Cloud data security storage method and system
A technology for secure storage and cloud data, applied in digital transmission systems, transmission systems, secure communication devices, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] In order to facilitate the expression, first of all, make a unified description of the following technical data:
[0031]
[0032]
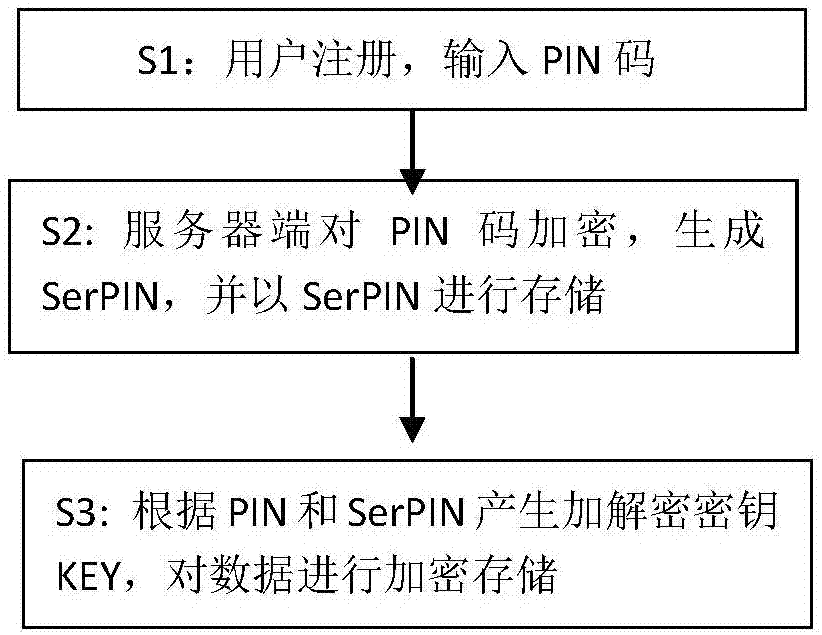
[0033] Such as figure 1 As shown, the key generation phase:
[0034] Step S1: User registration, input PIN code
[0035] When the user registers, set a specific user login password PIN code as the login password. The setting rule of the PIN code can be set according to the required computational complexity.
[0036] Step S2: The server encrypts the PIN code, generates SerPIN, and stores it as SerPIN
[0037] When saving the user information, the server saves the PIN code as a cipher text of the PIN code by means of encryption, and the server uses a hash algorithm to encrypt the PIN code. When saving the user information, only the hash value of the PIN code is recorded:
[0038] SerPIN=HASH(PIN||ID||TIME)
[0039] Among them, ID is the user ID, which is uniquely identifiable, and TIME is the registration time of the user, and the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com