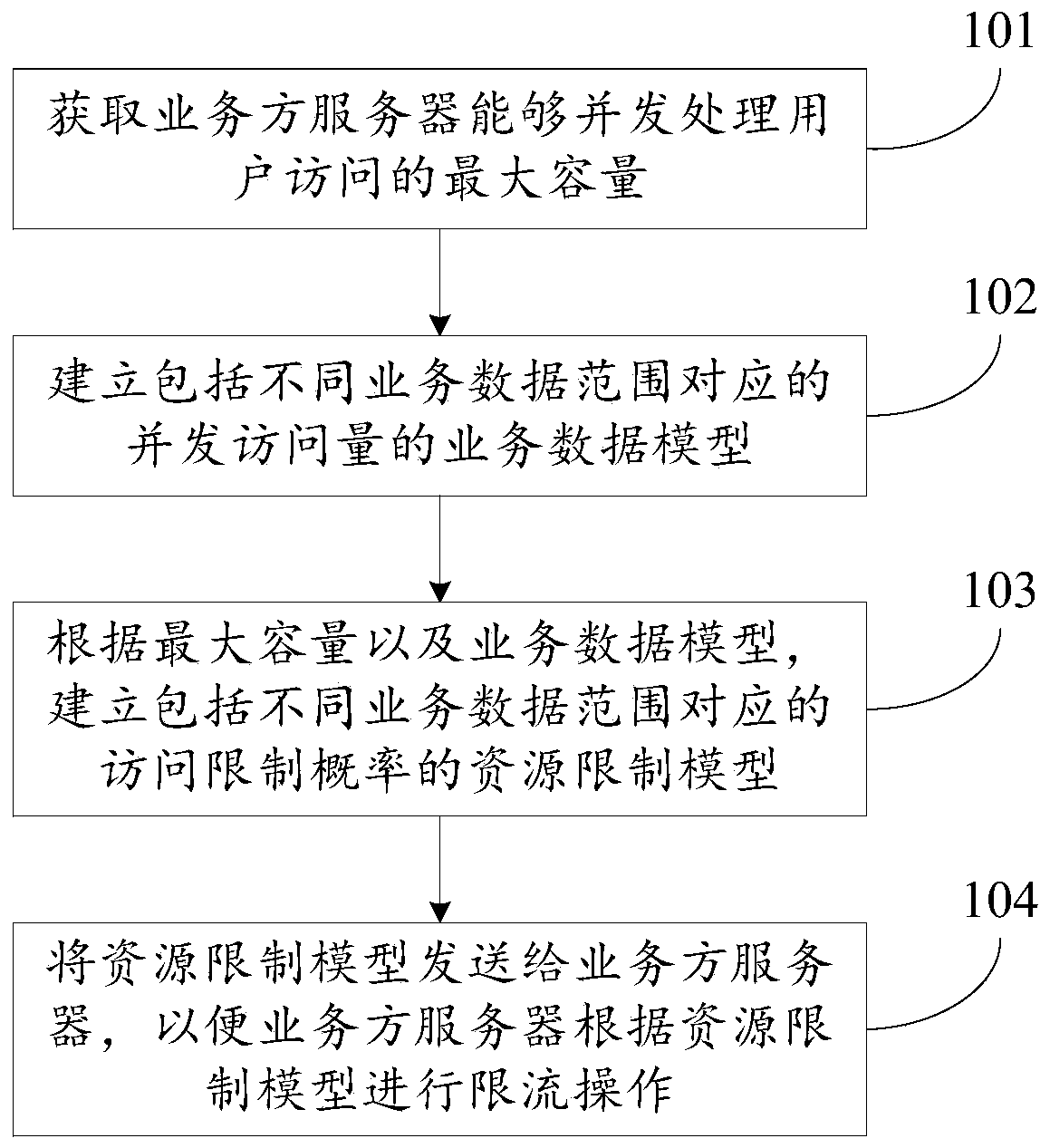
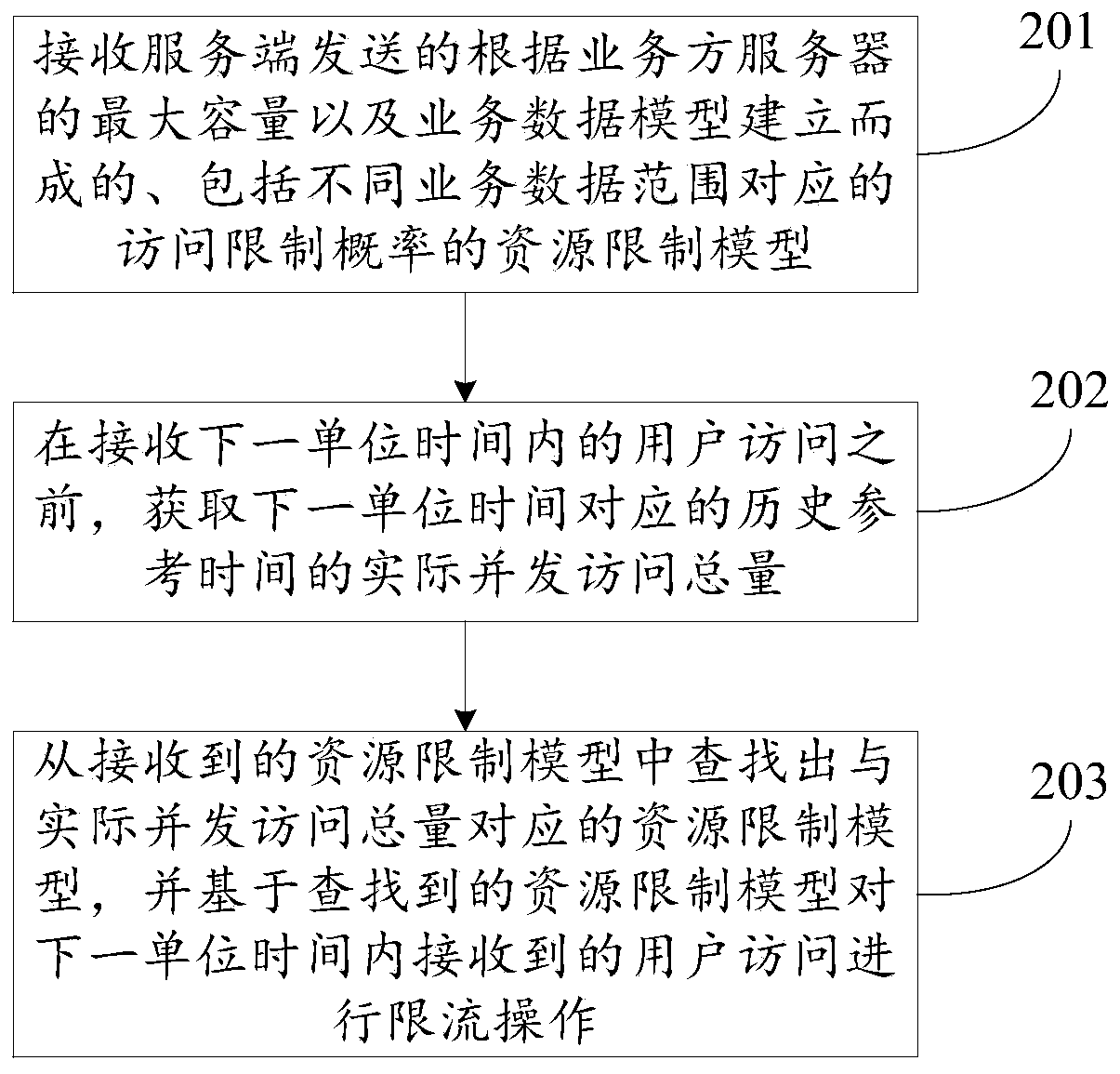
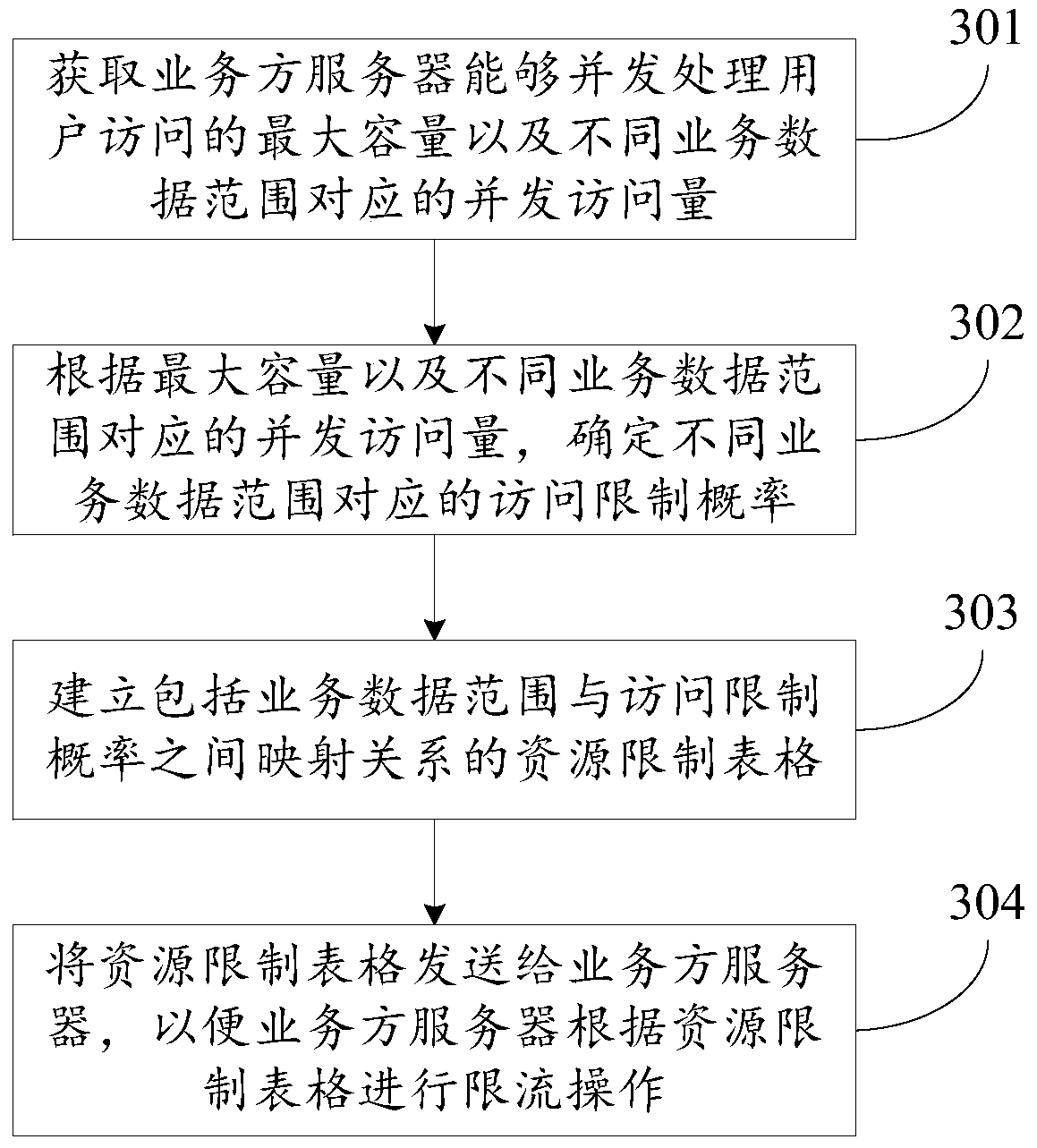
The present invention discloses a data processing method, device and system, and relates to the Internet technology field. The problem can be solve d that a current limiting strategy cannot satisfy demands of business sides at present. The method comprises: obtaining the maximum capacity of user access being subjected to concurrent processing by the server of a business side; establishing a business data model comprising concurrence access volume corresponding to different business data ranges; establishing a resource restriction model comprising access restriction probability corresponding to different business data ranges according to the maximum capacity and the business data model, wherein the access restriction probability is obtained according to the maximum capacity to allow the server of the business side to perform restriction of user access in different business data ranges according to the business strategy of the business side; and sending the resource restriction model to the server of the business side to allow the server of the business side to perform current limiting operation according to the resource restriction model. The data processing method, device and system are mainly suitable in the scenes of online transaction.
Owner:ADVANCED NEW TECH CO LTD
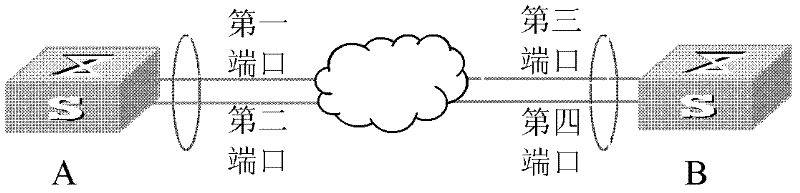
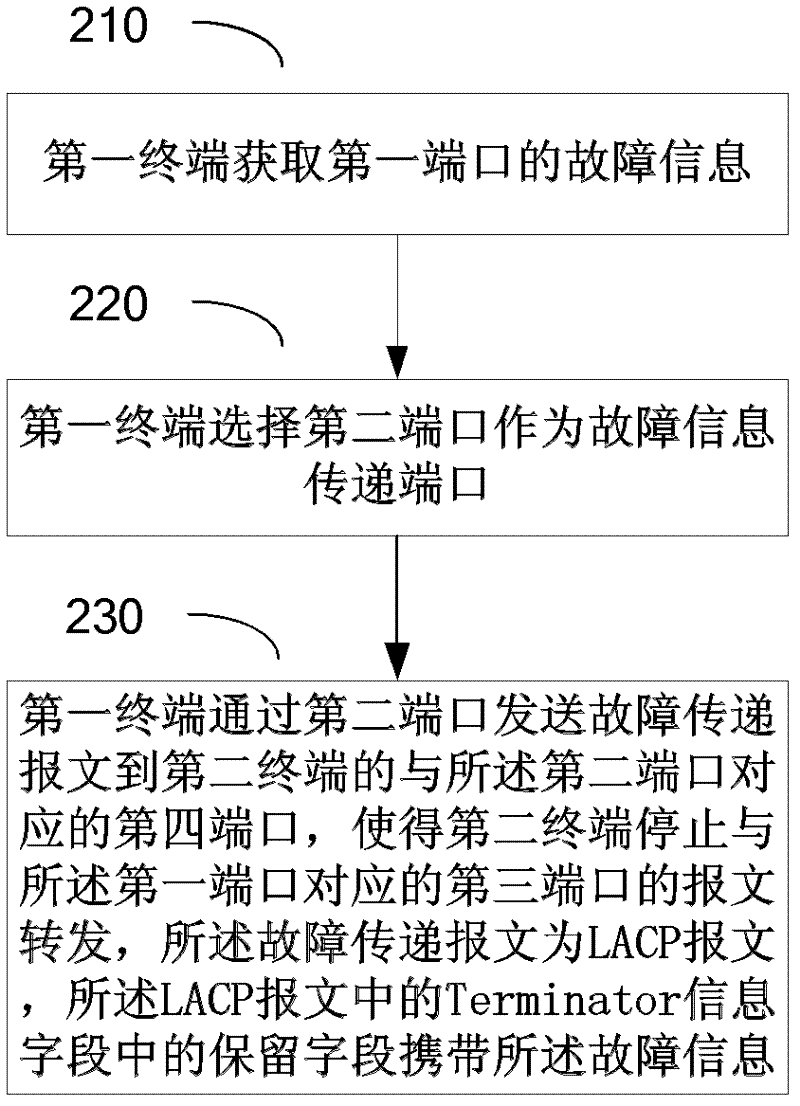
Method for processing port failures based on LACP and LACP terminal
ActiveCN102404143AReduce business impactMeet performance requirementsData switching networksInformation transmissionLink aggregation
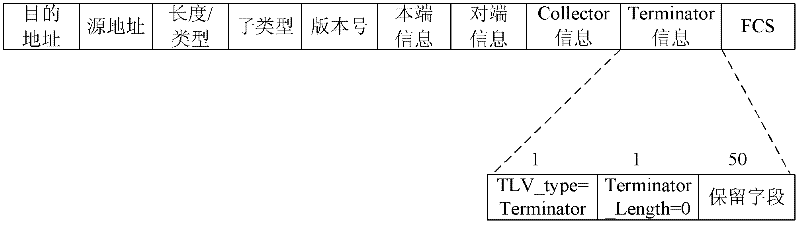
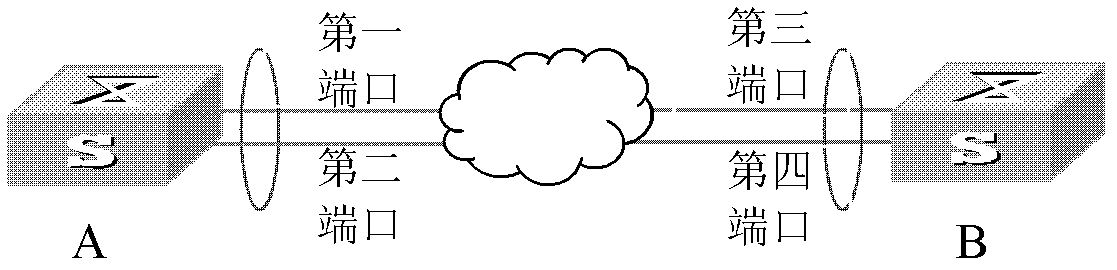
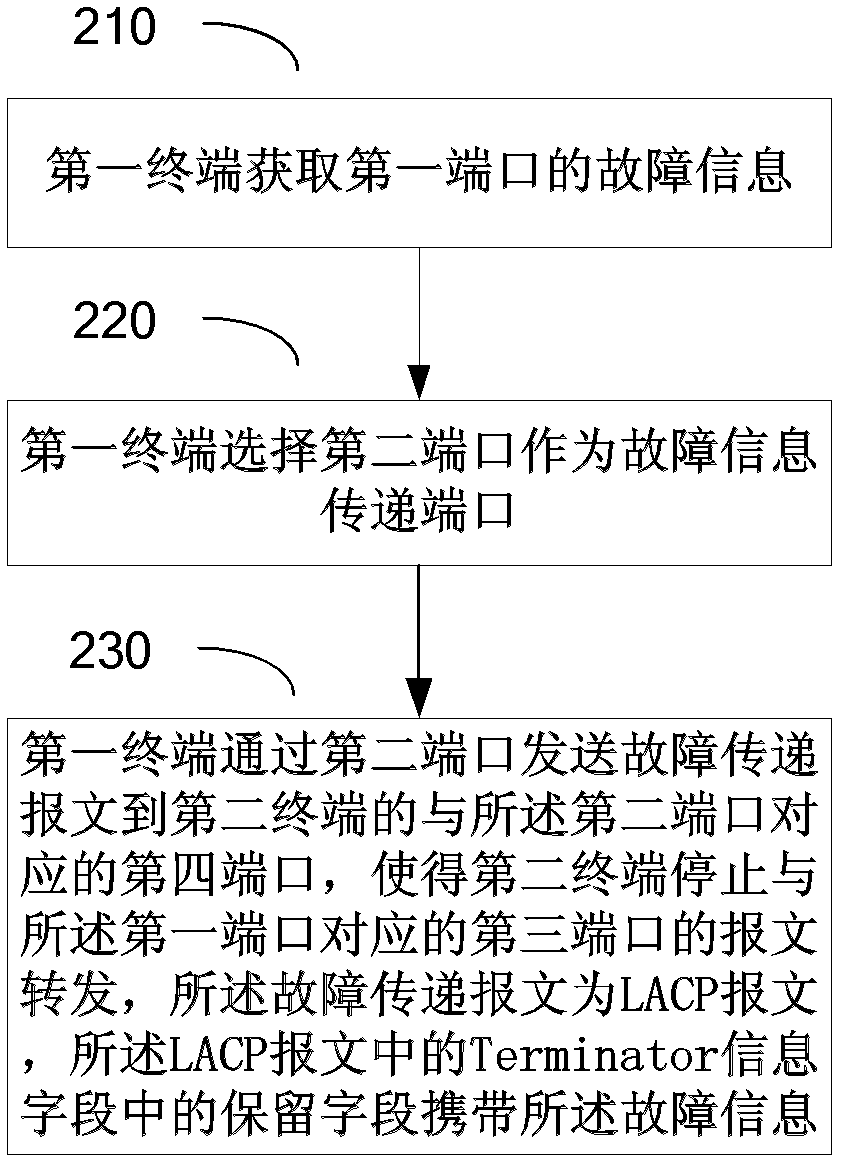
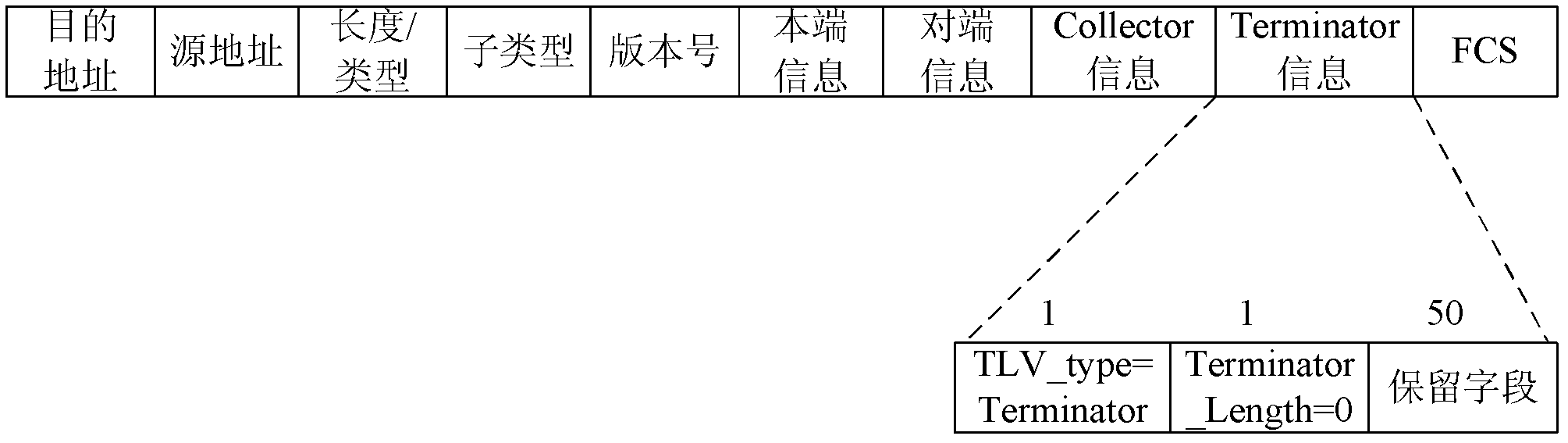
The embodiment of the invention discloses a method for processing port failures based on a link aggregation control protocol LACP and an LACP terminal. The method comprises the following steps: a first terminal obtains the failure information of the first port in a first port aggregation group; the first terminal adopts the second port in the first port aggregation group as a failure information transmission port; and the first terminal adopts the second port to transit a failure transfer message to a fourth port which is corresponding to the second port in a second port aggregation group of the second terminal so that the second terminal stops to transfer the message of a third port which is corresponding to the first port in the second port aggregation group, wherein the failure transfer message is an LACP message, and the reserved field in Terminator information field of the LACP message carries the failure information. The scheme of the embodiment of the invention improves the failure transfer performance through the optimization of the LACP, does not need depending on other protocols or technologies, and cannot be limited by the network.
Owner:HUAWEI TECH CO LTD
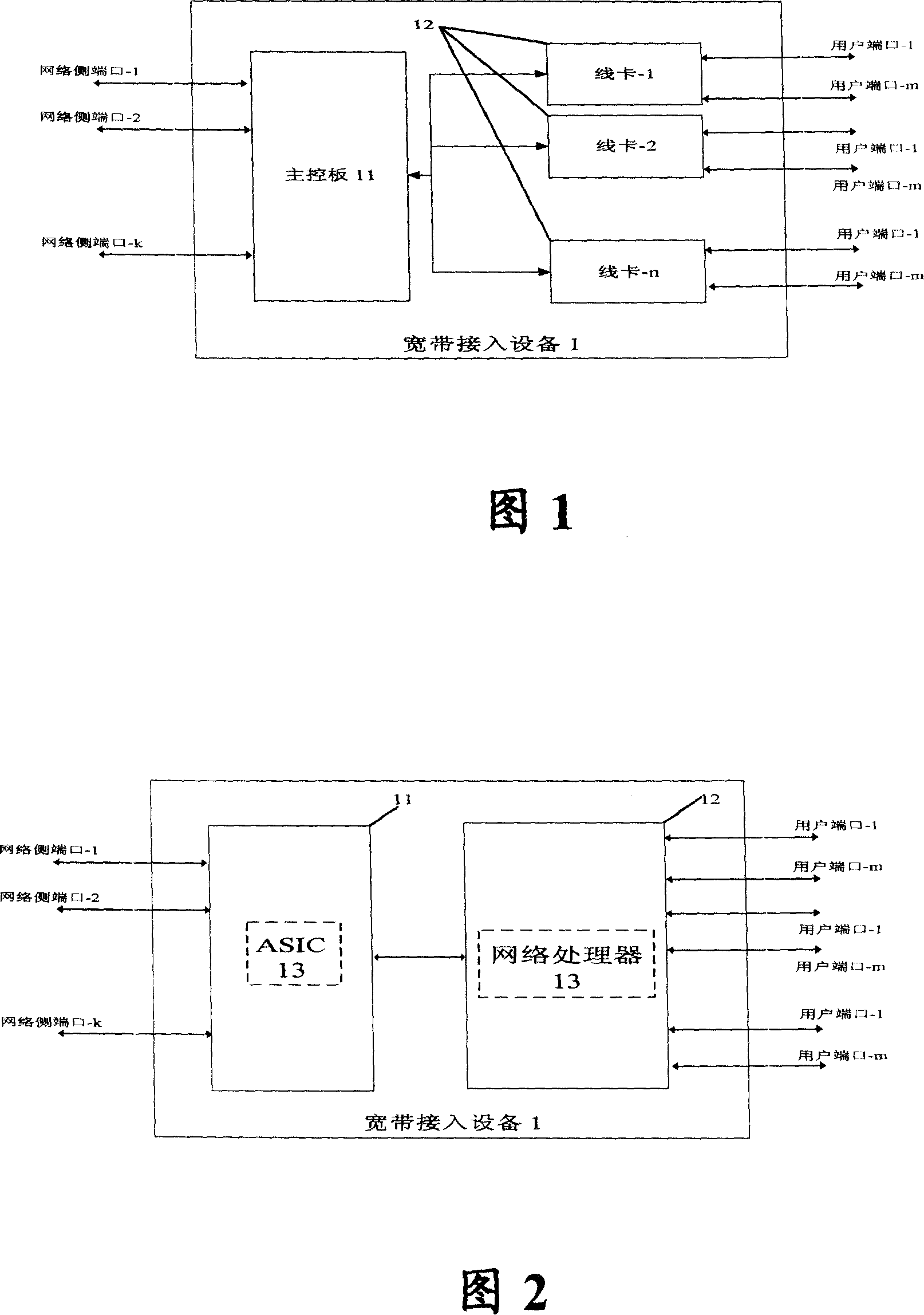
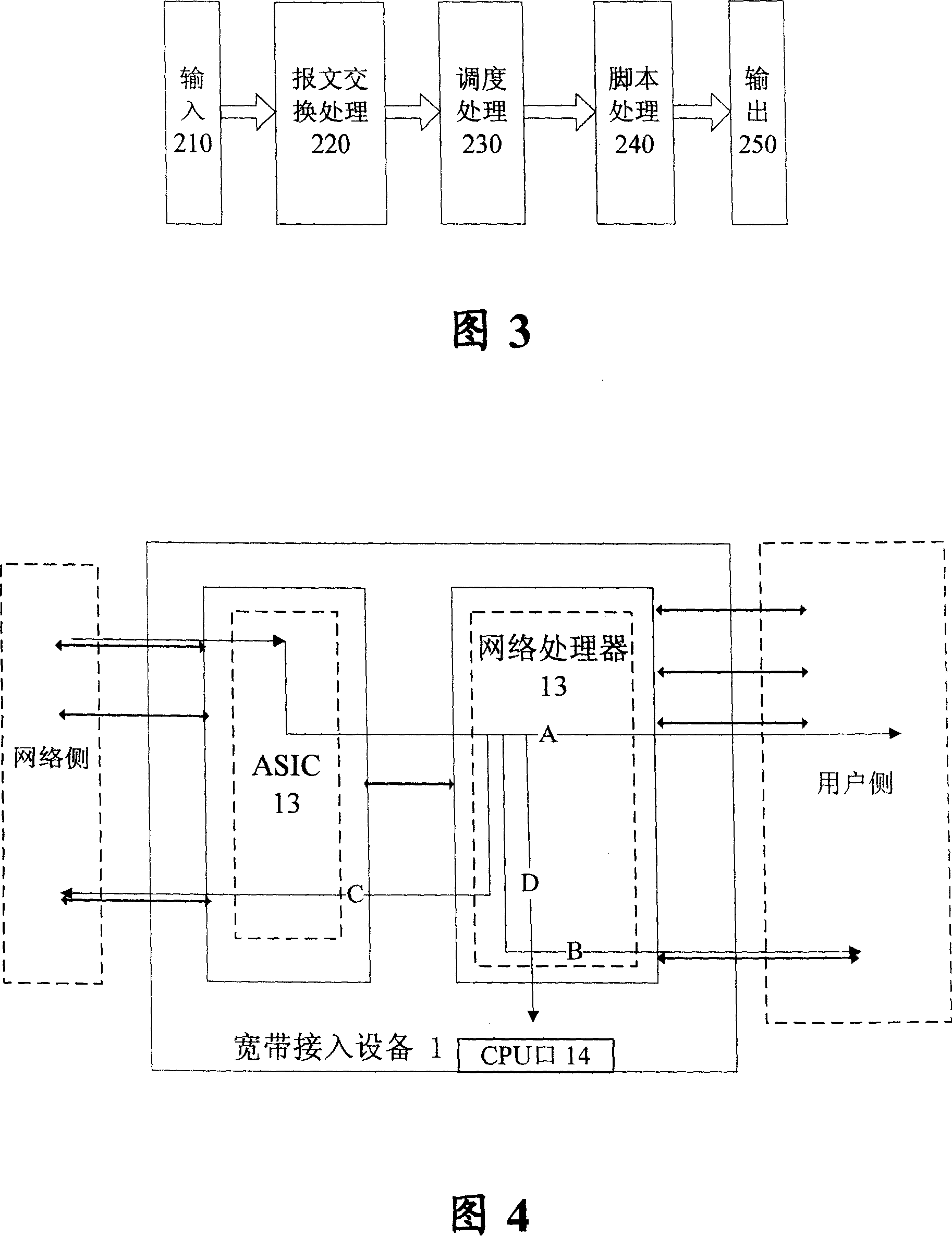
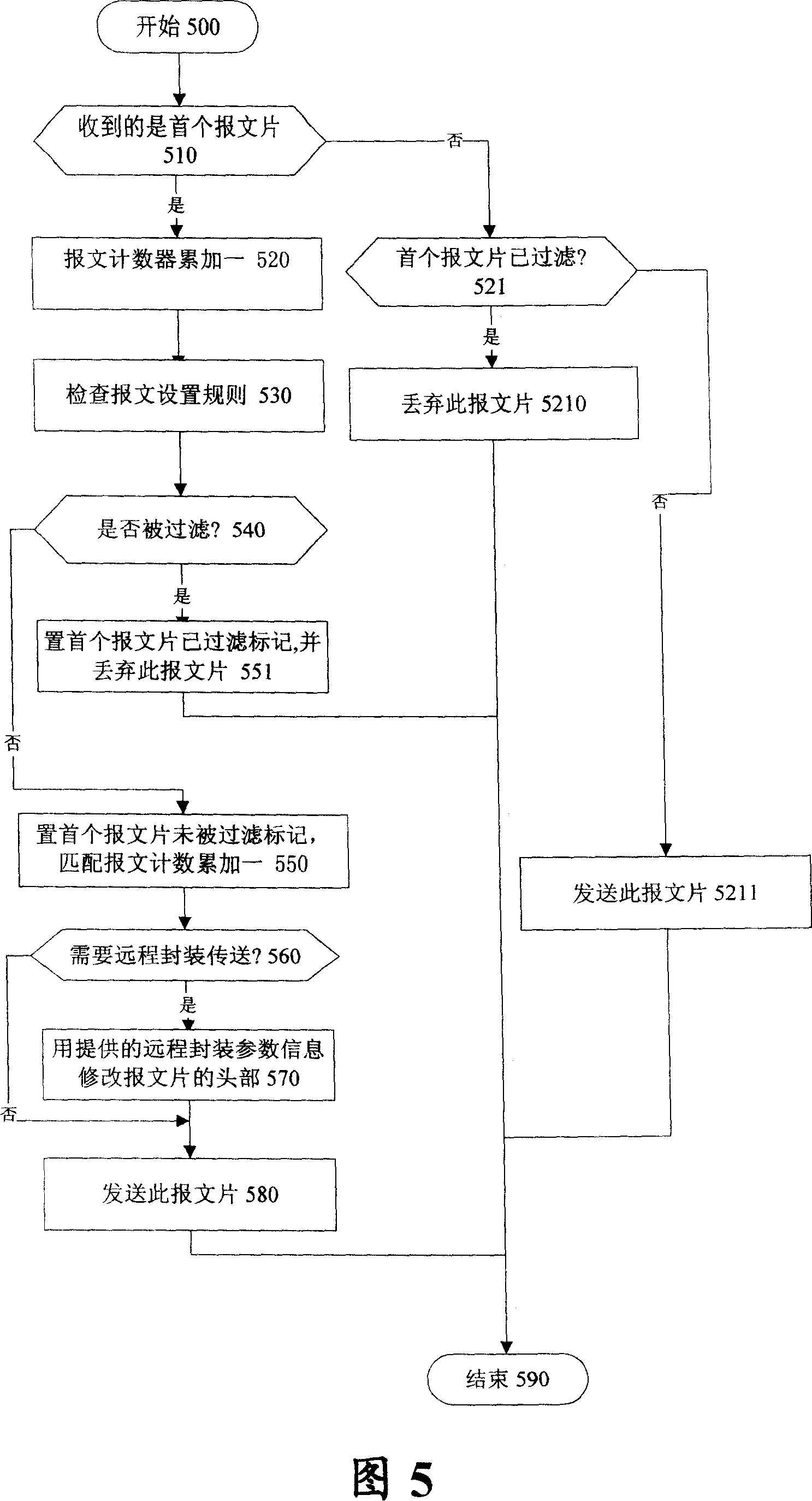
IP DSLAM business fault diagnosing method based on network processor
InactiveCN101155081AReduce interventionDoes not affect operationData switching networksWire speedProximal point
The invention relates to an IP DSLAM (1) traffic failure diagnosis method based on a network processor, using traffic flow mirror technique. An on-line traffic flow port to be diagnosed is confirmed, and spare traffic flow ports for diagnosis are selected and set in one group. When the network processor (13) sends the traffic flow port to be diagnosed to the on-line traffic flow port, the said traffic flow is copied in multicast mode and switched to the spare traffic flow port after script treatment. The copied traffic flow B or C are analyzed and an alarm or statistical information message is generated by treating the traffic flow D. The said invention fully uses linear speed processing ability of network processor, the CPU intervention is less and the running of device is not affected, at the same time all the diagnosis aims at the traffic flow port, and the influence on the affair of port to be diagnosed is little. The diagnostician is facilitated using near end, far end and script assistant specific diagnostic mode and the diagnose requirement is greatly satisfied.
Owner:ZTE CORP
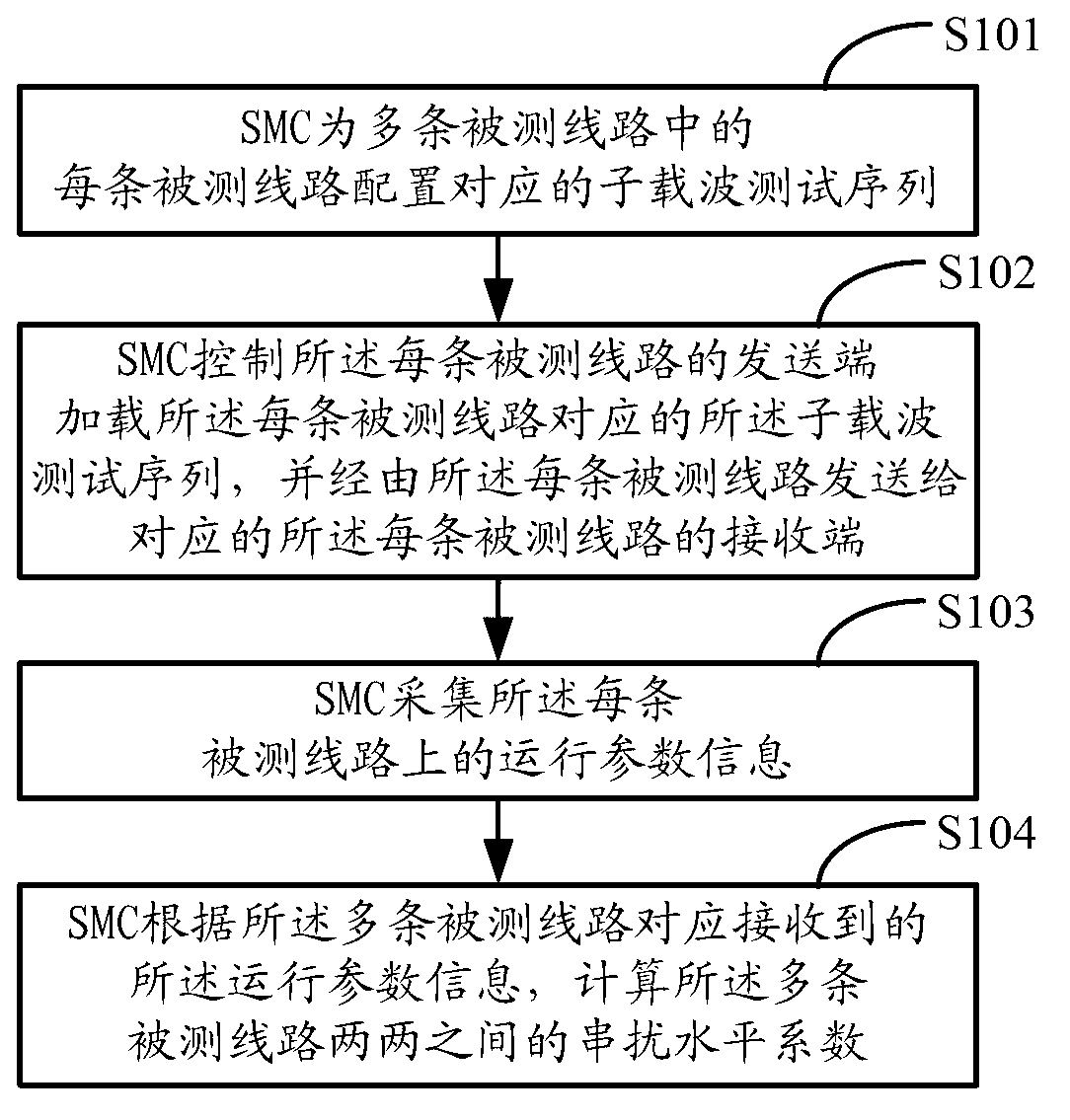
Multiline crosstalk test method, device and system
ActiveCN103229472AWork lessReduce business impactSupervisory/monitoring/testing arrangementsTransmitter/receiver shaping networksTest sequenceSubcarrier
The invention relates to a multiline crosstalk test method, device and system. The method includes: configuring a corresponding subcarrier test sequence, which includes at least one shielding frequency point, for each of the multiple tested lines and shielding transmission of subcarrier signals of corresponding frequencies on the shielding frequency points; controlling the loading, which is carried out by the sending terminal of each of the tested lines, of the subcarrier test sequence corresponding to each of the tested lines and sending the subcarrier test sequences to corresponding receiving terminals via each of the tested lines; collecting operating parameter information on each of the tested lines; and calculating the crosstalk level coefficient between every two of the tested lines according to the operating parameter information correspondingly received from the multiple tested lines. The multiline crosstalk test method, device and system enable multiple lines to be tested simultaneously so that the crosstalk test can be completed rapidly and precisely while the tested lines can still work normally. So effect on user service is small.
Owner:HUAWEI TECH CO LTD
Updating method and system for power amplification software in radio remote equipment
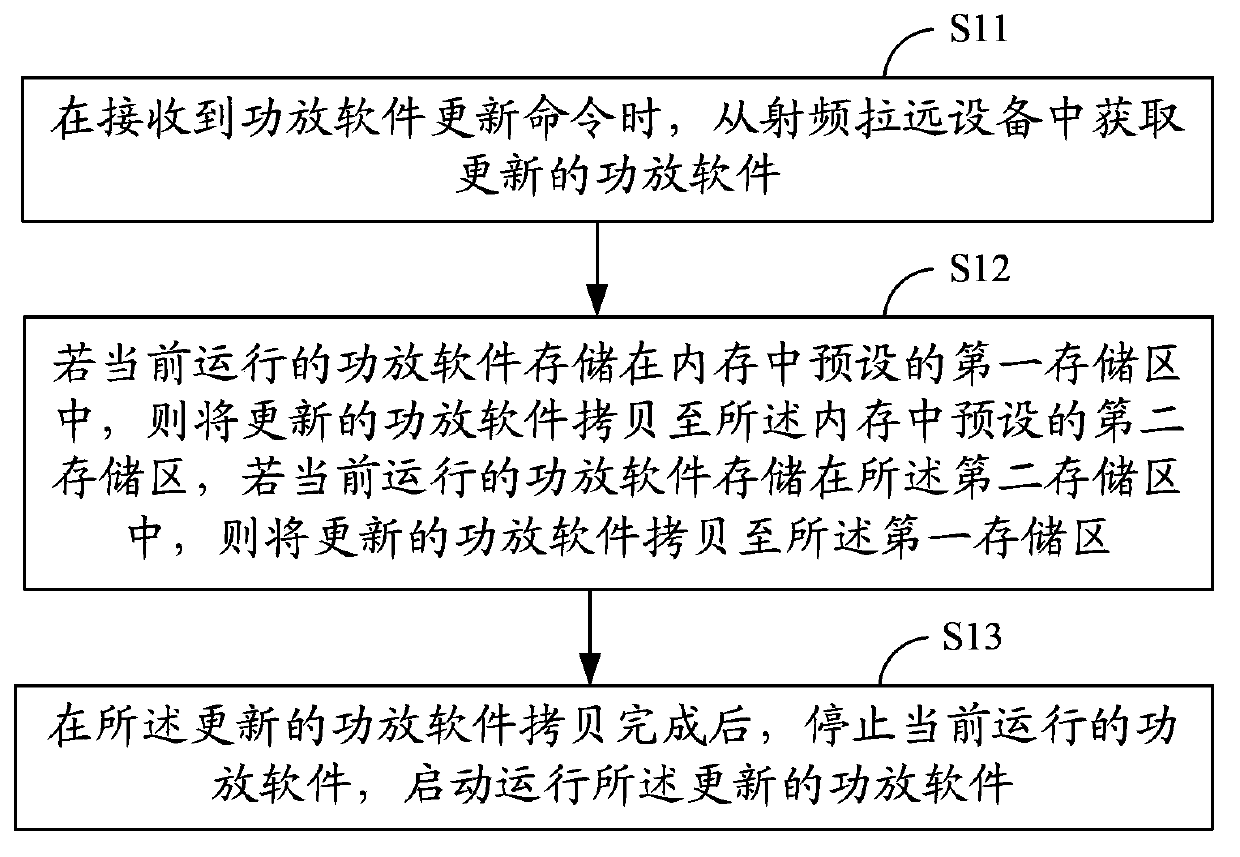
InactiveCN103970556AReduce downtimeReduce business impactProgram loading/initiatingRadio equipmentComputer module
The invention discloses an updating method for power amplification software in radio remote equipment. The updating method comprises the following steps: when an updating command to the power amplification software is received, updated power amplification software is acquired from the radio remote equipment; if the present running power amplification software is stored in a preset first memory area in a memory, the updated power amplification software is coped to a preset second memory area in the memory, or the updated power amplification software is coped to the first memory area if the preset running power amplification software is stored in the second memory area; after the updated power amplification software is completely coped, the preset running power amplification software stops, and the updated power amplification software is started up. Correspondingly, the invention further provides an updating system for the power amplification software in the radio remote equipment. The updating method and the updating system, disclosed by the invention, can achieve that the stop of the running power amplification is unnecessary when the power amplification software is updated, in addition, the updating process and version reversion are quick, and the error rate is low.
Owner:COMBA TELECOM SYST CHINA LTD
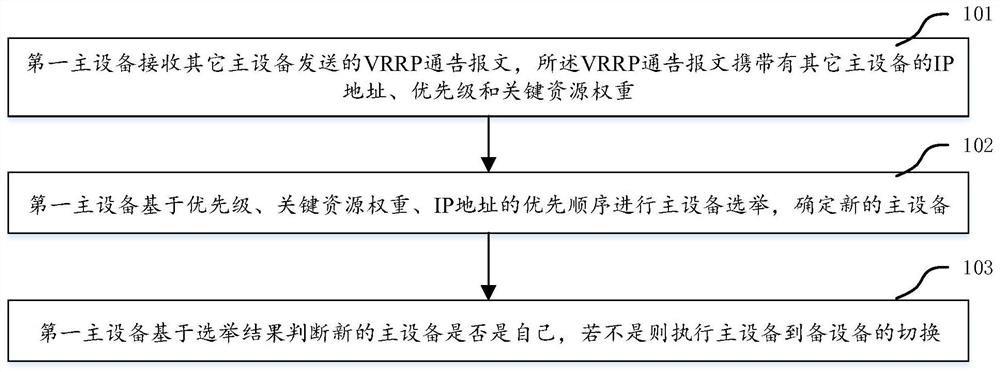
Main equipment election method and device and machine readable storage medium
ActiveCN111698158AReduce business impactGuarantee service continuityData switching networksEngineeringReal-time computing
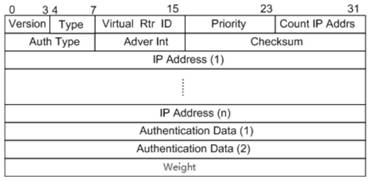
The invention discloses a main equipment election method and device and a machine readable storage medium, which are used for reducing the influence of a VRRP protocol on service continuity in the main equipment election process. According to the invention, after the main equipment receives VRRP notification messages sent by other main equipment, the priorities, the key resource weights and the IPaddresses carried by the notification messages are compared, the main equipment election is carried out based on the priority sequence, and the new main equipment is determined. According to the method, the decision condition for judging the key resource weight on the main equipment is added in the main equipment election rule, and the main equipment state of the main equipment with the large keyresource weight is maintained preferentially, so that the influence on the current ongoing service is reduced, and the service continuity of client hosts or users is ensured as much as possible.
Owner:NEW H3C TECH CO LTD
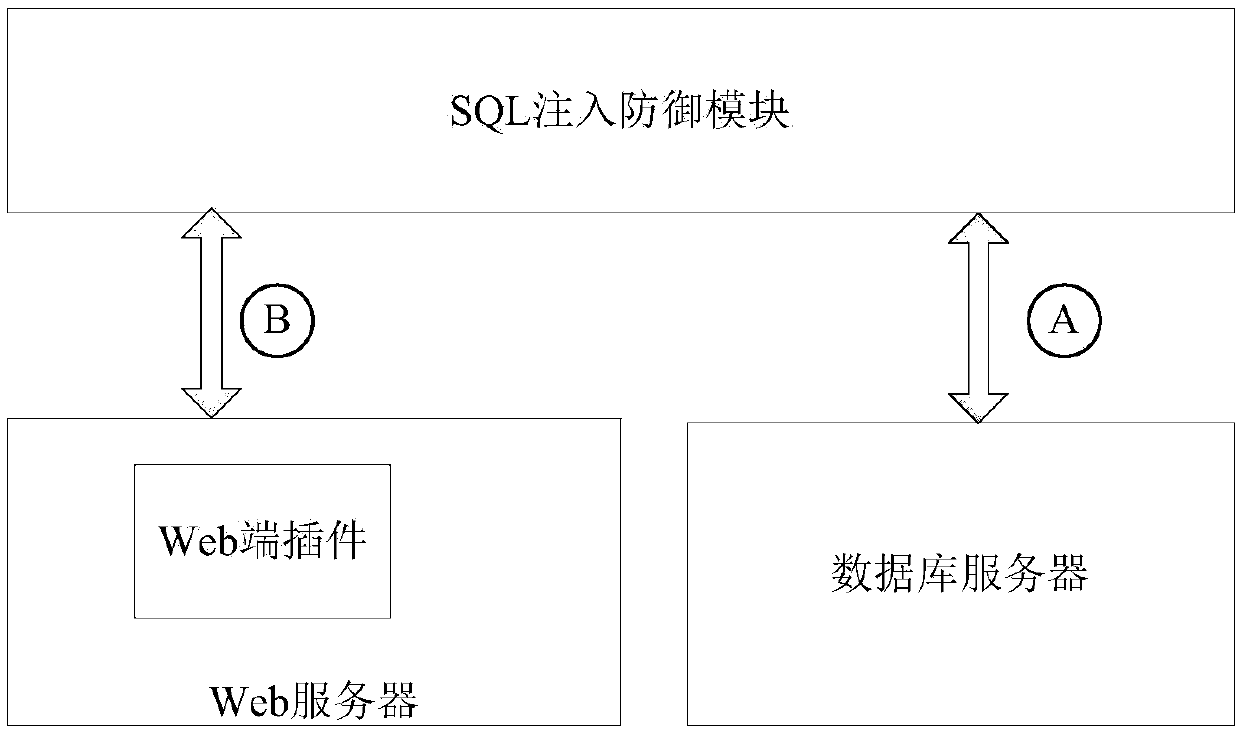
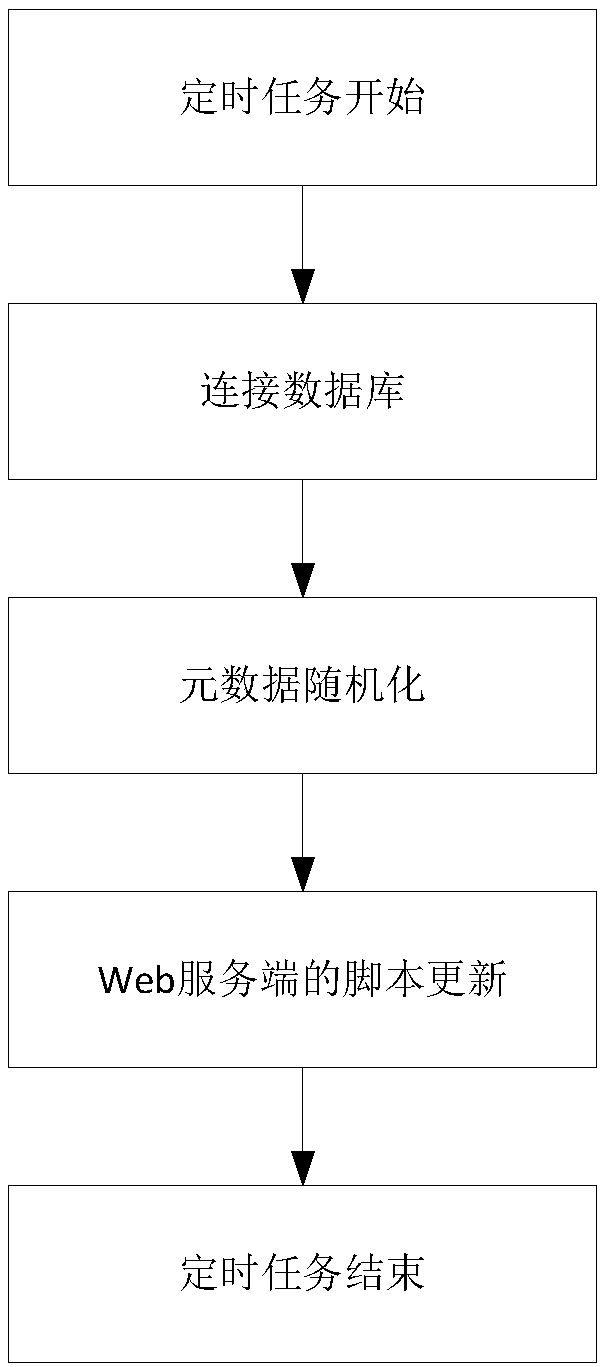
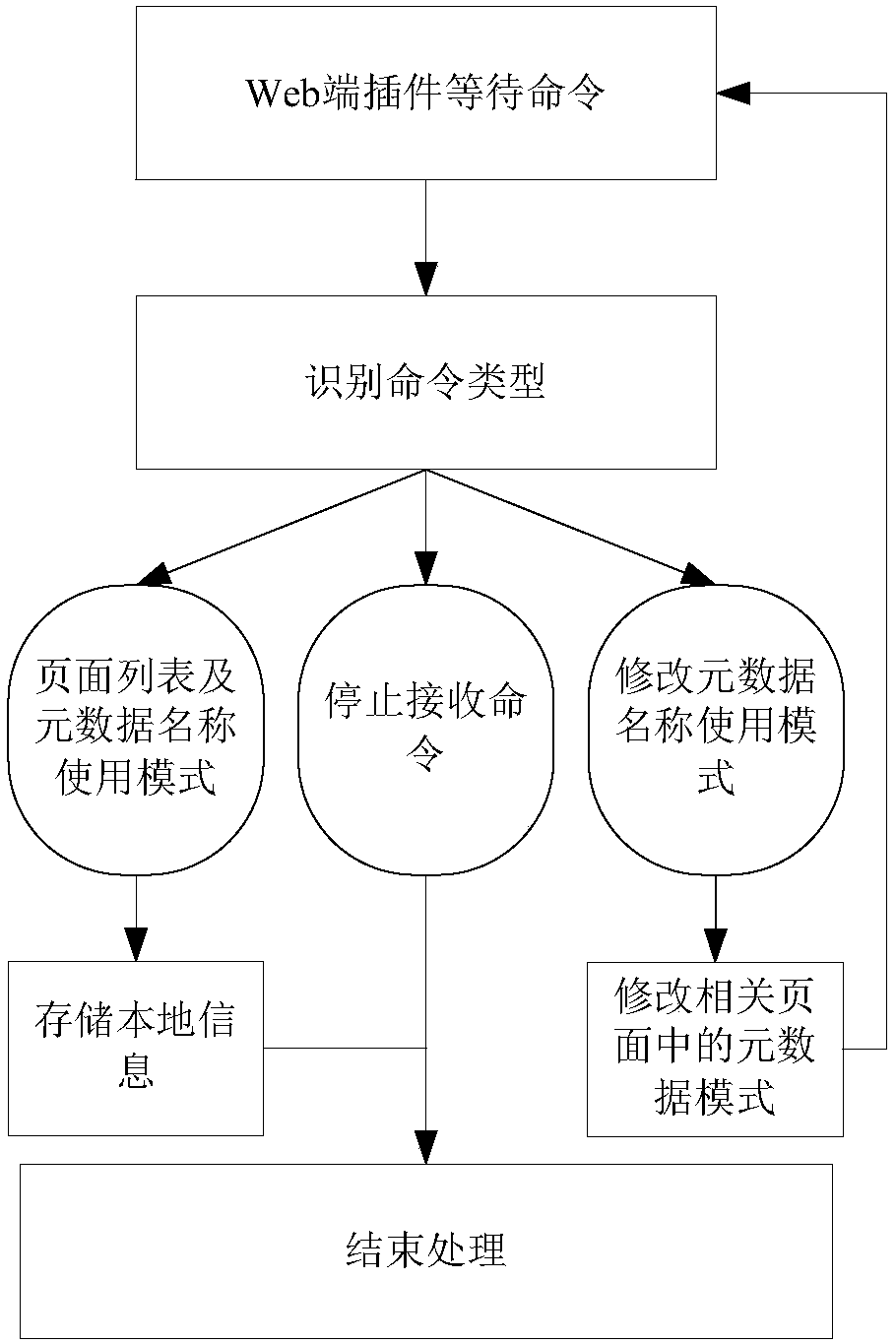
Database structure random change-based SQL injection defense method and system
ActiveCN107392014AEasy injectionReduced probability of injection attacksWeb data indexingPlatform integrity maintainanceWeb serviceSQL injection
The invention belongs to the technical field of network information safety, and specifically discloses a database structure random change-based SQL injection defense method and system. The method comprises the following steps of: firstly carrying out active and random change on a key metadata name in a database by using an active defense thought, and synchronizing the change with an application program at a Web side to ensure that metadata names of the whole database application system randomly change in a certain parameter space, so as to increase the difficulty of guessing the metadata names by attackers of SQL injection; and increasing the name space through setting proper time interval of parameter random change, so as to effectively reduce the SQL injection attack success probability and decrease the bad influences brought to normal users in the random change process. The system mainly comprises an SQL injection defense module and a Web side plugin; the SQL injection defense module and the Web side plugin form a novel framework to carry out safety reinforcement on an application system formed by a Web server and a database server; and the deployment is flexible and convenient.
Owner:FUDAN UNIV
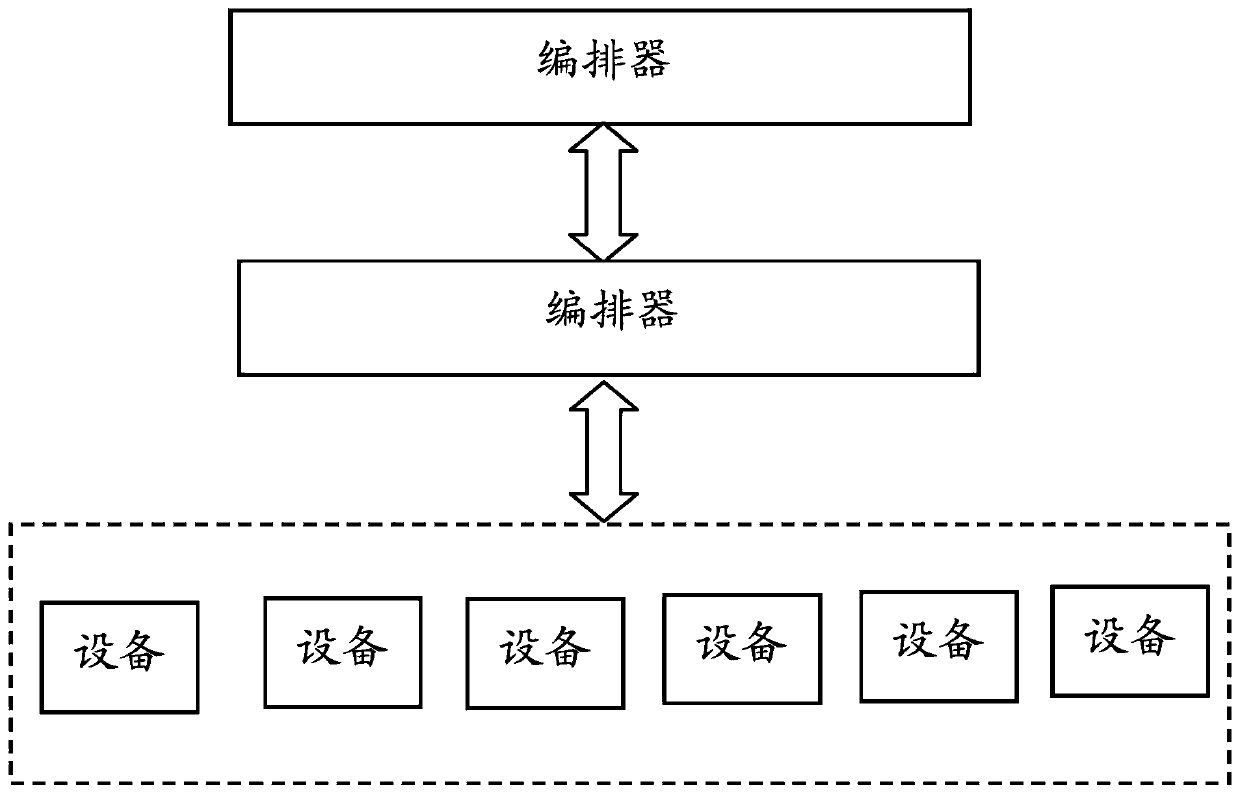
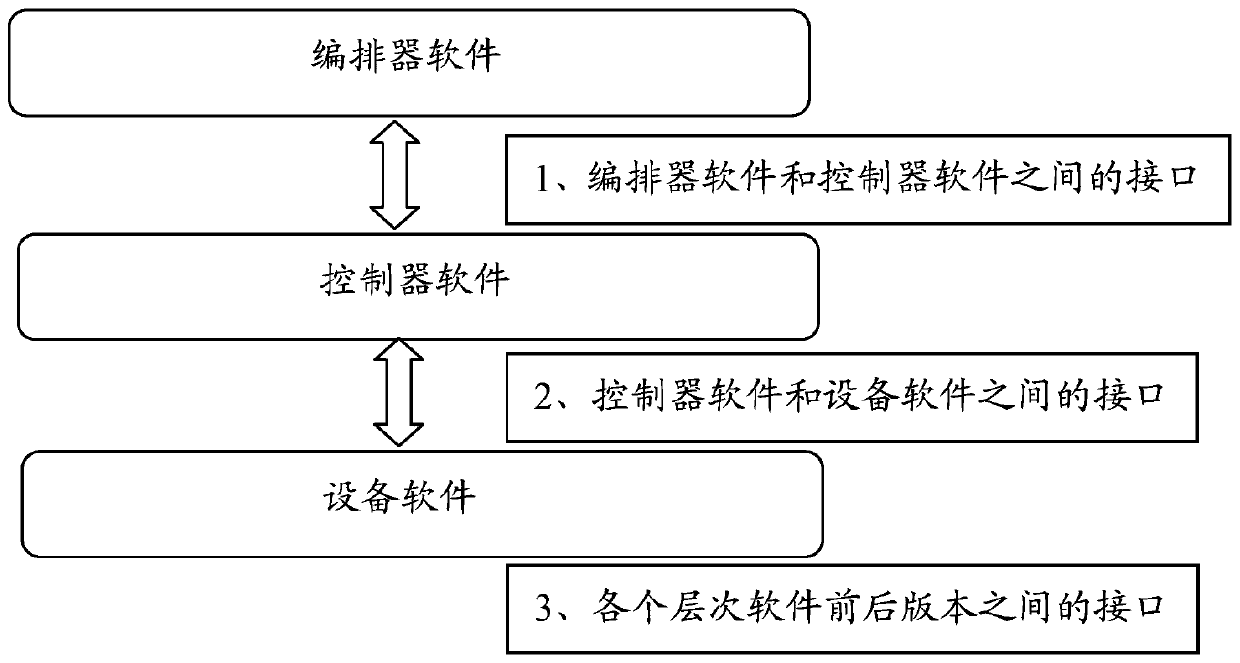
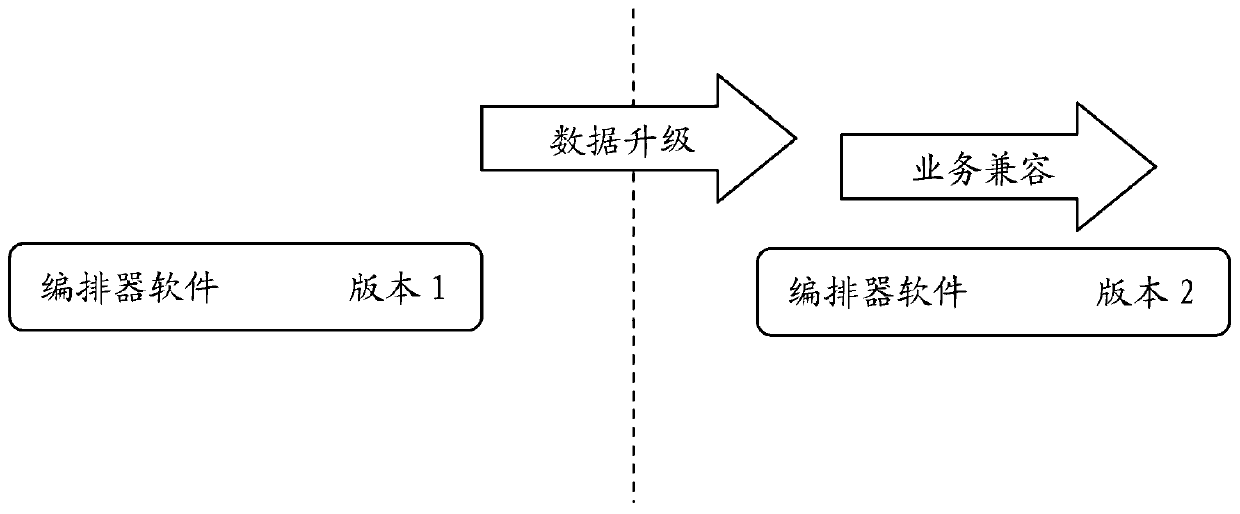
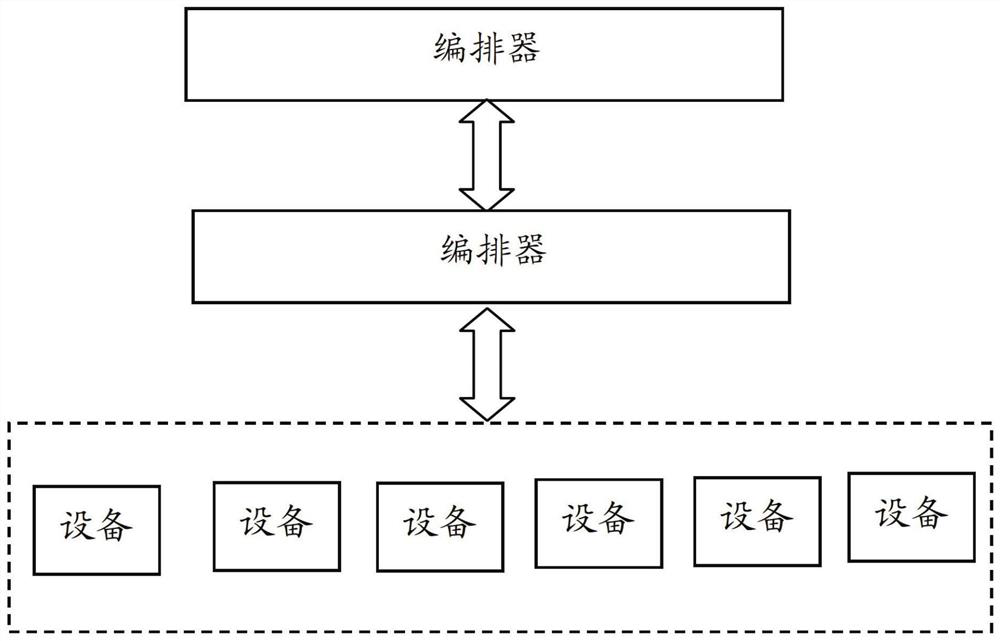
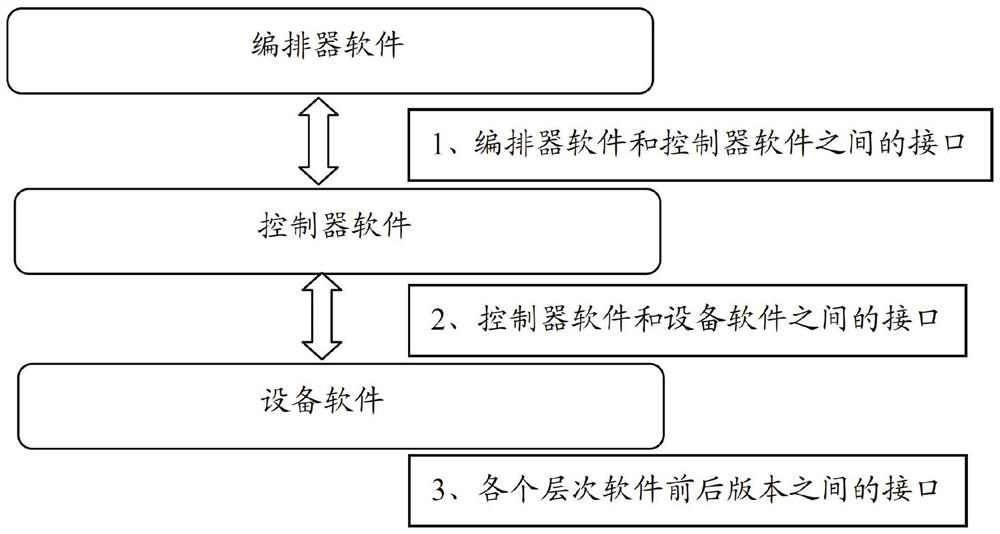
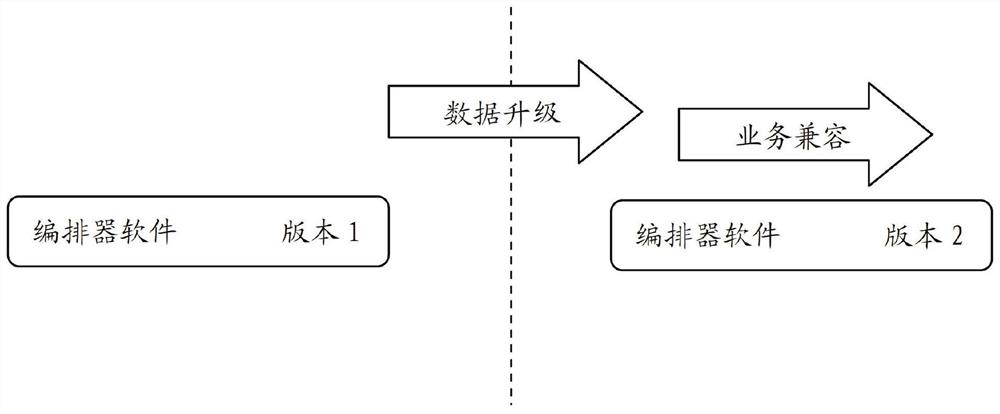
system and a method for realizing a software version smooth upgrading function for an SD-WAN system
ActiveCN109918109AEasy to upgradeReduce the pressure of upgrade operation and maintenanceVersion controlSoftware deploymentSoftware engineeringService configuration
The invention relates to a system and a method for realizing a software version smooth upgrading function for an SD-WAN system. The system comprises an orchestrator module, a controller module, an equipment module and an interface module. The controller module is connected with the orchestrator module and can perform service management configuration on the equipment modules with the multiple versions of software at the same time. The equipment module is connected with the controller module, is used for clearing the original configuration during upgrading, and is compatible with the service configuration issued by the controller module. The interface module is connected with the orchestrator module, the controller module and the equipment module. The invention also relates to a method for realizing a software version smooth upgrading function for an SD-WAN system. By adopting the system and a method for realizing a software version smooth upgrading function for an SD-WAN system, systemservices do not need to be rearranged, and smooth upgrading is realized. In the upgrading process, the service influence between the site devices is reduced to the minimum. An upgrading rollback scheme is provided, so that risks in an upgrading process are reduced.
Owner:CERTUS NETWORK TECHNANJING
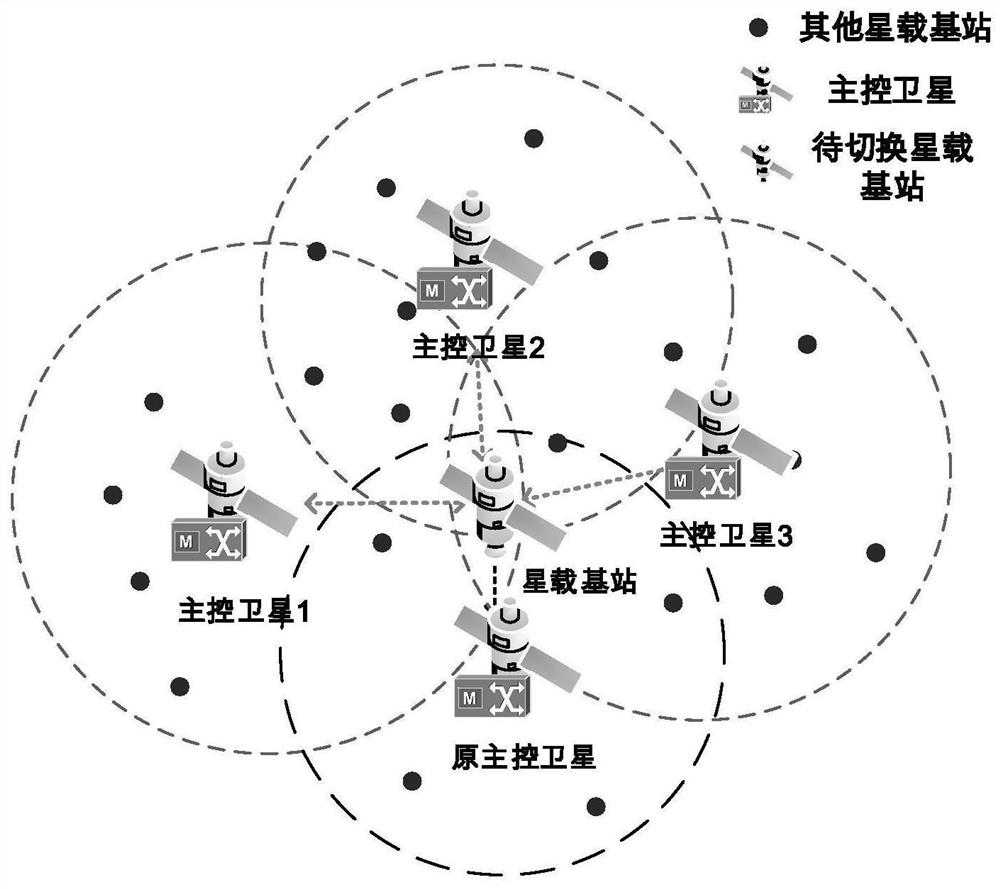
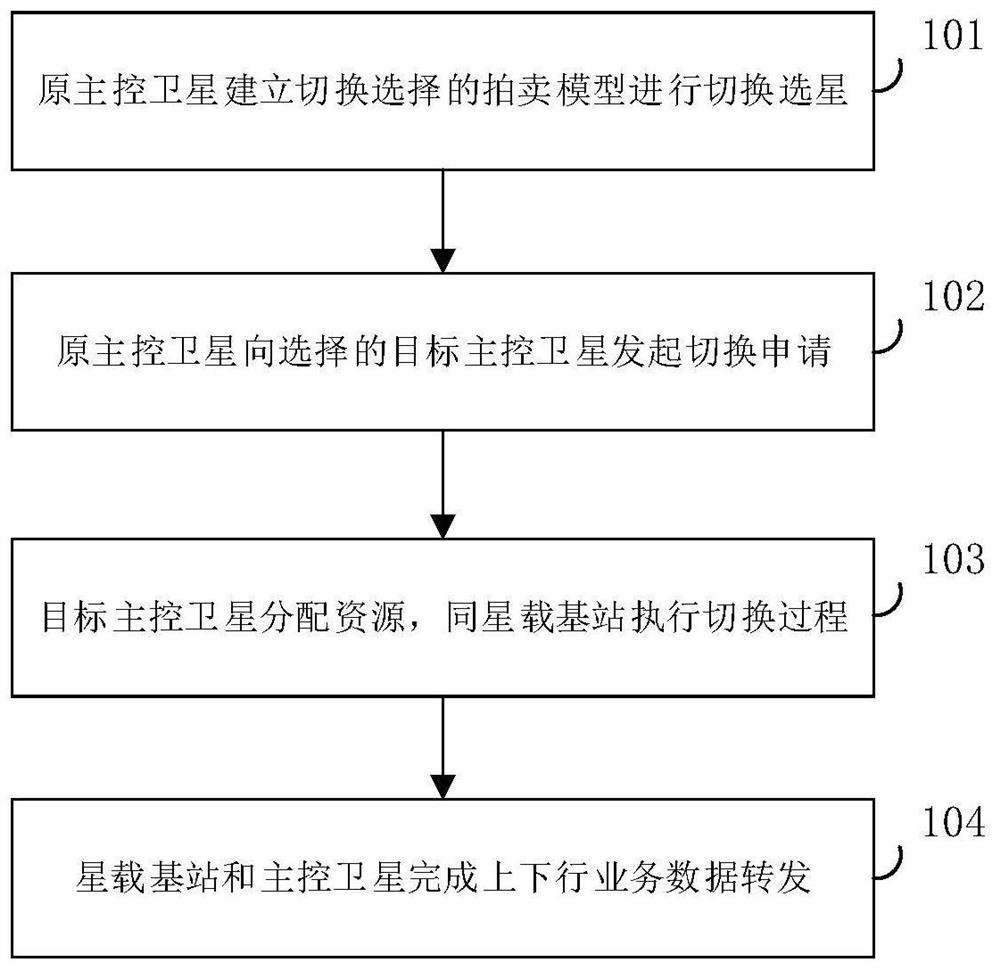
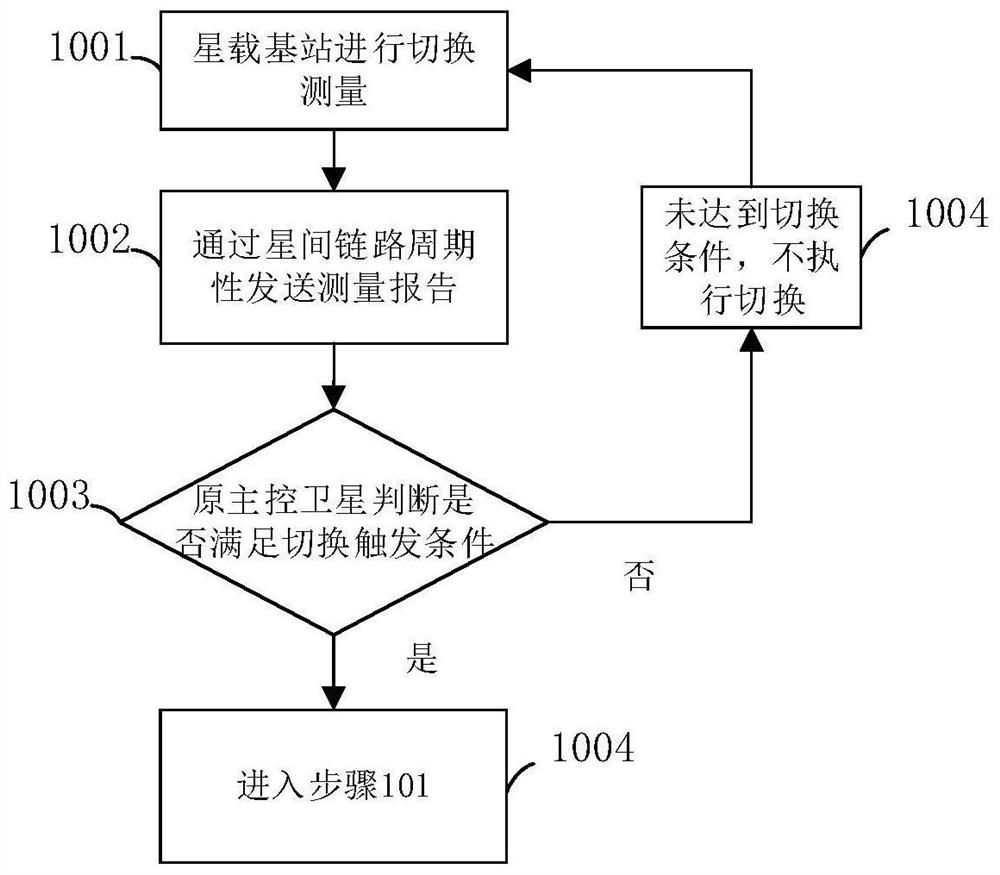
Satellite-ground fusion network-oriented satellite-borne base station switching management method
ActiveCN112887012AReduce switching frequencyLoad balancingNetwork traffic/resource managementNetwork topologiesSwitching frequencyRemote sensing
The invention relates to the field of satellite-ground fusion, in particular to a satellite-ground fusion network-oriented satellite-borne base station switching management method, which is applied among a satellite-borne base station, an original master control satellite and a target master control satellite and is used for realizing switching management of the satellite-borne base station under different satellite mobile subnetworks. The switching management method comprises the following steps: an original master control satellite of a satellite-borne base station establishes an auction model for switching selection; the original master control satellite initiates a switching application to a target master control satellite selected according to an auction model, the target master control satellite allocates resources, and meanwhile, the satellite-borne base station executes a switching process; and the satellite-borne base station and the master control satellite complete uplink and downlink data forwarding. Meanwhile, a switching selection algorithm is designed based on satellite measurement parameters, the switching frequency of the satellite-borne base station can be reduced, satellite node load balancing can be achieved, and service interruption is reduced.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
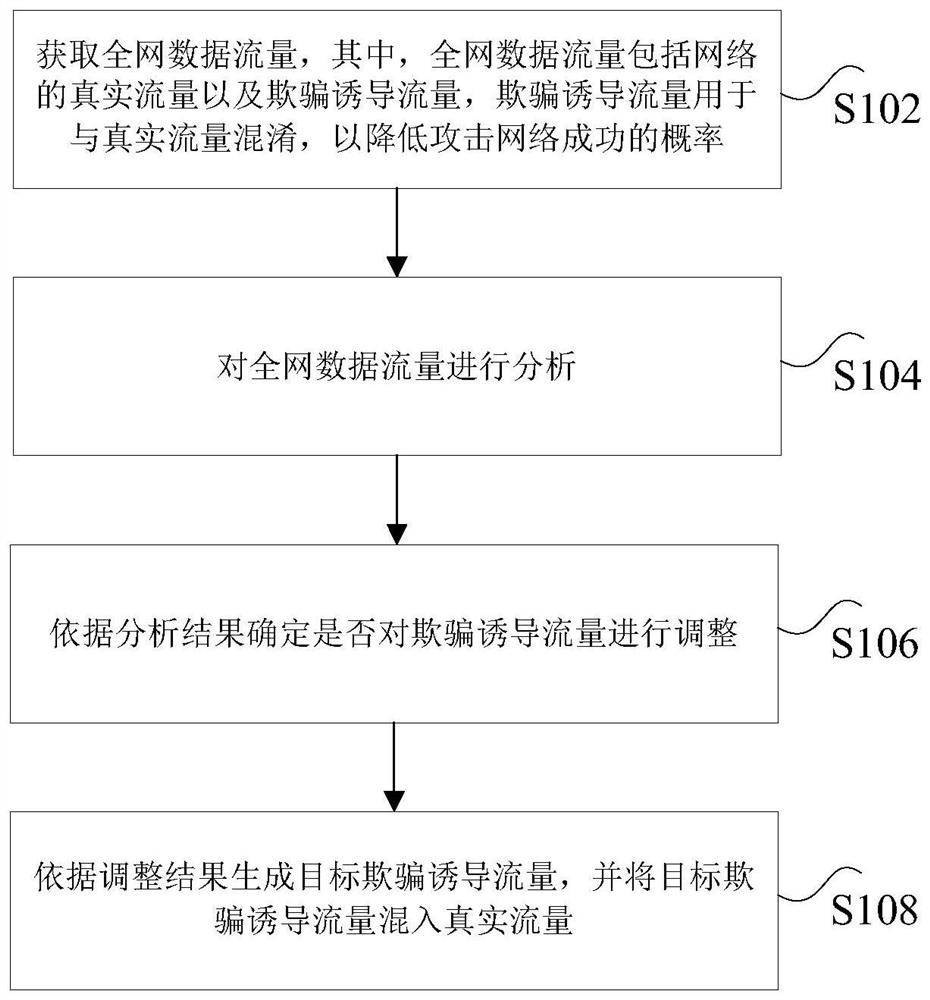
Method, device and system for generating data traffic
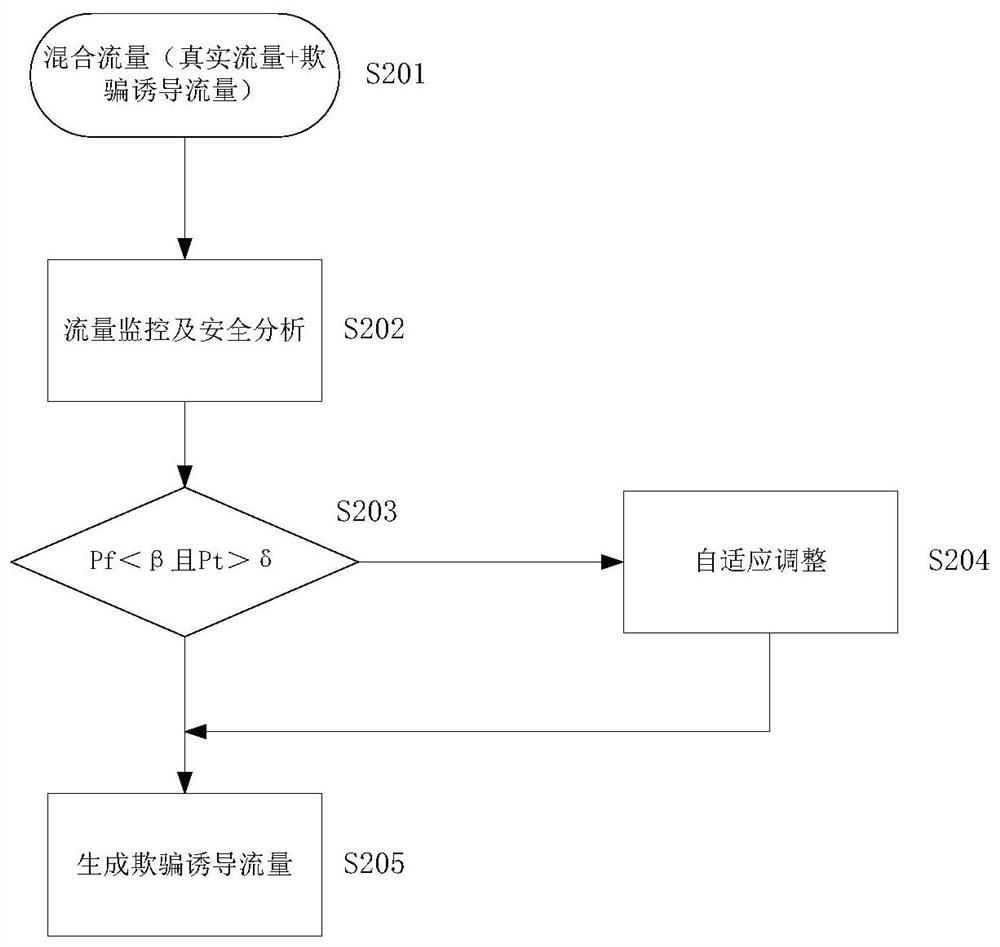
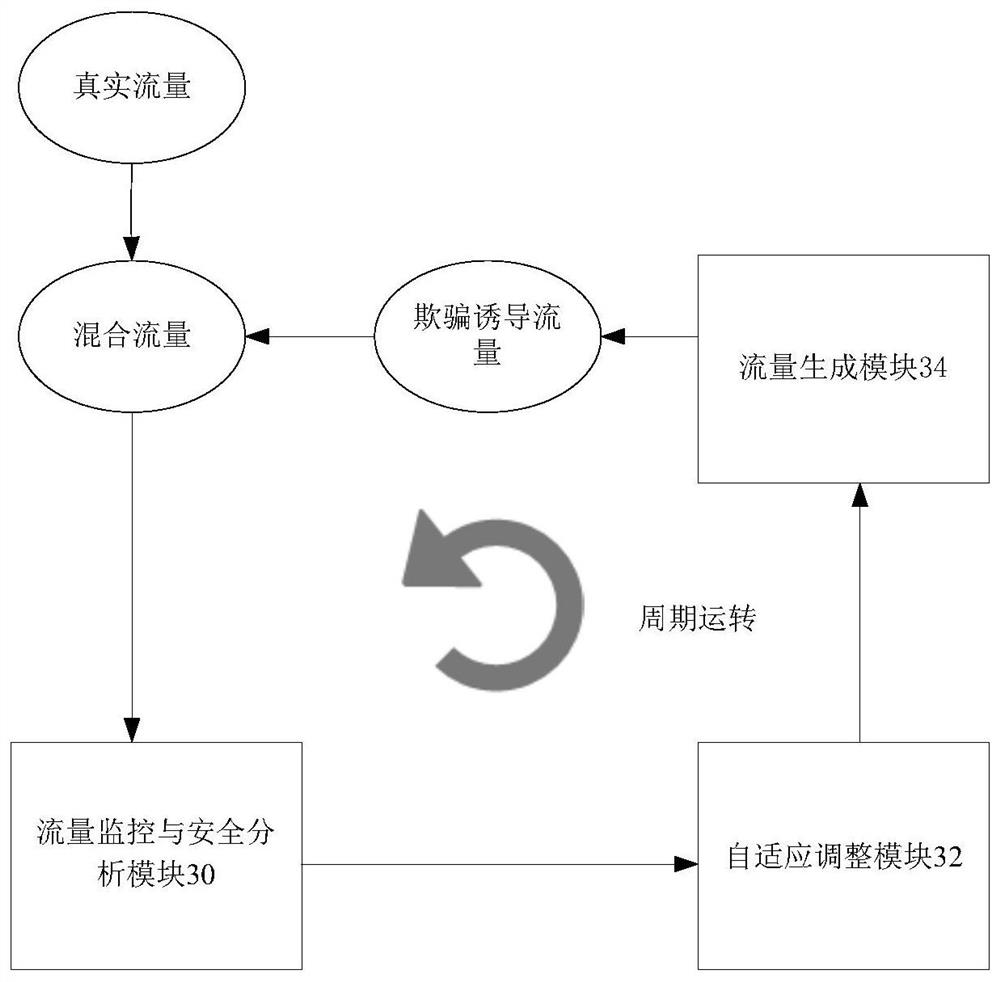
ActiveCN112822163ARealize adaptive adjustmentReduce business impactTransmissionHigh level techniquesNetwork dataNetwork attack
The invention discloses a method, device and system for generating data traffic. The method comprises the following steps: acquiring whole-network data traffic, wherein the whole-network data traffic comprises real traffic of a network and deception-induced traffic, and the deception-induced traffic is used for being confused with the real traffic so as to reduce the probability of network attack success; analyzing the whole-network data traffic; determining whether to adjust the deception-induced traffic according to the analysis result; and generating target deception-induced traffic according to an adjustment result, and mixing the target deception-induced traffic with real traffic. According to the invention, the technical problem that an existing traffic spoofing technology confusing network attacks is easy to be broken by attackers and cannot disperse too much attention of the attackers is solved.
Owner:HILLSTONE NETWORKS CORP
Method and device for deploying active-active mechanism of ORACLE database
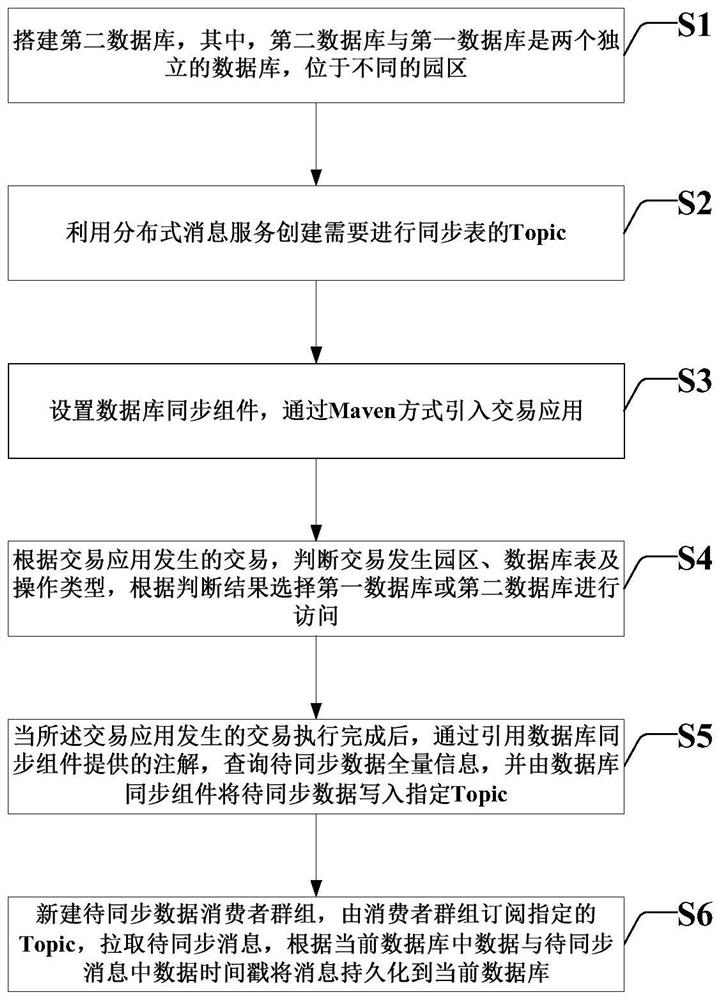
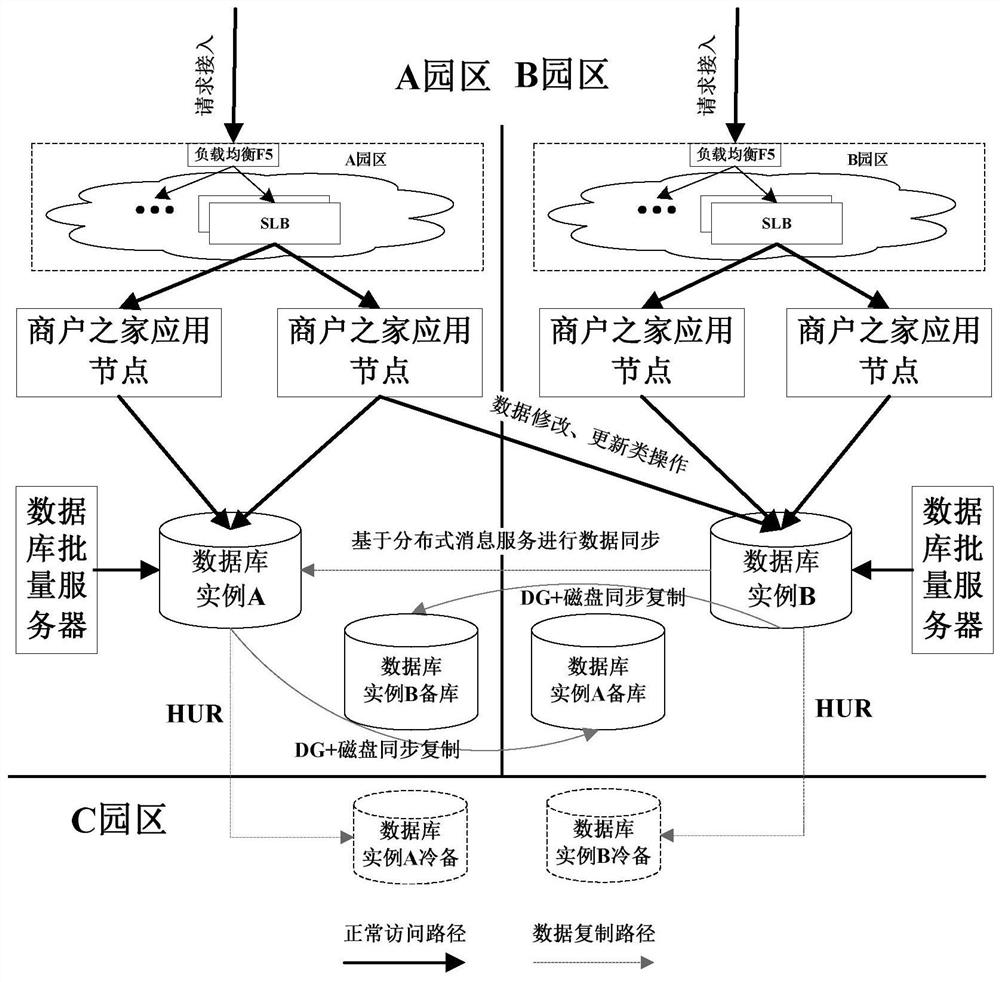
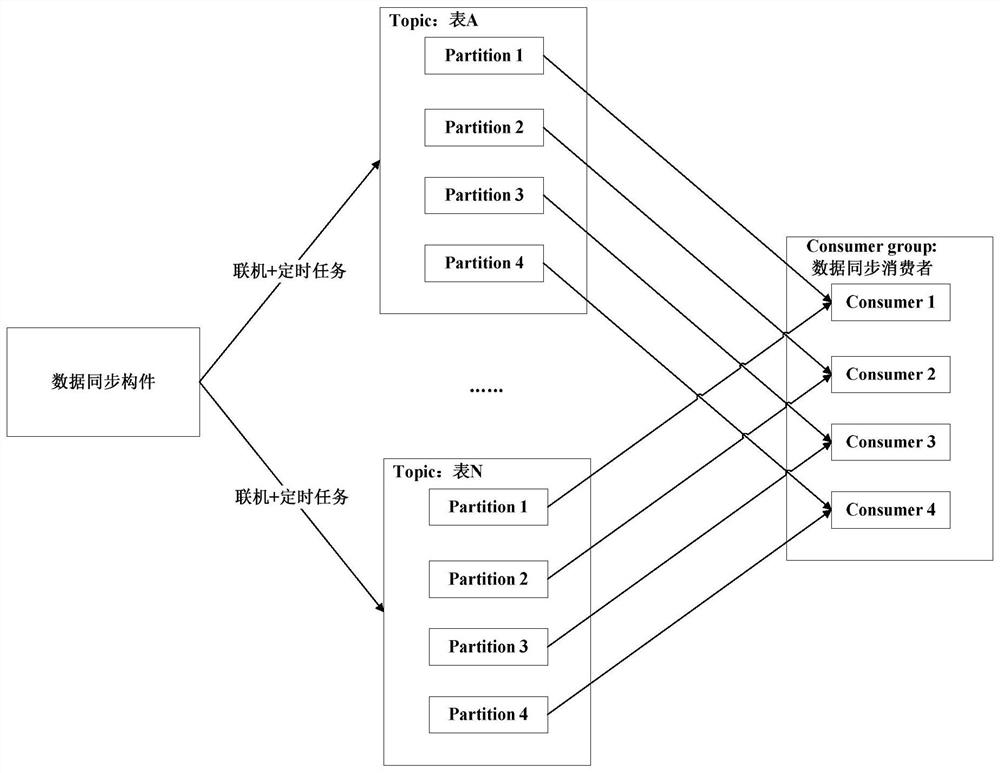
PendingCN113157701AReduce business impactImprove stabilityFinanceDatabase distribution/replicationCitation databaseFinancial transaction
The invention discloses an ORACLE database active-active mechanism deployment method and device, which can be used in the technical field of data processing, and the method comprises the following steps: building a second database; creating Topic which needs to be subjected to table synchronization by utilizing distributed message service; setting a database synchronization component, and introducing a transaction application in a Maven mode; according to a transaction generated by the transaction application, judging a transaction generation park, a database table and an operation type, and selecting a database for access according to a judgment result; after the transaction generated by the transaction application is executed, querying full-amount information of data to be synchronized by quoting an annotation provided by a database synchronization component, and writing the data to be synchronized into a specified Topic by the database synchronization component; creating a to-be-synchronized data consumer group, subscribing the specified Topic by the consumer group, pulling the to-be-synchronized message, and persisting the message to the current database according to the data in the current database and the data timestamp in the to-be-synchronized message.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
Network attack processing method and device
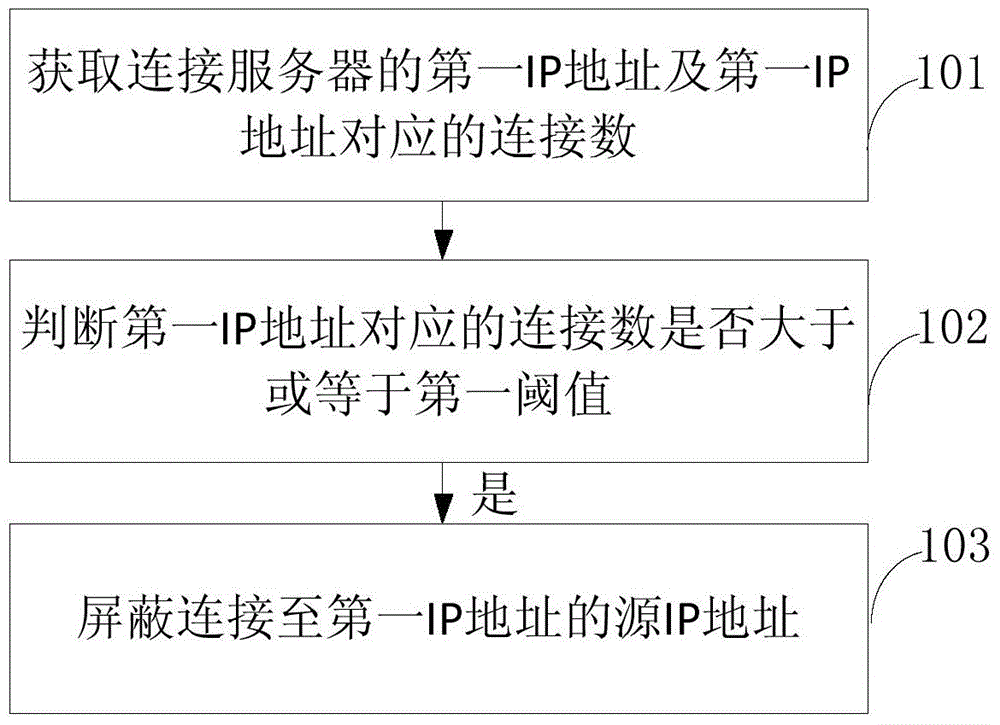
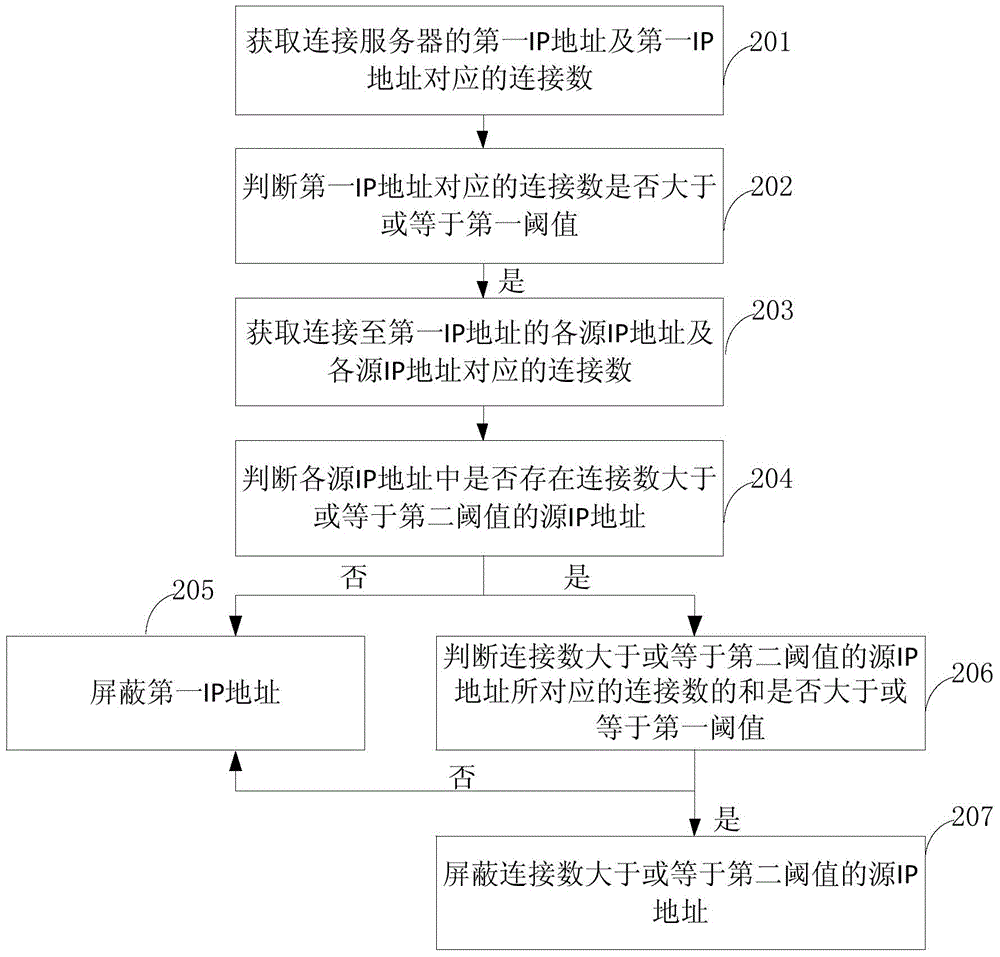
ActiveCN106302347AReduce business impactReduce the impact of accessSecuring communicationIp addressConnection number
The invention provides a network attack processing method and device The network attack processing method comprises steps of obtaining a first IP address connected to a server and a connection number corresponding to the first IP address, determining whether the connection number corresponding to the first IP address is greater than or equal to a first threshold value, if yes, shielding a source IP address connected to the first IP address. The embodiment of the network attack processing method and device not only guarantees integral stability of the server and the network, but also reduces influence on a service of an attacked IP address through shielding the source IP address, and reduces the influence on the network access.
Owner:ALIBABA GRP HLDG LTD
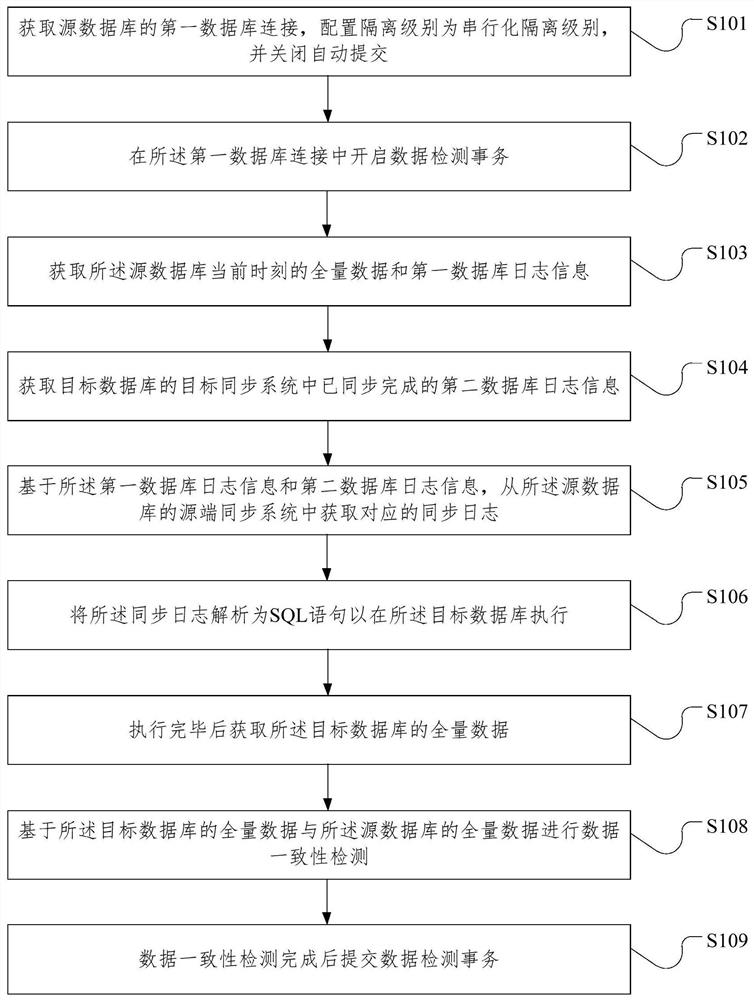
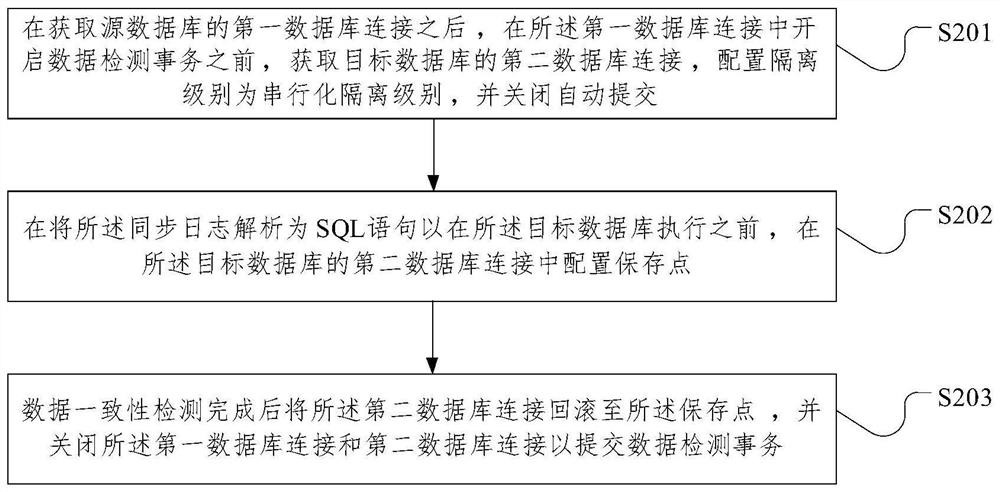
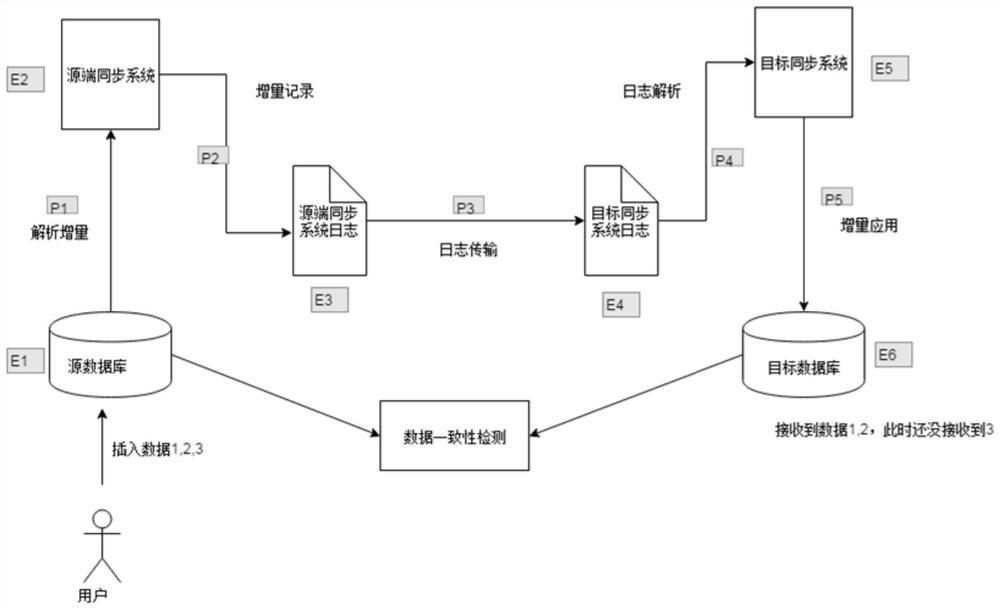
Database data consistency detection method and device, medium and electronic equipment
PendingCN112162989AReduce overheadGuaranteed performanceDatabase updatingDatabase distribution/replicationData miningDatabase connection
The invention relates to a database data consistency detection method and device, a medium and electronic equipment, and the method comprises the steps: obtaining a first database connection of a source database, configuring an isolation level as a serialization isolation level, and closing automatic submission; starting a data detection transaction in the first database connection; acquiring total data of the source database at the current moment and first database log information; acquiring synchronized second database log information in a target synchronization system of the target database; based on the first database log information and the second database log information, obtaining a corresponding synchronization log from a source end synchronization system of the source database; analyzing the synchronization log into an SQL statement to be executed in a target database; acquiring total data of the target database after the execution is finished; performing data consistency detection based on the total data of the target database and the total data of the source database; and submitting a data detection transaction after the data consistency detection is completed.
Owner:北京人大金仓信息技术股份有限公司 +1
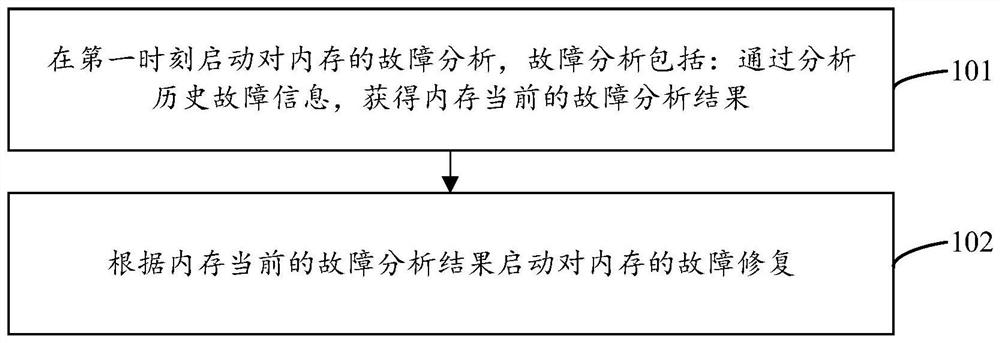
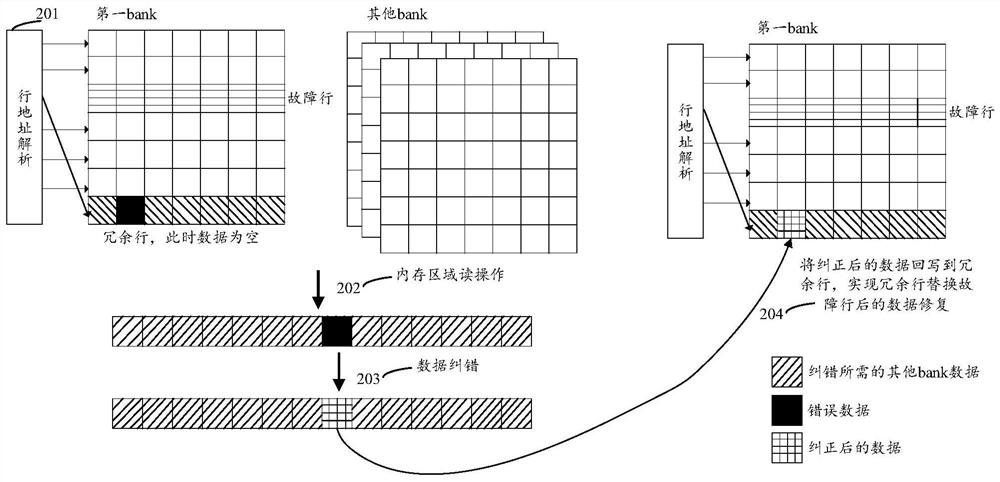
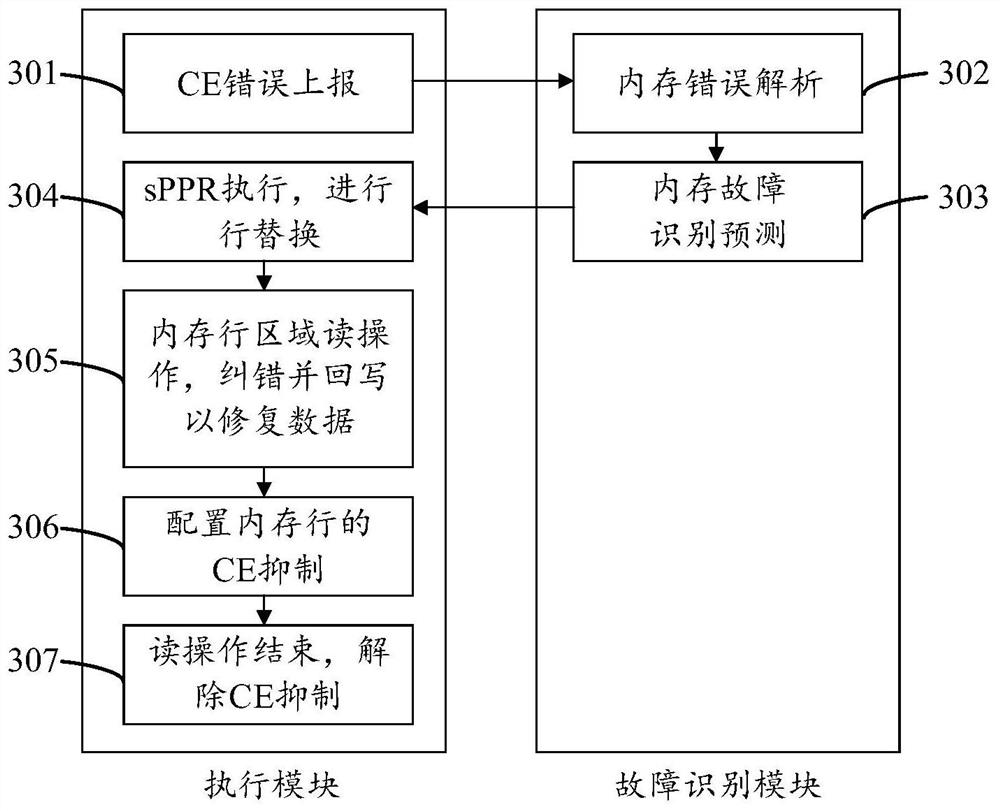
Memory fault processing method and device, equipment and storage medium
PendingCN113821364AAvoid downtimeReduce business impactNon-redundant fault processingStatic storageEmbedded systemFault analysis
The embodiment of the invention discloses a memory fault processing method and device, equipment and a storage medium, and belongs to the technical field of computers. In the embodiment of the invention, the fault analysis result is obtained by analyzing the historical fault information, and then the fault of the memory is repaired according to the fault analysis result, so that the memory fault can be analyzed more accurately. In addition, according to the scheme, memory fault repair can be started without cold reset, that is, memory faults can be repaired in time, system downtime is prevented, and service influences are reduced.
Owner:HUAWEI TECH CO LTD
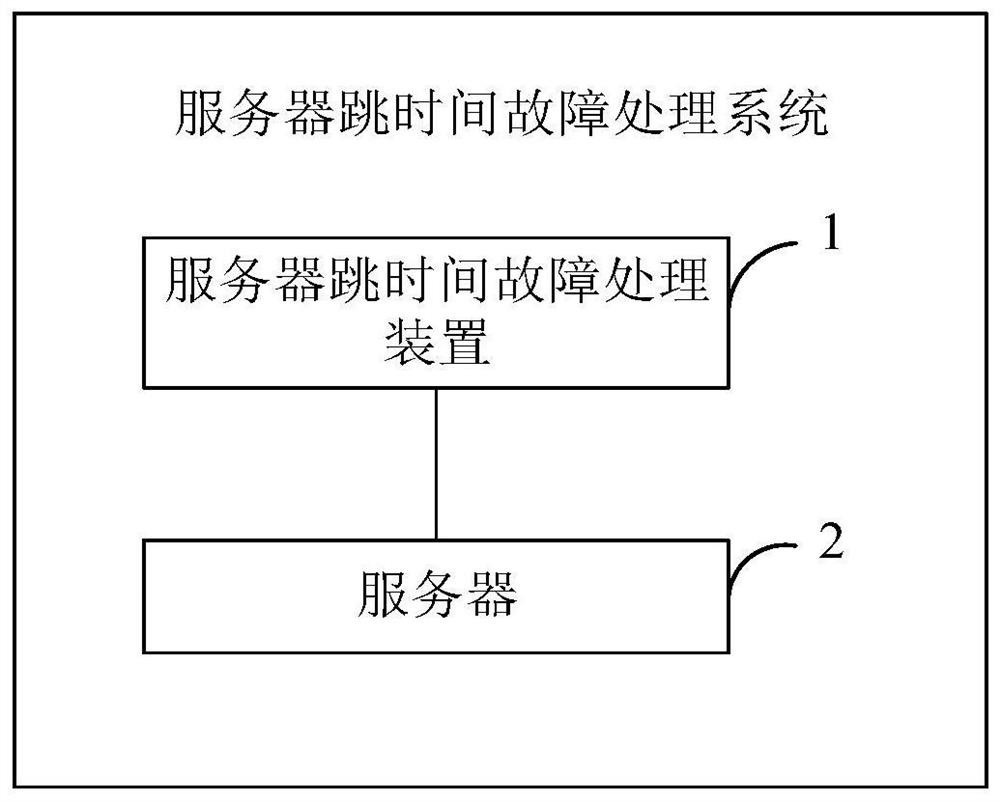
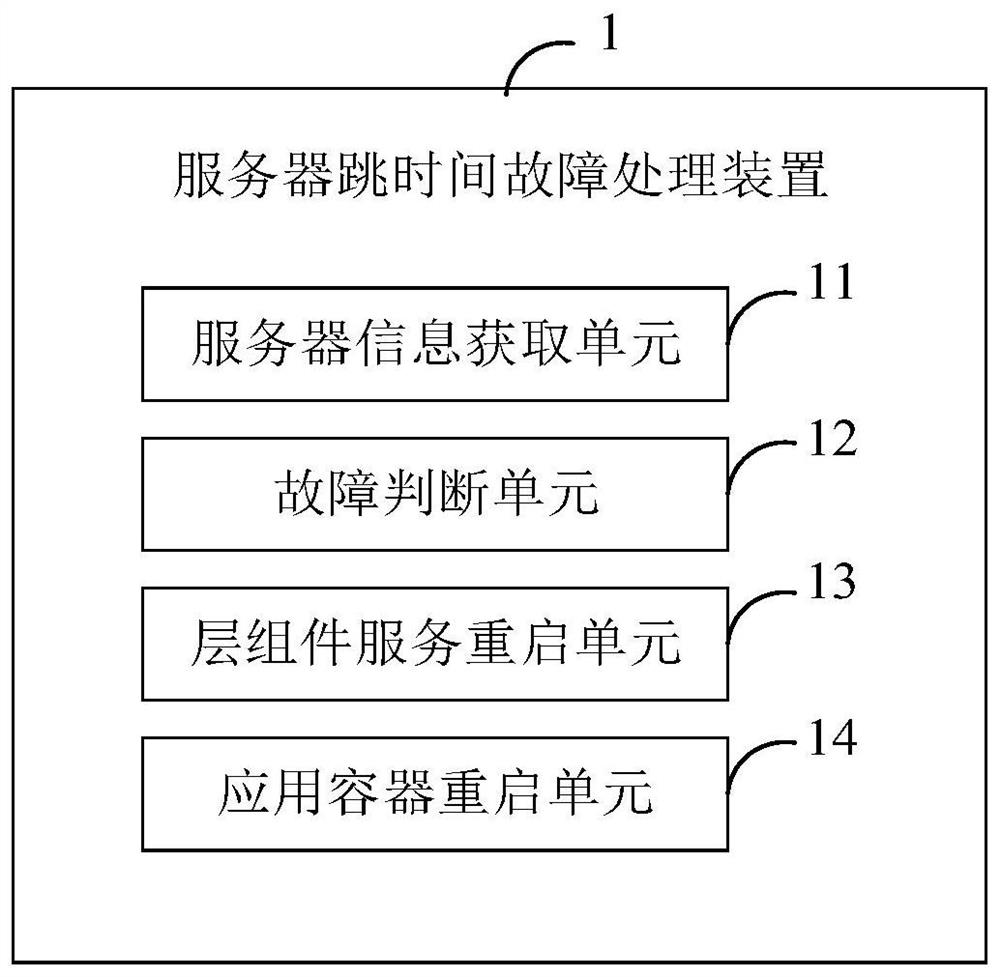
Cluster-based server time hopping fault processing method, device and system
PendingCN113157481AAutomated recovery from time-hopping faultsImprove efficiencyNon-redundant fault processingSoftware simulation/interpretation/emulationInformation securityCluster based
The invention discloses a cluster-based server time hopping fault processing method, device and system, and relates to the field of information security, the method comprises the following steps: obtaining server information in a cluster in response to triggering a server time hopping fault check operation, the server information comprising the current time of a server; judging whether the server has a time hopping fault or not according to the current time of the server on the basis of a preset rule; in response to the judgment result, performing a restart operation on a cluster layer component service corresponding to the server through a predetermined program; and after the cluster layer component service is restarted successfully and the server hop time fault is recovered, restarting an application container corresponding to the server. Through adoption of the method and the device, the time hopping fault of the server can be automatically recovered, manual operation is not needed, the efficiency is relatively high, and the influence on services is relatively small.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
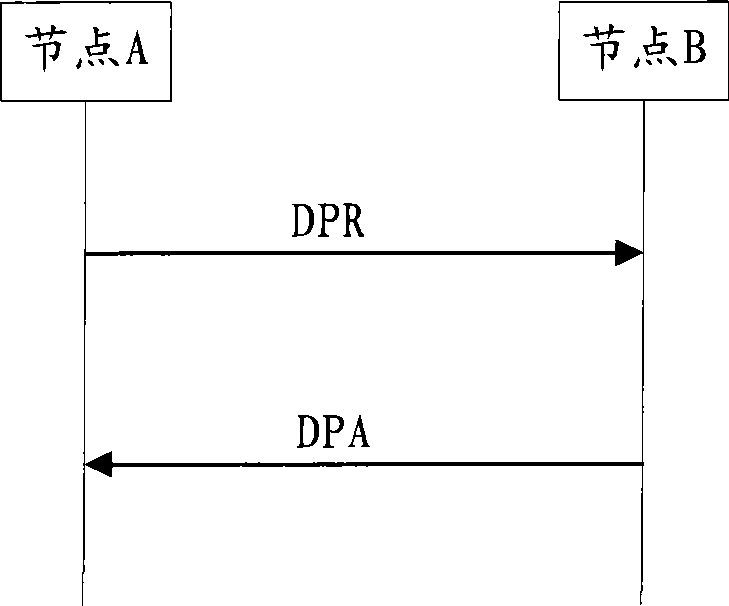
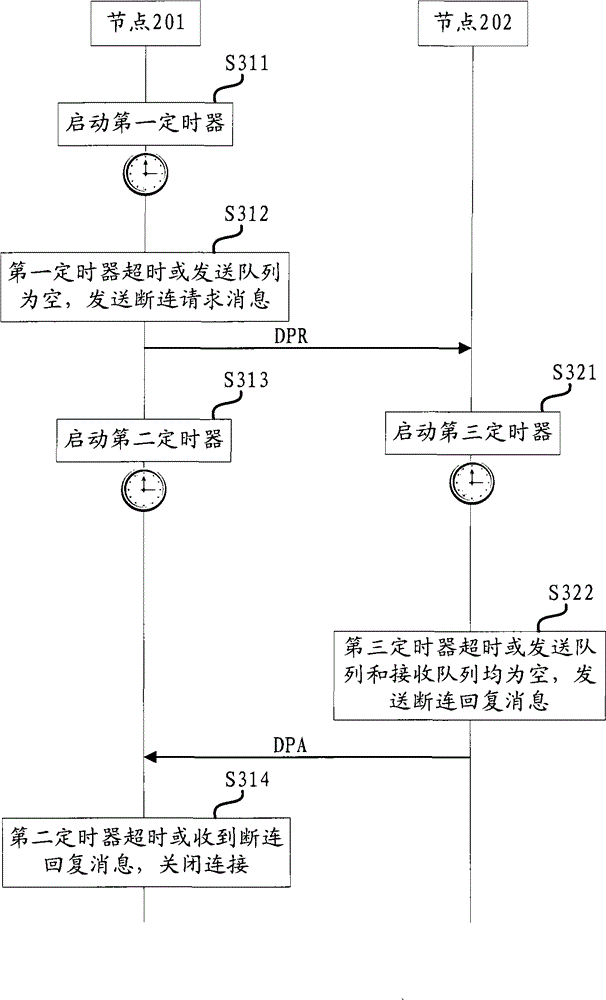
Method and device for closing Diameter connection
InactiveCN104601533AReduce in quantityReduce business impactConnection managementTransmissionTimerReal-time computing
The invention aims to provide a method and a device for closing Diameter connection. The first Diameter node starts the first timer, when the first timer overtimes or the transmit queue to be opened on connection is empty, sending the disconnection request message to the second Diameter node. Then, at one side of the second Diameter node, starting the third timer, when the third timer overtimes or the transmit queue to be opened on connection and the receiving queue are empty, sending the disconnection reply message to the first Diameter node. At one side of the first Diameter node, the second timer is started, and breaking the Diameter connection when the second timer overtimes or receives the disconnection reply message. The number of the failure can be obviously reduced through the method and the device, under reasonable setting of the timer, the ideal effect without failure message can be achieved and the QoS and stability of the system can be raised.
Owner:ALCATEL LUCENT SAS
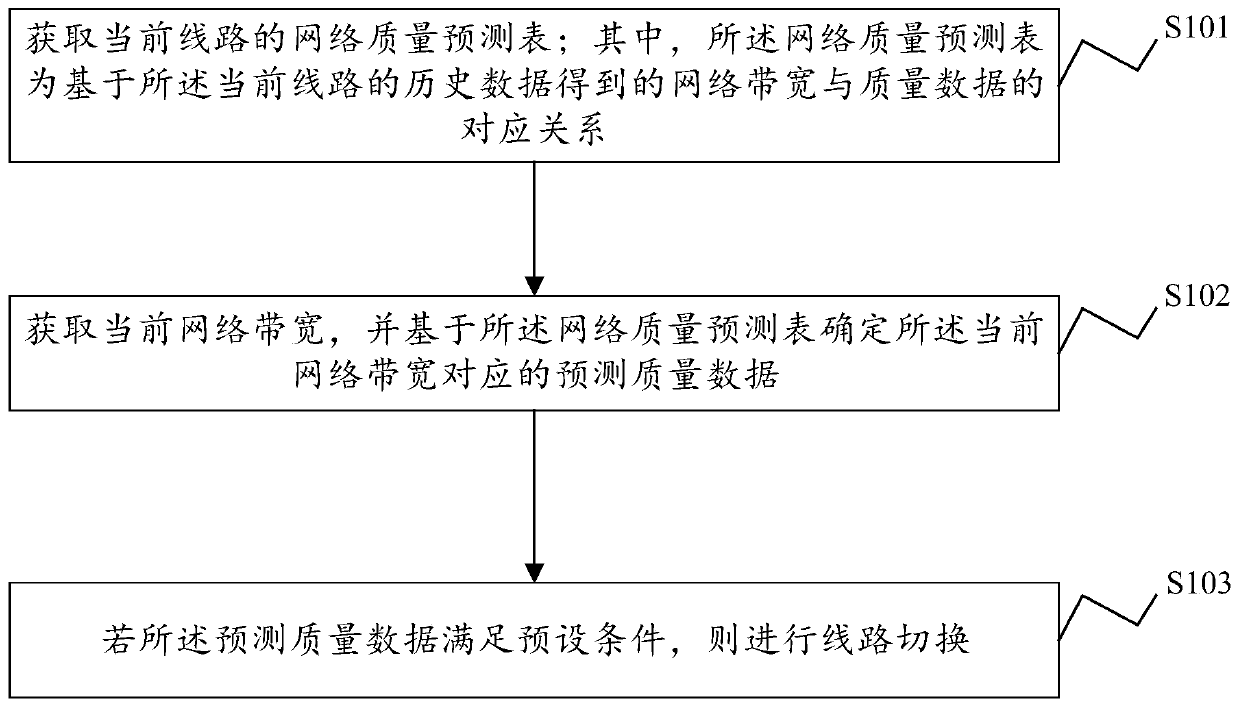
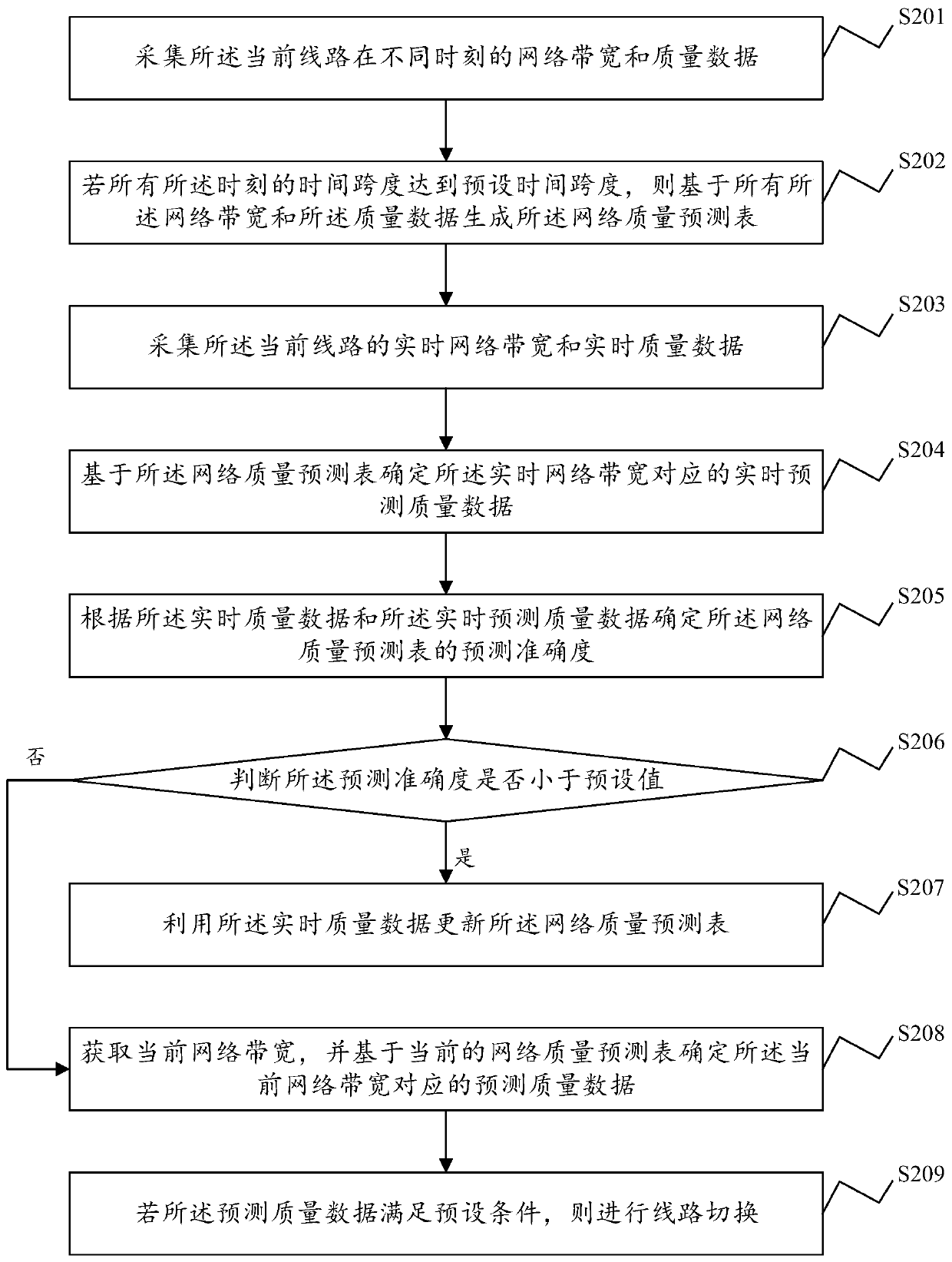
Network quality monitoring method and device, electronic equipment and storage medium
ActiveCN111404773AReduce business impactWith hysteresisData switching networksQuality dataEngineering
The invention discloses a network quality monitoring method and device, electronic equipment and a computer readable storage medium. The method comprises the steps of obtaining a network quality prediction table of a current line, wherein the network quality prediction table representing corresponding relationship between the network bandwidth and the quality data obtained based on the historicaldata of the current line; obtaining a current network bandwidth, and determining predicted quality data corresponding to the current network bandwidth based on the network quality prediction table; and if the prediction quality data satisfies a preset condition, carrying out line switching. According to the network quality monitoring method provided by the invention, line quality model predictionis carried out depending on historical data to obtain the network quality prediction table of the current line, and the network quality prediction table can identify possible degradation of the network quality in advance and make a response in advance, so that influence on the service is relatively small.
Owner:SANGFOR TECH INC
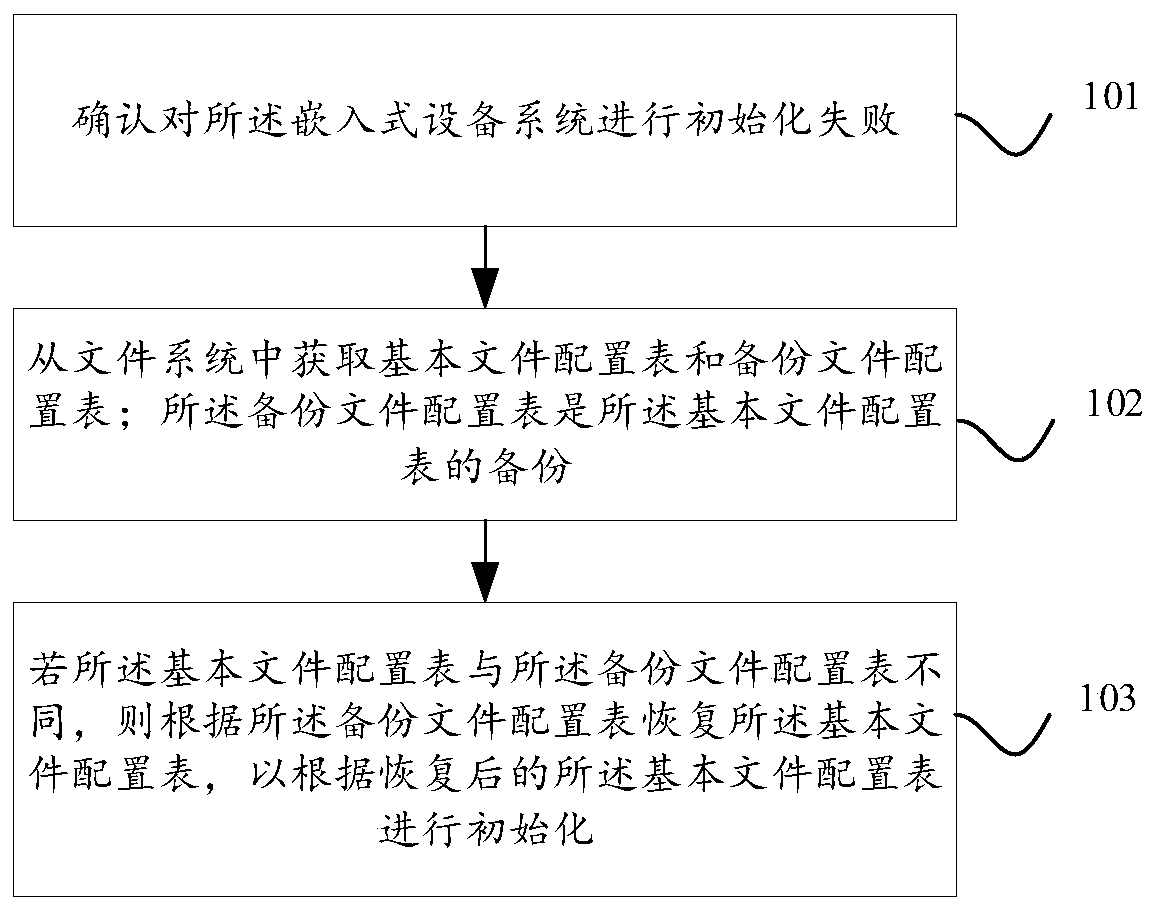
File recovery method, device and equipment and storage medium
InactiveCN110795281AReduce business impactReduce maintenance costsBootstrappingFile system administrationOperational systemFile system
The invention provides a file recovery method and device, equipment and a storage medium. The method comprises the following steps: determining that the initialization of an embedded equipment systemfails at a boot initialization stage of the embedded equipment system; obtaining a basic file configuration table and a backup file configuration table from a file system; wherein the backup file configuration table is a backup of the basic file configuration table; If the basic file configuration table is different from the backup file configuration table, recovering the basic file configurationtable according to the backup file configuration table so as to perform initialization according to the recovered basic file configuration table. According to the method, the damaged file configuration table is automatically repaired by the embedded equipment in the system boot initialization stage, so that the operating system can be normally started, the service influence on the online equipmentis reduced, the maintenance efficiency is improved, and the maintenance cost is reduced.
Owner:HANGZHOU DPTECH TECH
Information sending method, device and equipment and readable storage medium
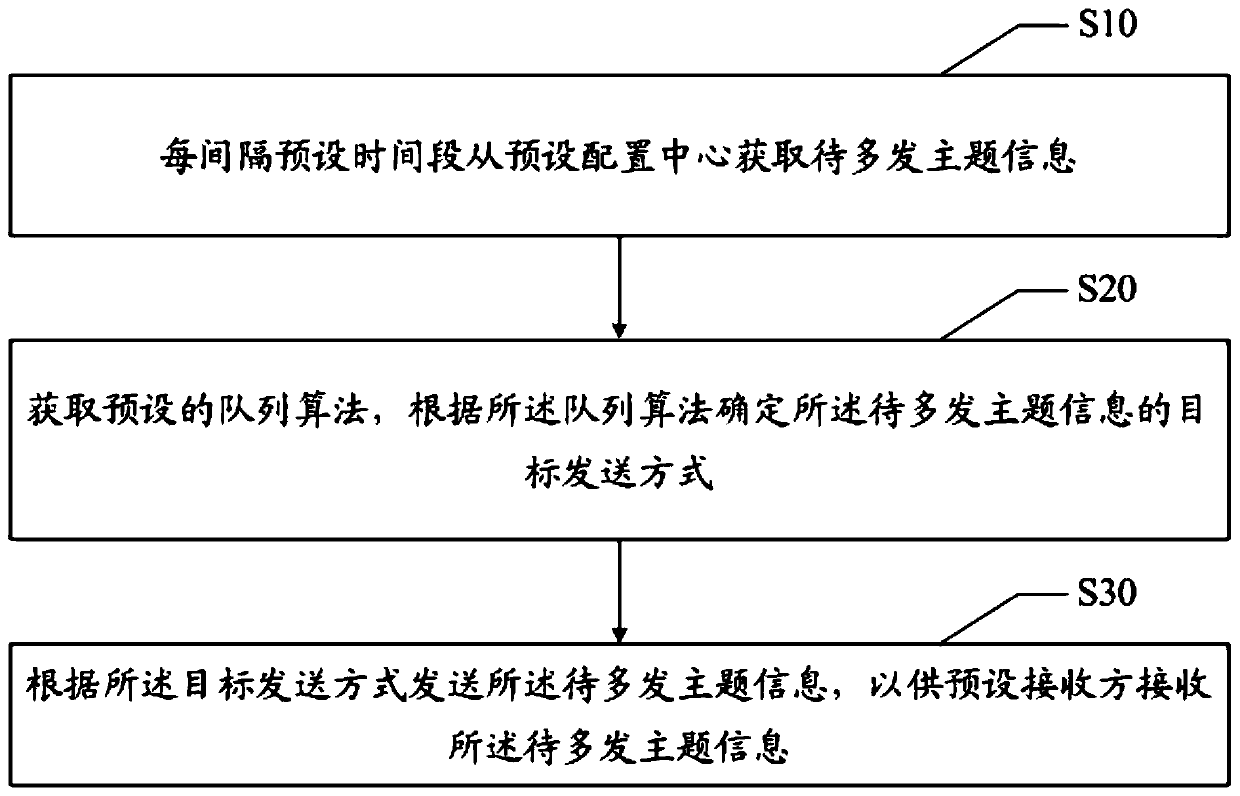
PendingCN110247808AAvoid transaction failureTransaction failure will notFinanceInterprogram communicationReal-time computing
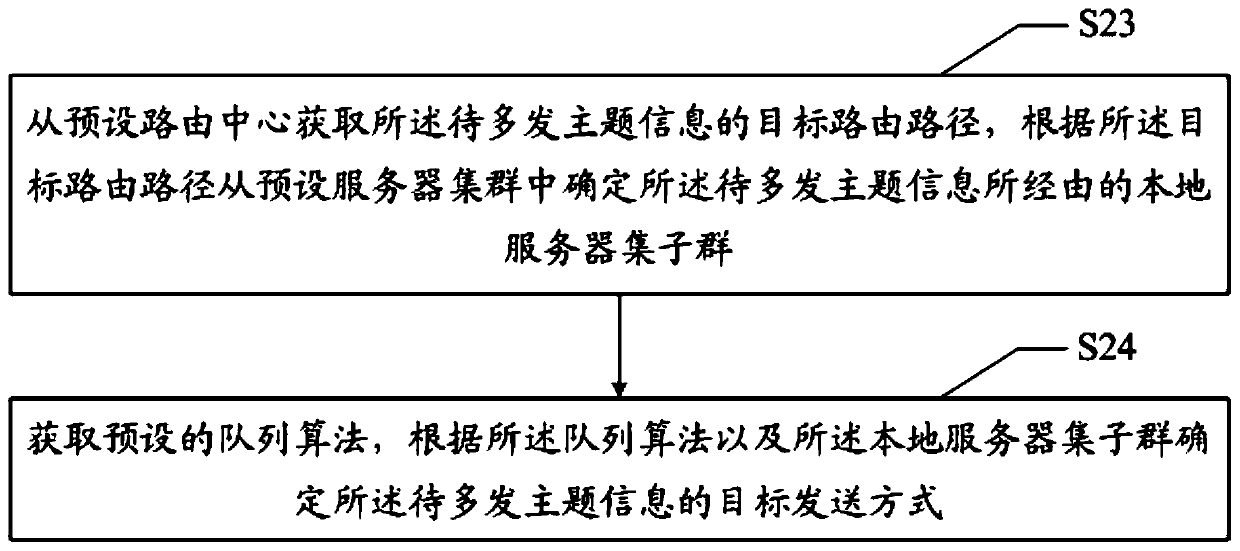
The invention discloses an information sending method, device and equipment and a readable storage medium, and relates to the field of financial institutions, the method comprises the following steps: obtaining to-be-sent theme information from a preset configuration center at intervals of a preset time period; obtaining a preset queue algorithm, and determining a target sending mode of the to-be-sent theme information according to the queue algorithm; and sending the to-be-sent theme information according to the target sending mode, so that a preset receiver receives the to-be-sent theme information. According to the invention, the number of times of information sending failure is reduced, and the service influence caused by server failure is reduced.
Owner:WEBANK (CHINA)
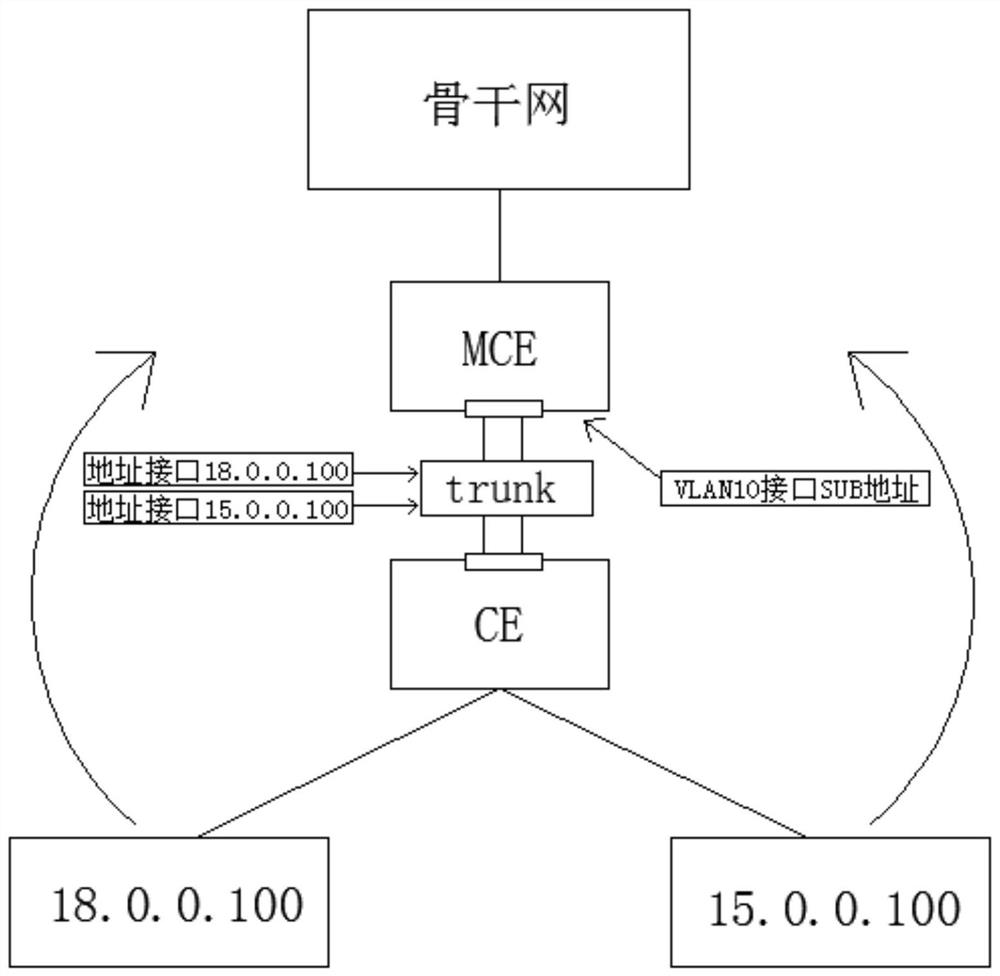
New and old IP address interconnection method for marine information communication network
The invention discloses a new and old IP address interconnection method for a marine information communication network. The method comprises the steps: A, removing a private network router of an original business address, and enabling MCE to be connected with a backbone network; B, creating an original service VLAN on the MCE; C, creating a virtual interface on the original service VLAN; and D, configuring a main IP address on the virtual interface to serve as a gateway of a first network segment and a slave IP address to serve as a gateway of a second network segment. According to the invention, the interconnection of new and old IP addresses are realized, the window cutover time is effectively shortened, the transition is smooth, the low service influence is ensured, and the smooth development of the network integration work of the marine information communication network is ensured.
Owner:NAT MARINE DATA & INFORMATION SERVICE
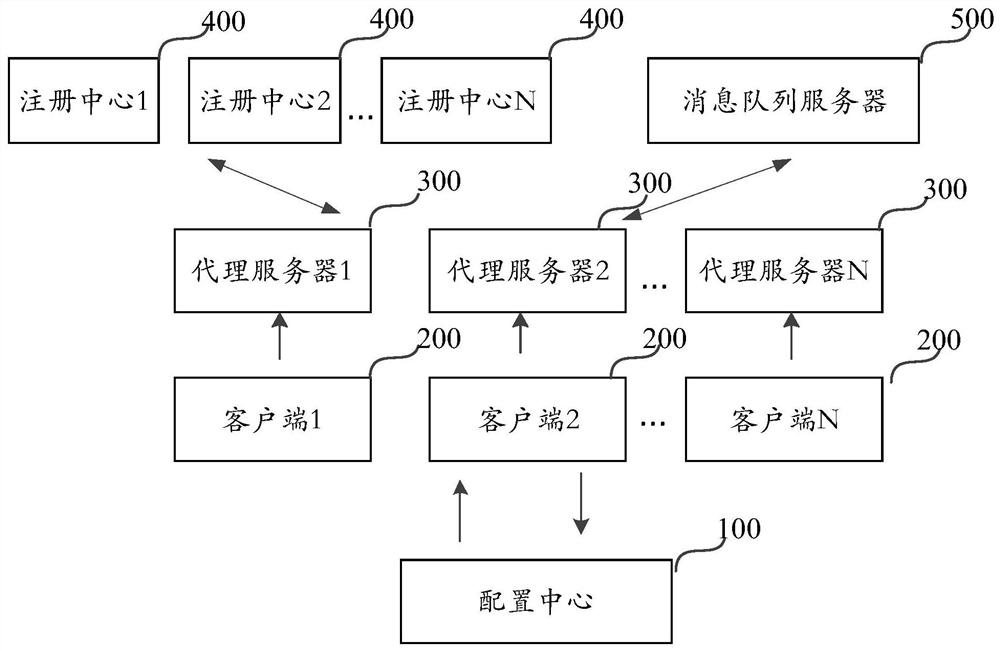
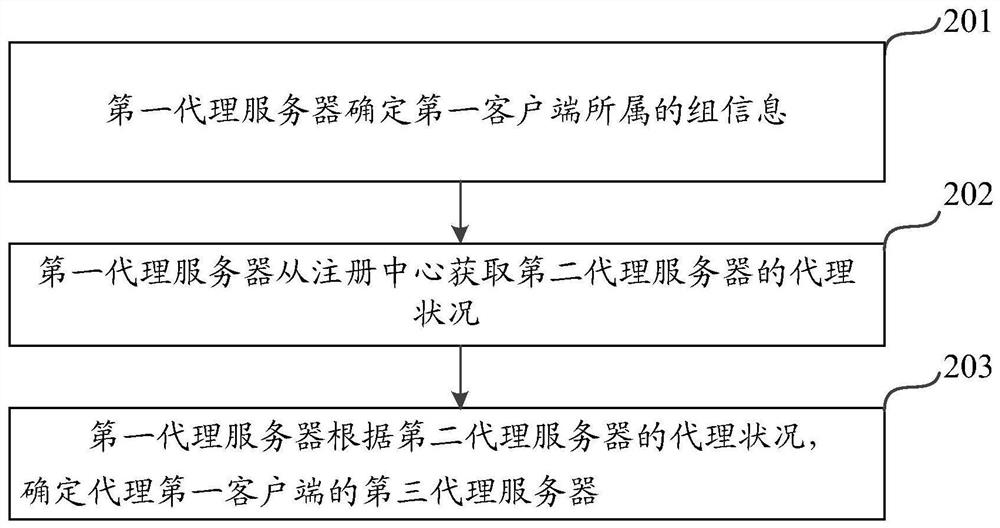
Message receiving and sending method and device
PendingCN111654527AImprove the efficiency of sending and receiving messagesEvenly distributedData switching networksEngineeringProxy server
The invention relates to the field of Fintech. The invention further discloses a message receiving and sending method and device. The method comprises the following steps: a first proxy server determines group information to which a first client belongs, the first proxy server acquires the agency condition of a second proxy server from a registration center, wherein the current agented client of the second proxy server comprises a second client with group information, the agency condition is used for indicating the condition of the second client, and the first proxy server determines a third proxy server agenting the first client according to the agency condition of the second proxy server. According to the invention, the received and sent messages with the same group information are distributed to different proxy servers in a relatively balanced manner, and the service influence caused by the failure of the proxy servers is reduced.
Owner:WEBANK (CHINA)
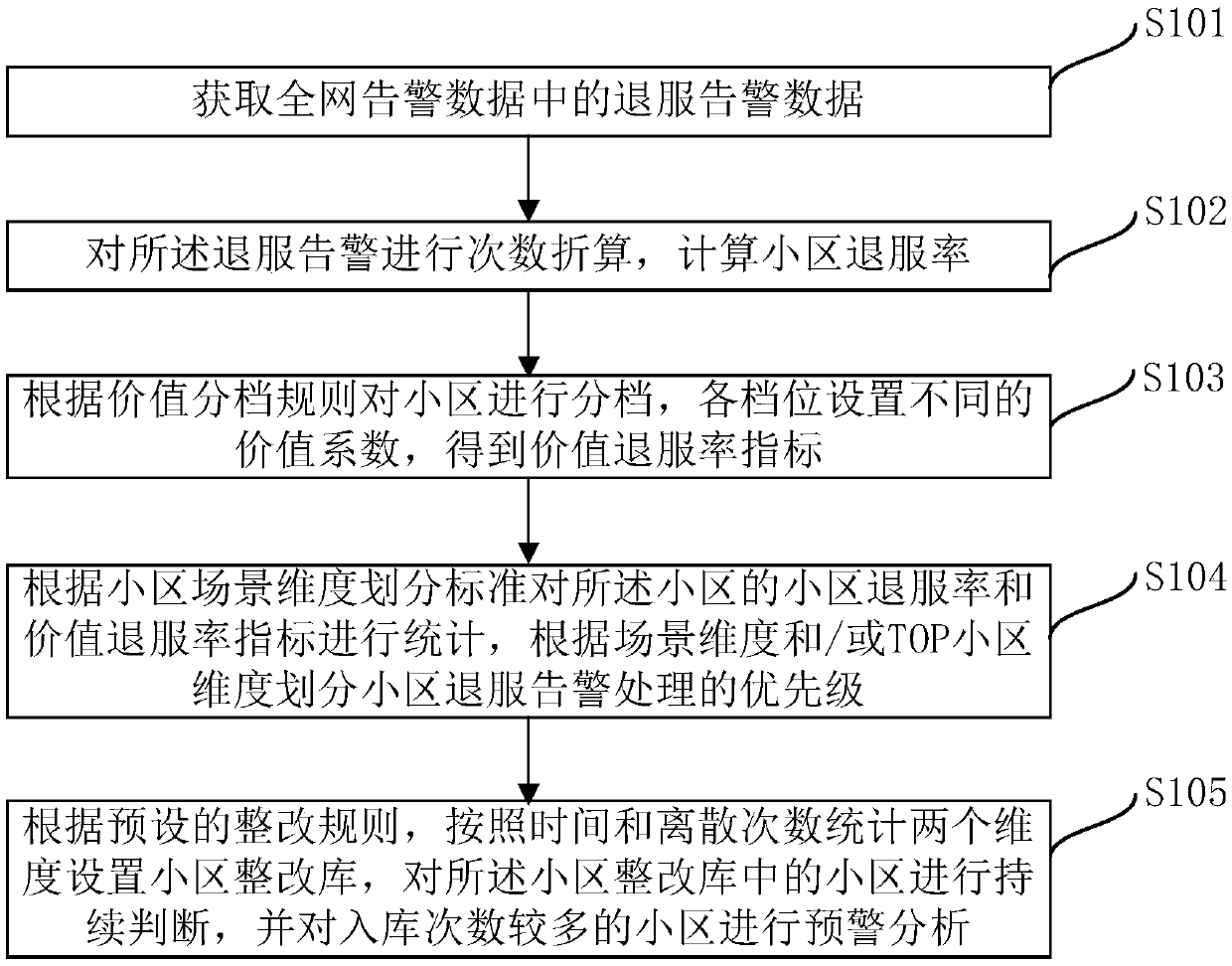
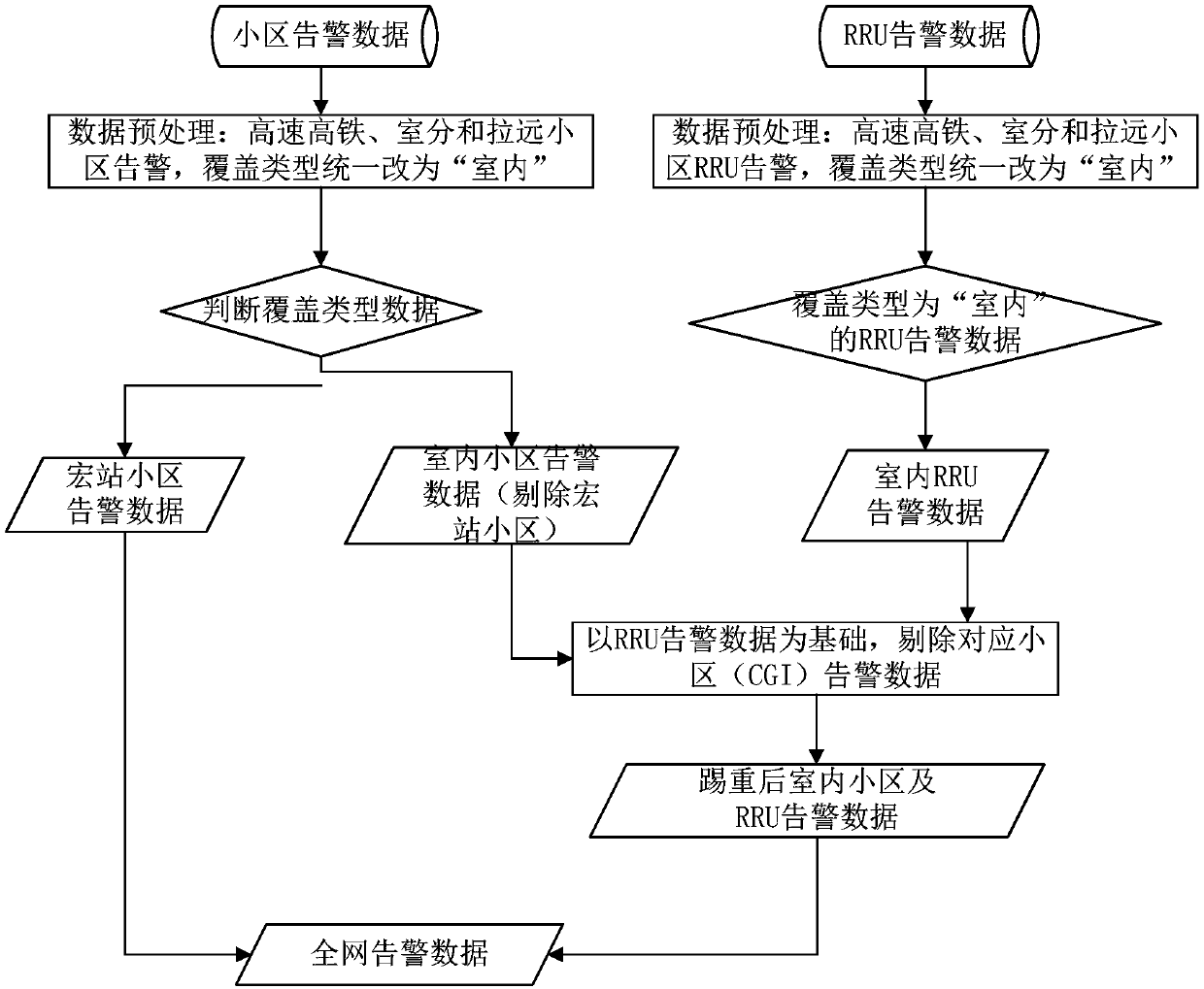
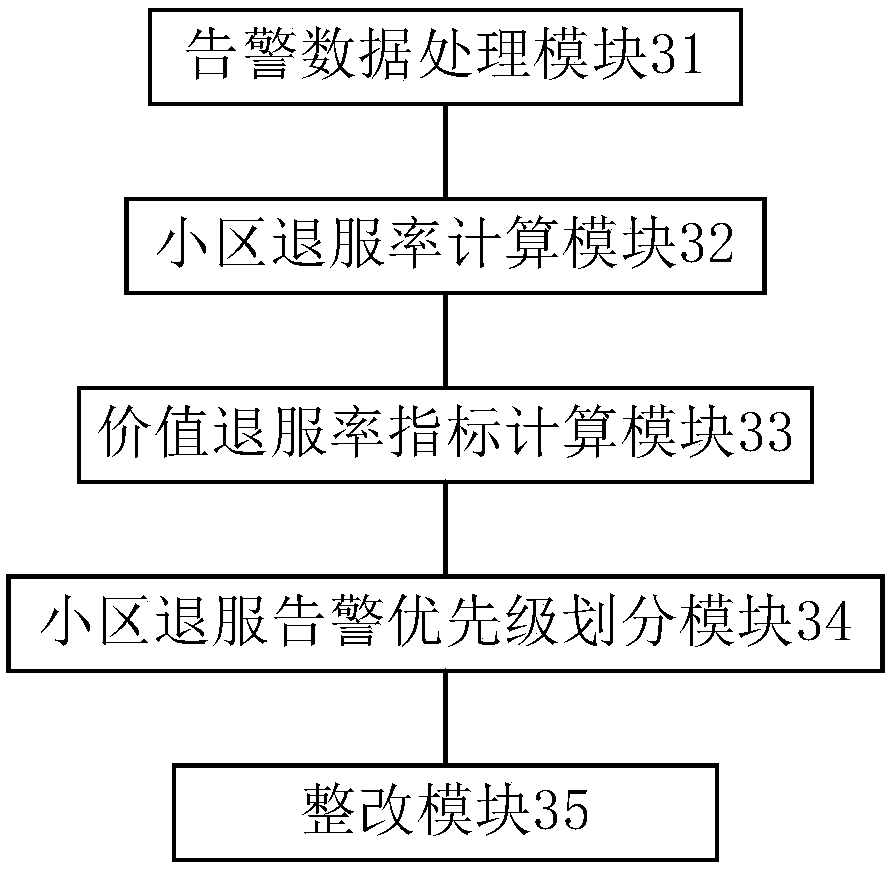
A frequency conversion-based out-of-service alarm analysis processing method and system
ActiveCN109787786APrecise PrioritizationFacilitate intelligent analysisData switching networksHigh level techniquesCell processingFrequency conversion
The invention provides a frequency conversion-based out-of-service alarm analysis processing method and system, and the method is characterized in that the method comprises the steps: obtaining out-of-service alarm data in whole-network alarm data; Performing frequency conversion on the out-of-service alarm, and calculating a cell out-of-service rate; Grading the cell according to a preset value grading rule to obtain a value out-of-service rate index of the cell; According to a cell scene dimension division standard, carrying out statistics on a cell service rejection rate and a value servicerejection rate index of the cell; And according to a preset rectification rule, two dimensions are counted according to time and the number of discrete times to set a cell rectification library, cells in the cell rectification library are continuously judged, and early warning analysis is carried out on the cells with more warehousing times. Based on intelligent analysis and early warning of bigdata influencing service alarm, high-value cell accurate priority processing is realized; And establishing a rectification library mechanism, and carrying out long-term effective tracking and early warning on a cell processing effect.
Owner:BOCO INTER TELECOM
Method, device and system for data processing
The present invention discloses a data processing method, device and system, and relates to the Internet technology field. The problem can be solve d that a current limiting strategy cannot satisfy demands of business sides at present. The method comprises: obtaining the maximum capacity of user access being subjected to concurrent processing by the server of a business side; establishing a business data model comprising concurrence access volume corresponding to different business data ranges; establishing a resource restriction model comprising access restriction probability corresponding to different business data ranges according to the maximum capacity and the business data model, wherein the access restriction probability is obtained according to the maximum capacity to allow the server of the business side to perform restriction of user access in different business data ranges according to the business strategy of the business side; and sending the resource restriction model to the server of the business side to allow the server of the business side to perform current limiting operation according to the resource restriction model. The data processing method, device and system are mainly suitable in the scenes of online transaction.
Owner:ADVANCED NEW TECH CO LTD
Self-adaptive flow control method and device, computing equipment and storage medium
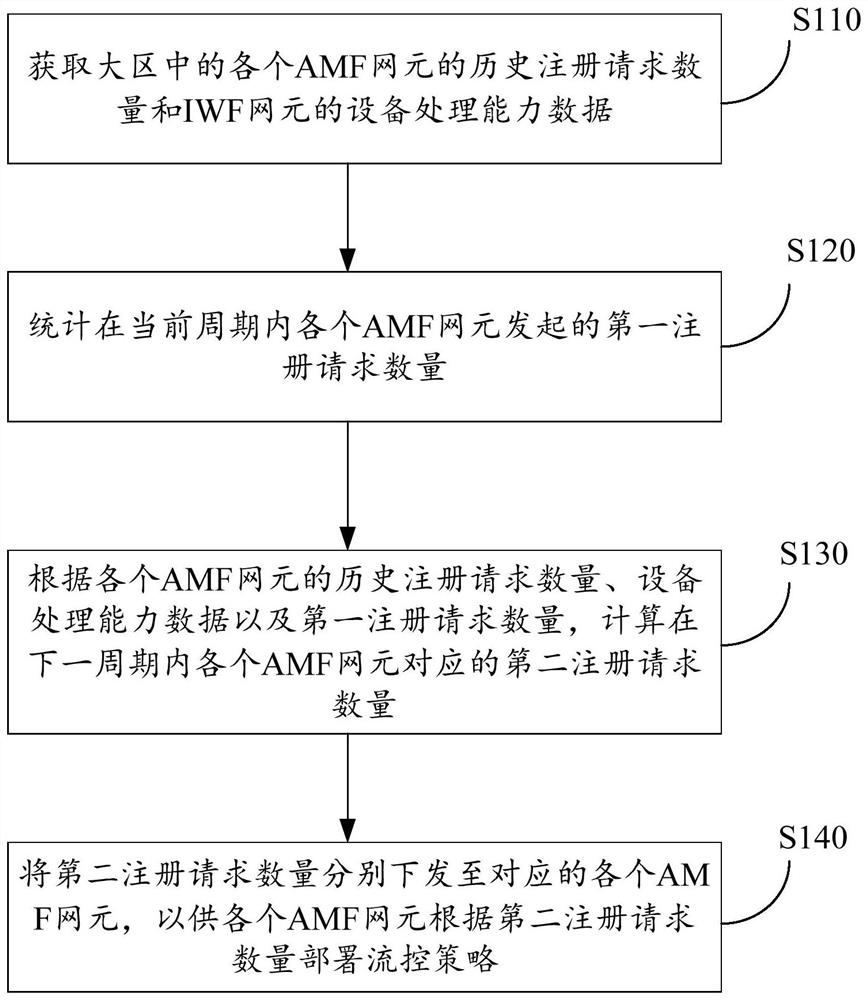
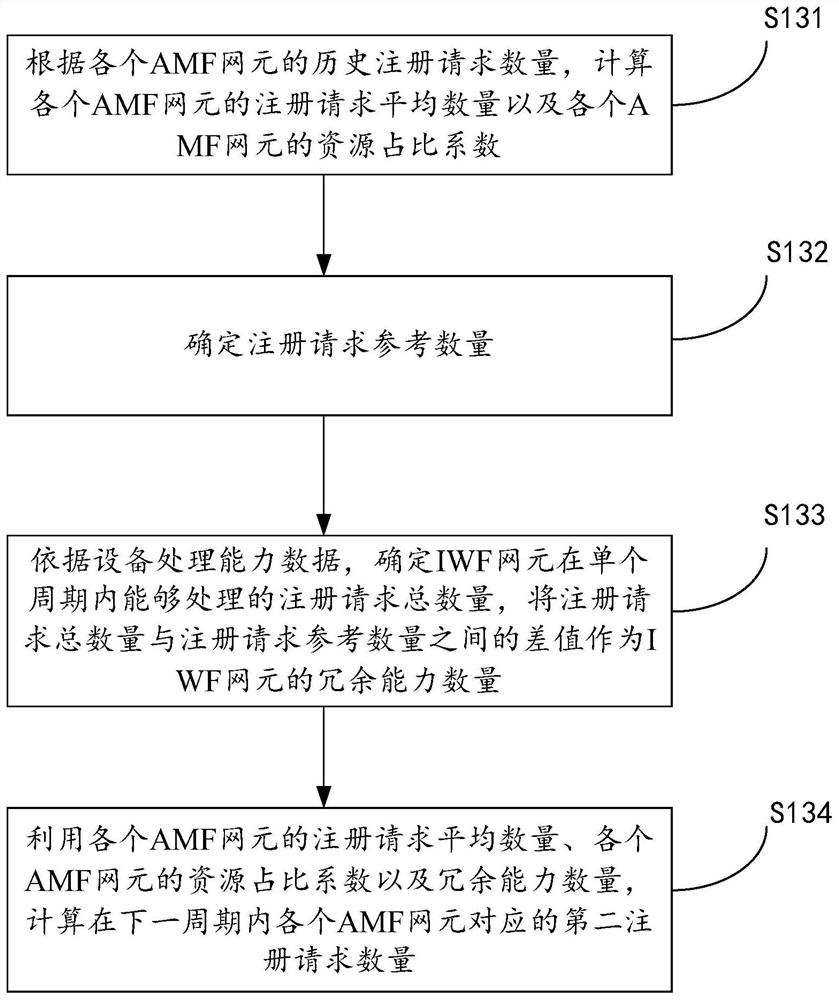
PendingCN113891340AAvoid business interruptionReduce business impactNetwork traffic/resource managementSelf adaptiveNetwork element
The invention discloses a self-adaptive flow control method and device, computing equipment and a storage medium. The method comprises the following steps: acquiring the historical registration request quantity of each AMF network element in a large area and the equipment processing capability data of an IWF network element; counting the number of first registration requests initiated by each AMF network element in the current period; calculating a second registration request number corresponding to each AMF network element in the next period, and issuing the second registration request number to each corresponding AMF network element, so that each AMF network element deploys a flow control strategy according to the second registration request number. According to the method, the IWF network elements are periodically predicted and the number of the second registration requests is updated in real time without manual intervention, so that the processing capacity of each AMF network element in a signaling storm scene is maximized, the IWF network elements are effectively protected, the interruption of services in a large area is avoided, and the influence of the services is reduced to the greatest extent.
Owner:CHINA MOBILE GROUP ANHUI +1
A method for real-time migration of base station processing tasks
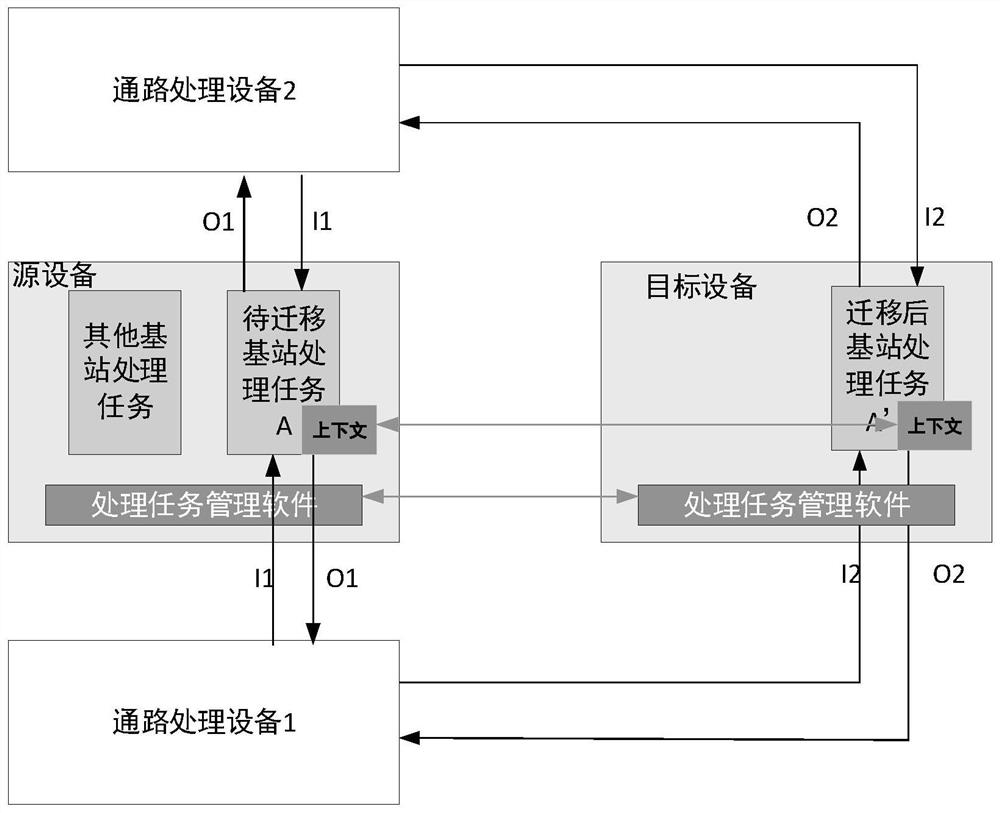
ActiveCN111432438BEfficient readingGuaranteed normal transmissionNetwork traffic/resource managementDevice migrationTerm memory
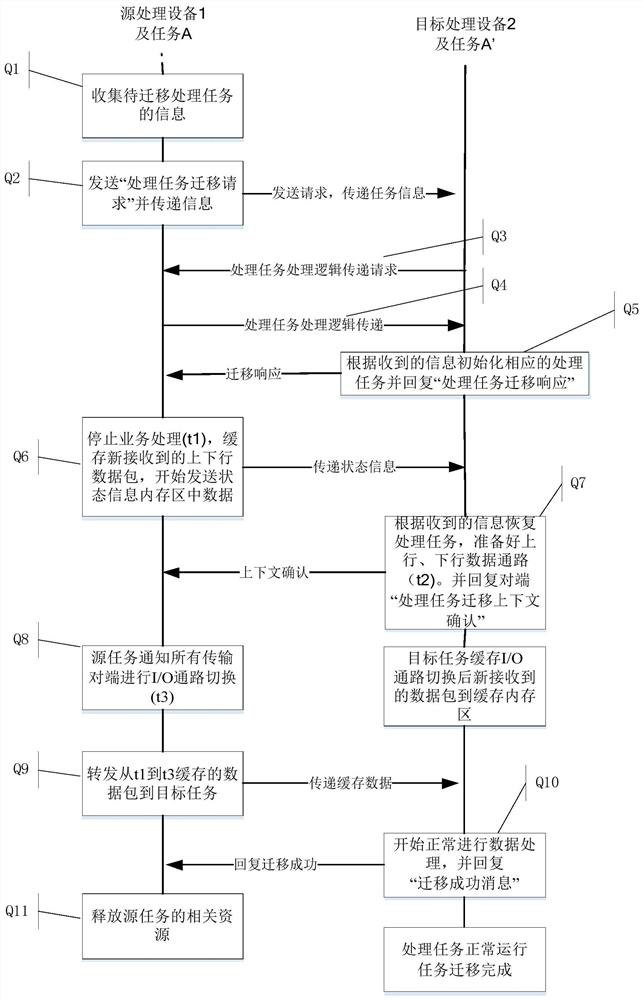
The present invention provides a method for real-time migration of base station processing tasks, which is used to migrate base station processing tasks from a source device to a target device, wherein the base station processing tasks to be migrated on the source device include processing logic and task context, and the task context is stored in The source device is a continuous memory area allocated by the base station processing task, and the method includes: the source device initiates a base station processing task migration request to the target device; the target device responds to the request initiated by the source device, allocates resources required for the base station processing task and starts The target task is executed; the source device migrates the task context of the base station processing task to be migrated to the target device based on the response of the target device; the target device rebuilds the base station processing task based on the received task context. The method of the present invention only needs to transmit the core key context information in the process of task execution, which is the most core and minimum information required for the task to resume its running state, the time required for transmission is short, and the impact on business is small.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Method for processing port failures based on LACP and LACP terminal
ActiveCN102404143BReduce business impactMeet performance requirementsData switching networksInformation transmissionLink aggregation
Owner:HUAWEI TECH CO LTD
System and method for realizing smooth software version upgrade function for sd-wan system
ActiveCN109918109BEasy to upgradeReduce the pressure of upgrade operation and maintenanceVersion controlSoftware deploymentStationSoftware engineering
The invention relates to a system for realizing a smooth software version upgrade function for an SD-WAN system, comprising an orchestrator module; a controller module, which is connected with the orchestrator module, can simultaneously perform software upgrades on equipment modules with multiple versions of software. Service management configuration; device module, connected with the controller module, used for clearing the original configuration during upgrade, and compatible with the service configuration issued by the controller module; interface module, and the orchestrator Modules, controller modules, and device modules are all connected. The present invention also relates to a method for smooth software version upgrade operation for SD-WAN system. By adopting the system and method for realizing the function of smooth software version upgrade for SD-WAN system of the present invention, system services do not need to be rearranged, and smooth upgrade is realized; during the upgrade process, the business impact between devices at each site is minimized; there is upgrade rollback solutions to mitigate the risks that arise during the upgrade process.
Owner:CERTUS NETWORK TECHNANJING
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com