Wireless router and wireless terminal encrypted transmission method and system
A wireless router, encrypted transmission technology, applied in transmission systems, digital transmission systems, key distribution, can solve problems such as easy information leakage, wireless routers cannot encrypt data transmission, etc., to achieve high security and reduce the possibility of being cracked. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
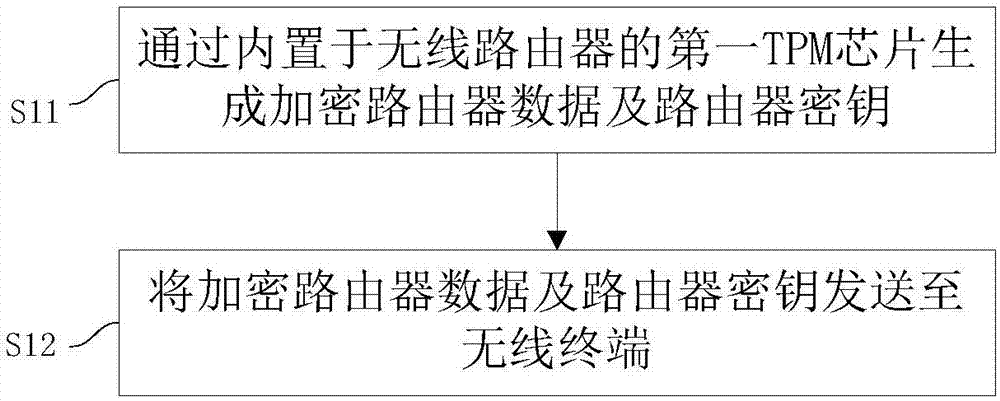
[0052] This embodiment provides a method for wireless router encrypted transmission, such as figure 1 shown, including steps:
[0053] S11: Generate encrypted router data and router key through the first TPM chip built in the wireless router;
[0054] S12: Send the encrypted router data and the router key to the wireless terminal.
[0055] With the development of wireless networks, the information security of wireless routers as devices for wireless and wired conversion is becoming more and more important. The user does not want the information forwarded by the wireless router to be intercepted and the content of the information to be known by others.
[0056] In the traditional data transmission method, encryption software is used to encrypt the data to be transmitted from the wireless terminal to the wireless router or from the wireless router to the wireless terminal, and then store it in the corresponding device. The problem with this method is that the software encrypt...
Embodiment 2
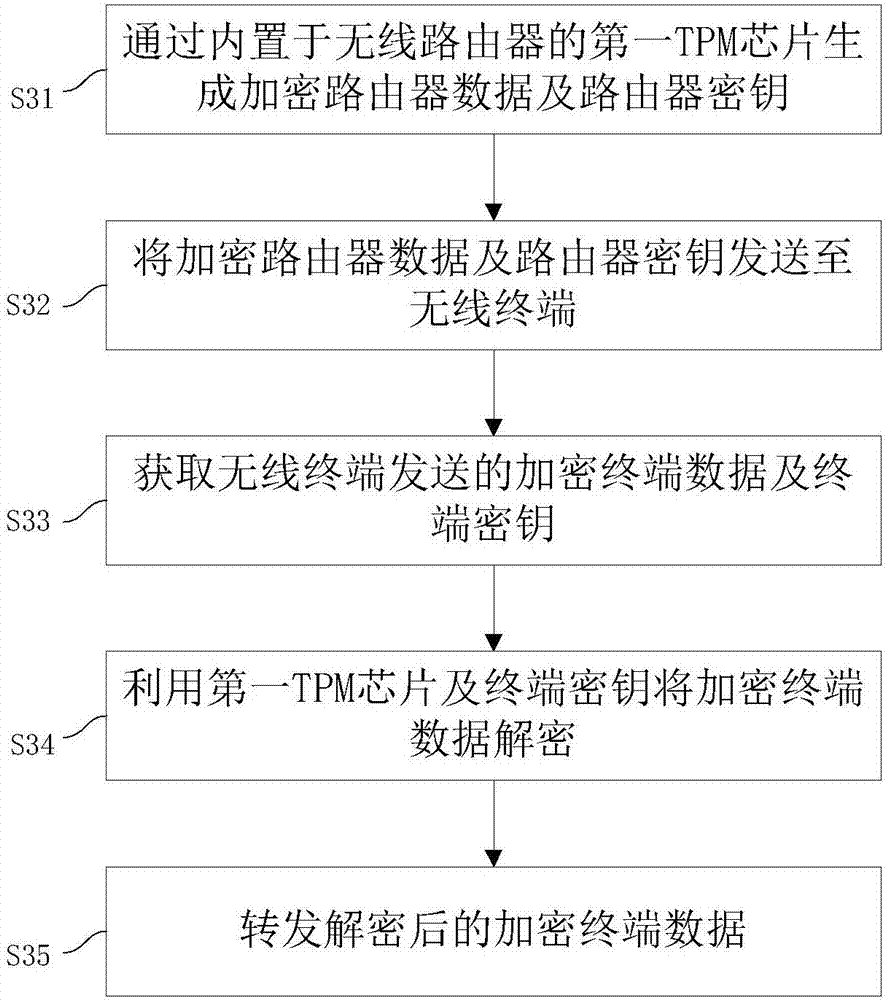
[0083] This embodiment provides a method for wireless router encrypted transmission, such as image 3 shown, including steps:
[0084] S31: Generate encrypted router data and router key through the first TPM chip built in the wireless router;
[0085] S32: Send the encrypted router data and the router key to the wireless terminal;
[0086] S33: Obtain encrypted terminal data and a terminal key sent by the wireless terminal;
[0087] S34: Using the first TPM chip and the terminal key to decrypt the encrypted terminal data;
[0088] S35: Forward the decrypted encrypted terminal data.
[0089] The difference from the first embodiment is that it further includes step S31, step S32 and step S33.
[0090] Specifically, when the wireless router receives the data sent by the wireless terminal, it acquires the terminal key sent by the wireless terminal, and the wireless router stores the key according to the corresponding wireless terminal. Then the wireless terminal encrypts the ...
Embodiment 3
[0104] This embodiment provides a method for wireless terminal encrypted transmission, such as Figure 5 shown, including steps:
[0105] S51: Generate encrypted terminal data and a terminal key through the second TPM chip built in the wireless terminal;
[0106] S52: Send the encrypted terminal data and the terminal key to the wireless router.
[0107] Both the wireless router and the wireless terminal include a TPM chip, the wireless router has a built-in first TPM chip, and the wireless terminal has a built-in second TPM chip.
[0108] In this embodiment, step S51 is to generate encrypted terminal data and a terminal key through the second TPM chip built in the wireless terminal.
[0109] Specifically, when the terminal wants to send data to the wireless router, it uses its built-in second TPM chip to generate a terminal key, and then the wireless terminal encrypts the data with the second TPM chip to generate encrypted terminal data.
[0110] In this embodiment, step S5...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com