Identification-based digital signature method and device
A digital signature and identification technology, used in digital transmission systems, secure communication devices, user identity/authority verification, etc. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0070] It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
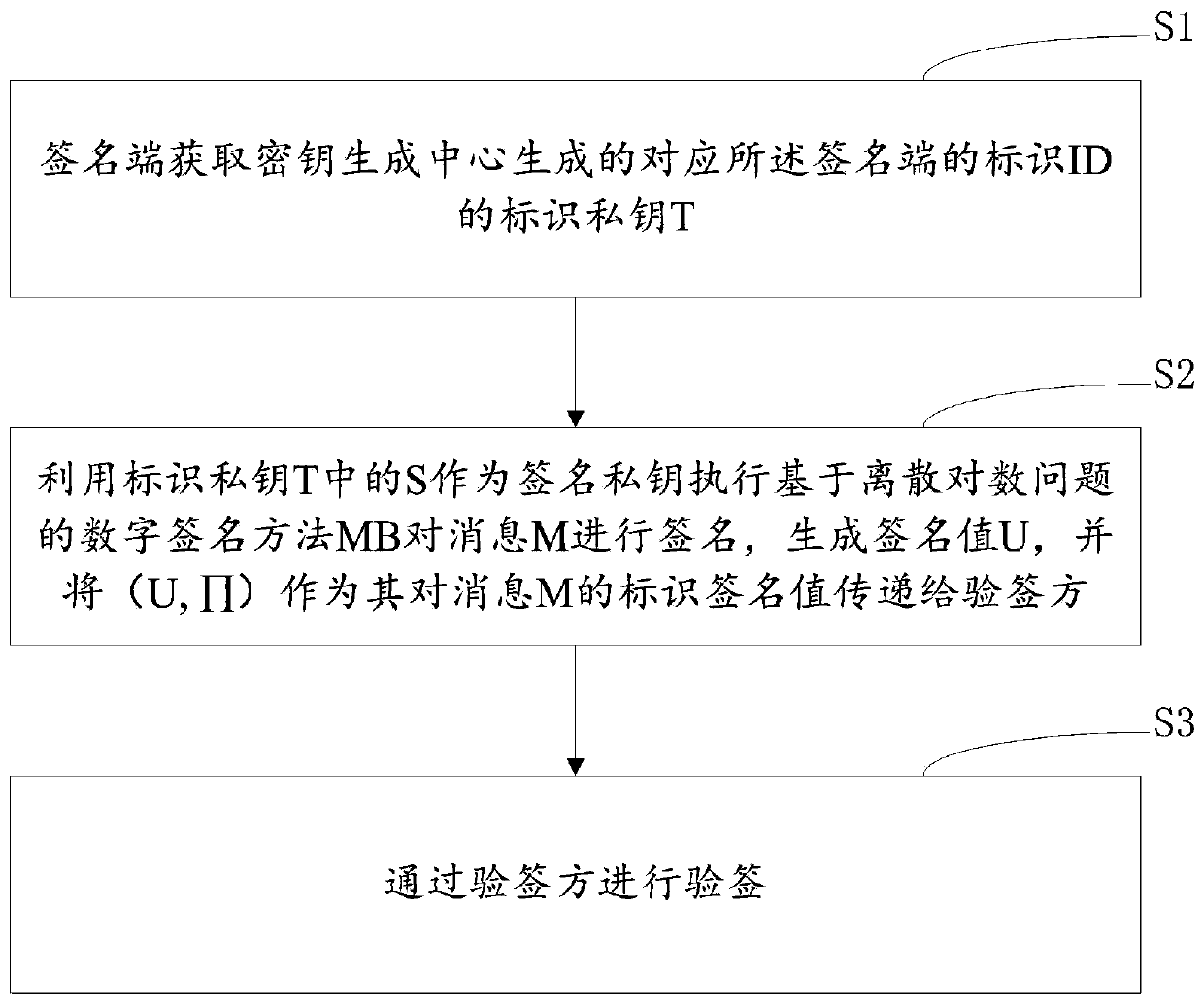
[0071] refer to figure 1 , the embodiment of the present invention firstly provides an identification-based digital signature method, including:
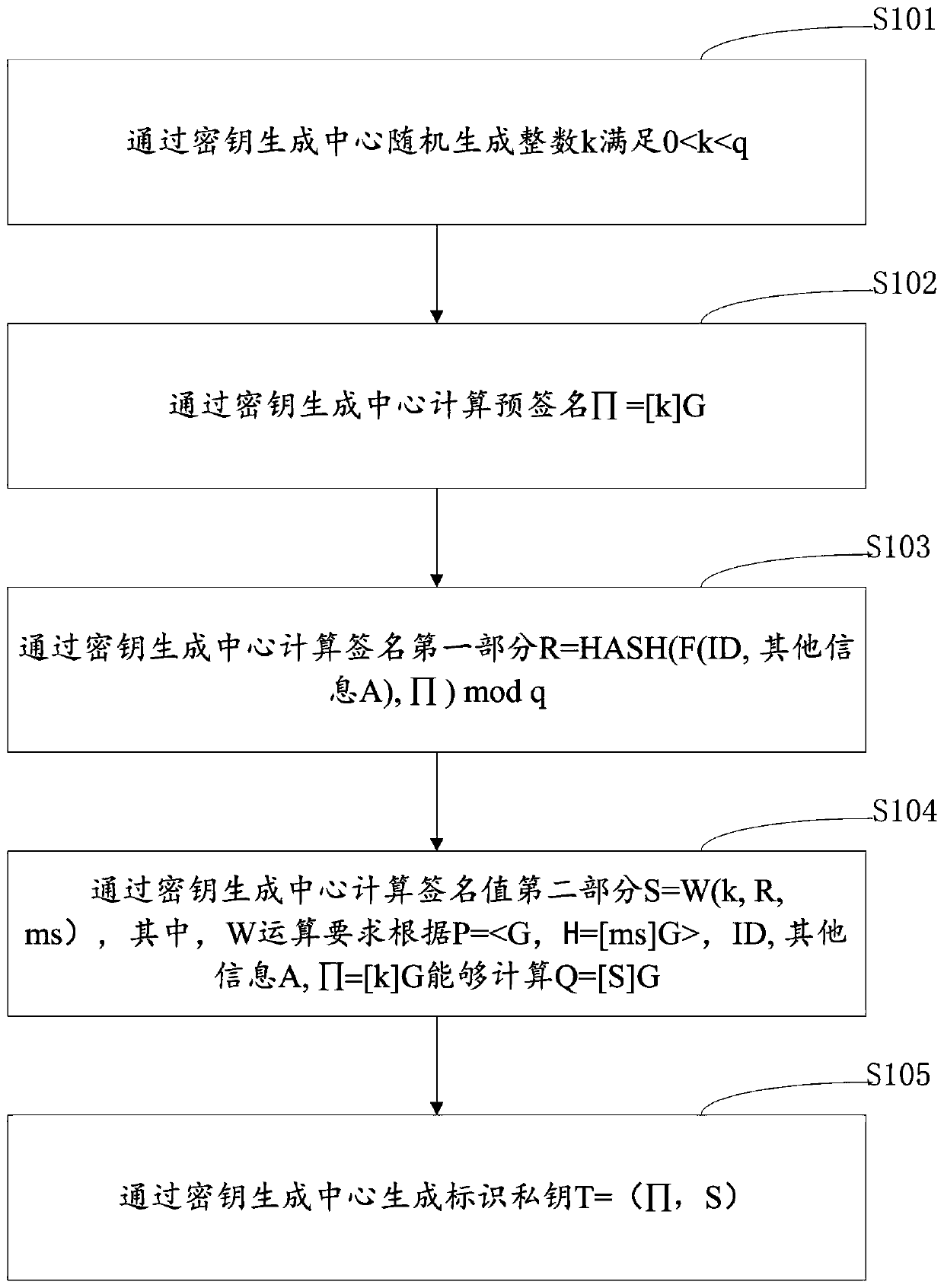
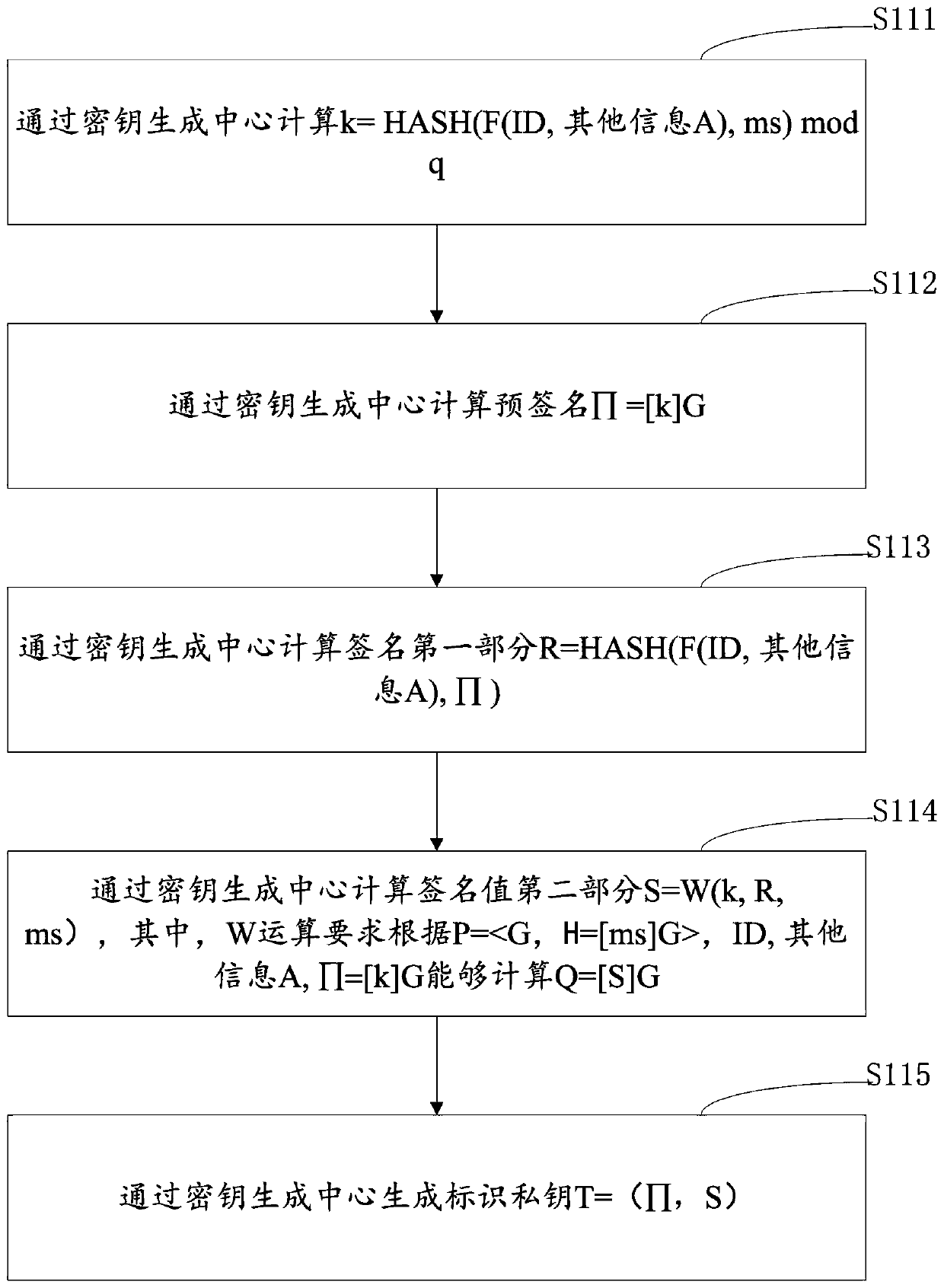
[0072] S1. The signing end obtains the identification private key T corresponding to the identification ID of the signing end generated by the key generation center, wherein the key generation center executes the preset digital signature method MA, and randomly generates a signature public-private key pair as an identification Cryptographic system parameters P and master key ms, the key generation center executes the digital signature method MA to digitally sign the ID, generates a pre-signed Π and a signature value (R, S) containing two parts, and The pre-signed Π and the second part of the signature value S are used as the identification private key T=(Π, S);
[0073] S...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com