A security outsourcing method for sequence comparison algorithm based on single server model, user terminal and server
A user terminal, sequence comparison technology, applied in the field of cloud computing security and bioinformatics security, can solve the problem of limited system security, reliability of two cloud service providers, not yet fully balanced sensitive information confidentiality and effective use, overall The architecture lacks effective measures to defend against cloud server collusion, etc., to achieve optimal computing and storage efficiency, minimize network communication overhead, and reasonable space-time overhead.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0050] The present invention will be described in further detail below in conjunction with the accompanying drawings and embodiments.
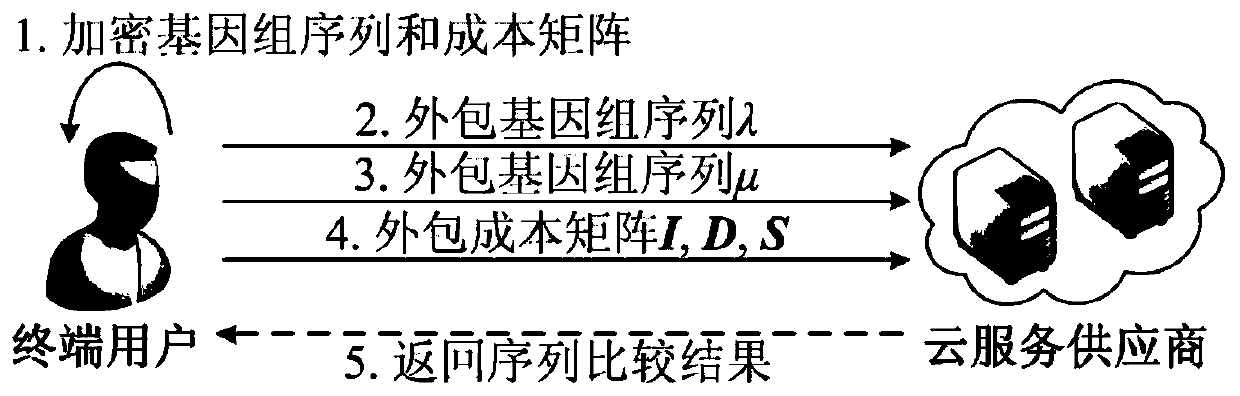
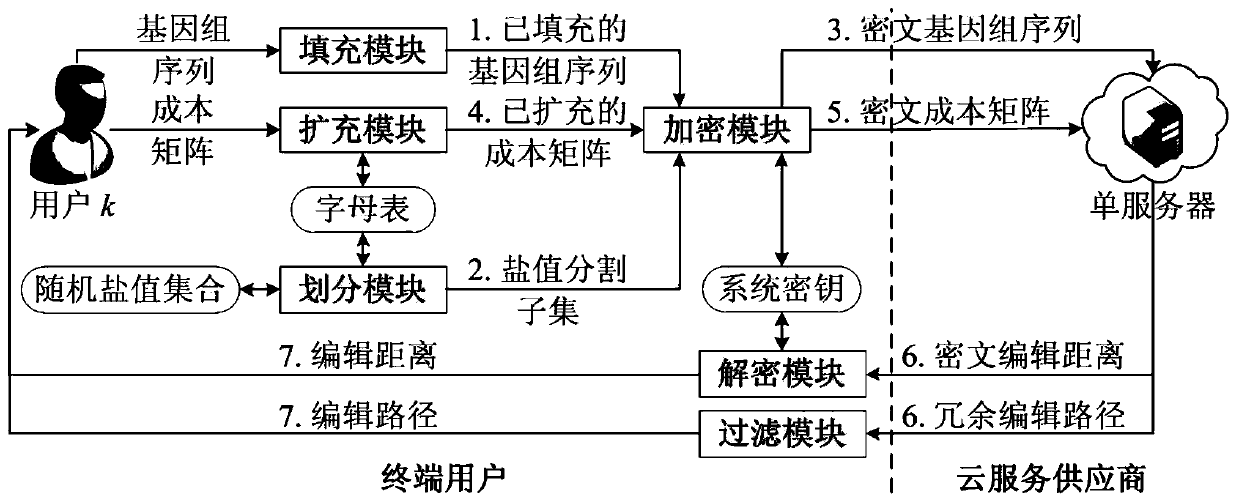
[0051] The invention is based on figure 1 The public cloud outsourcing general system model, proposes a sequence comparison algorithm security outsourcing method using a single cloud server (including the calculation of the Wagner-Fischer edit distance and the planning of the edit path, the Wagner-Fischer edit distance and the edit path are a well-known algorithm, the present invention carries out safe outsourcing to this algorithm). This method acts between both the end user and the cloud service provider. The end user is responsible for encrypting the genome sequence before outsourcing, and the cloud service provider uses a single cloud server to directly execute the sequence comparison algorithm on the ciphertext genome sequence in a non-interactive manner, and the returned ciphertext comparison result is decrypted by the end user. figur...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com