Security and protection monitoring big data processing method and system based on cloud computing
A technology of big data processing and security monitoring, which is applied in the direction of digital transmission system, transmission system, closed-circuit television system, etc., can solve the problems of potential safety hazards, difficulty in resisting DDOS attacks, and insufficient security, so as to improve security, eliminate potential safety hazards, The effect of guaranteeing processing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
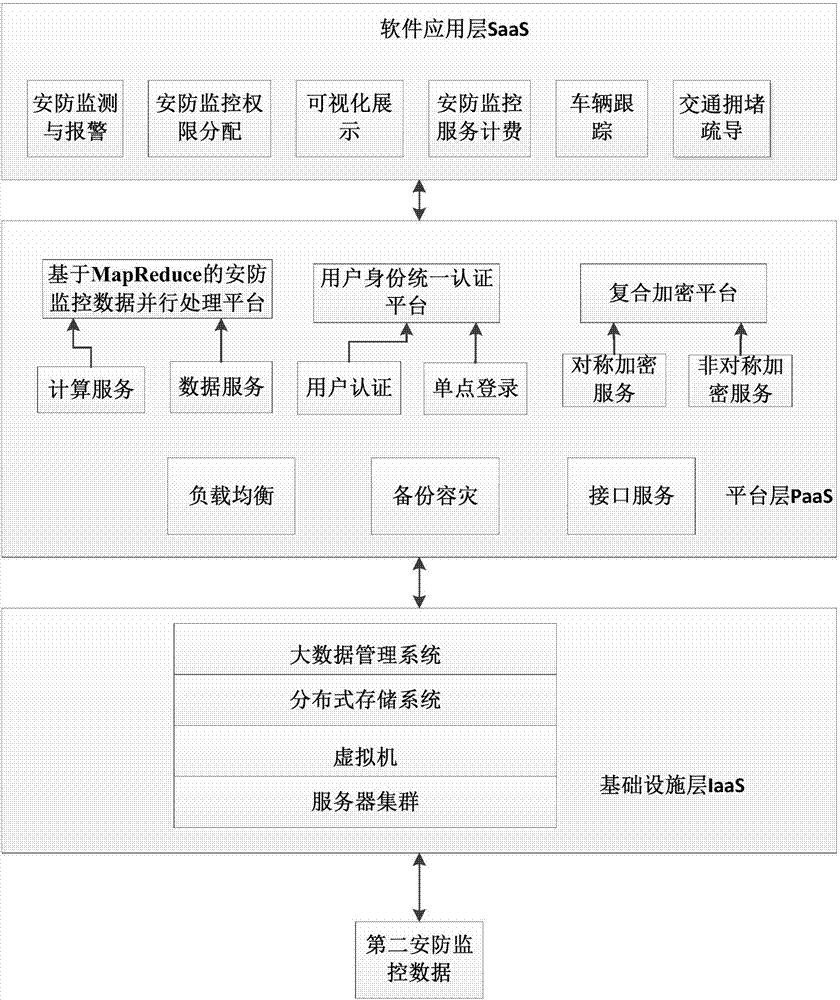
Image
Examples
Embodiment 1
[0083] Aiming at the defect that the existing security monitoring big data processing method cannot meet the requirements of high processing efficiency and safety at the same time, the present invention proposes a new security monitoring big data processing method and system.
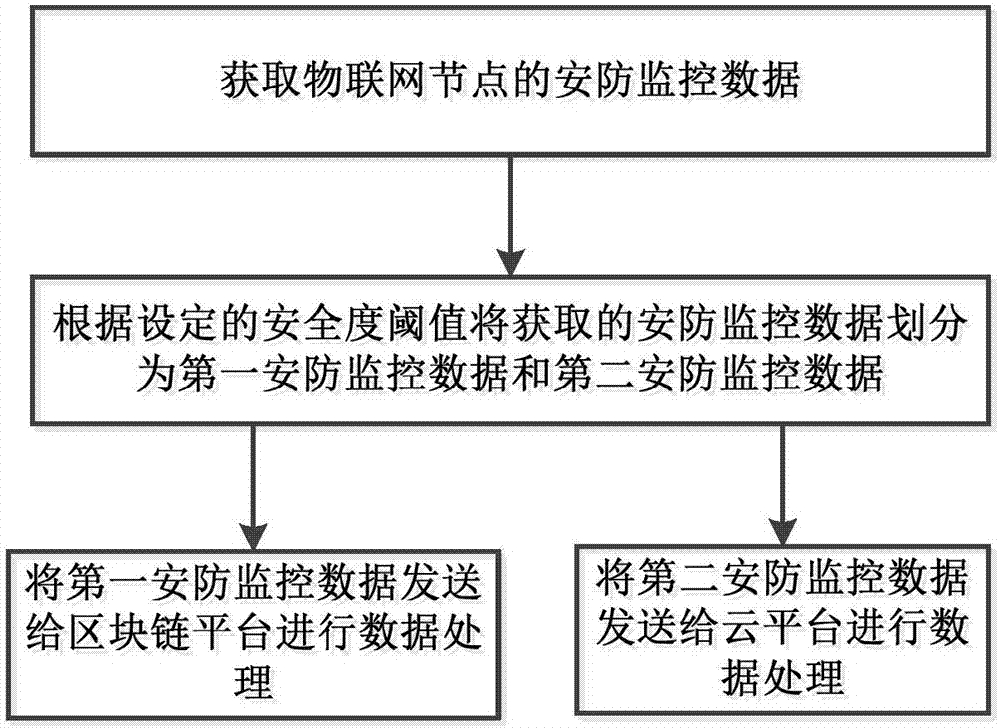
[0084] Such as figure 1 As shown, the security monitoring big data processing method specifically includes the following steps:
[0085] (1) Obtain security monitoring data of IoT nodes.
[0086] Among them, the Internet of Things node of the present invention is provided with cameras, audio collection equipment, positioning devices, etc., in locations such as communities and arterial roads to conveniently obtain data such as video monitoring data, audio monitoring data, and location positioning data. In addition, the security monitoring data also includes the paid monitoring service request data of each IoT node, which is used to request the paid monitoring service from the paid monitoring service provider.
...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com