Cloud storage data verification method and system based on elliptic curve cryptography
An elliptic curve encryption and data verification technology, which is applied in the field of cloud storage data verification method and system based on elliptic curve encryption, can solve problems affecting data verification efficiency, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
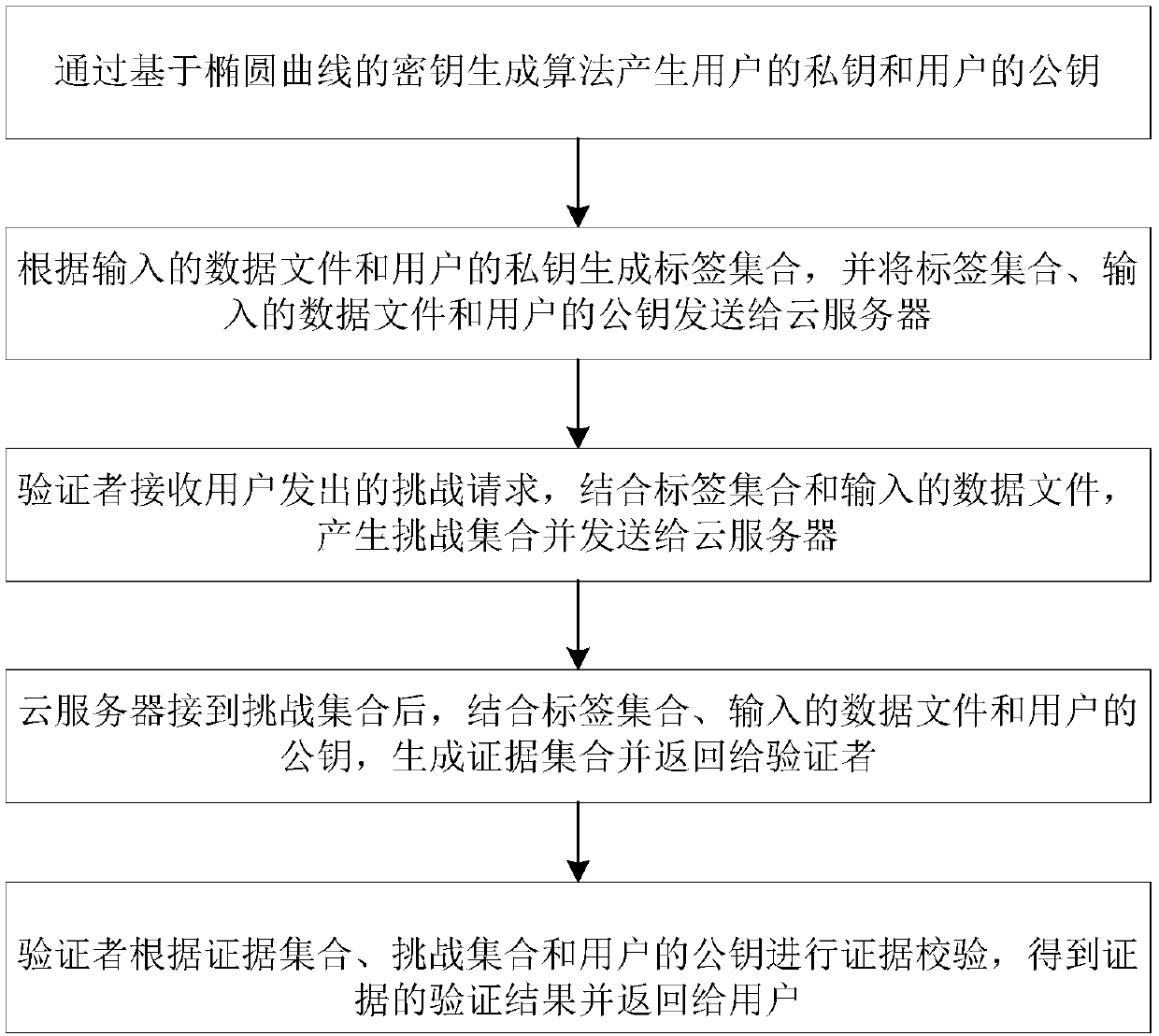
[0051] refer to figure 1 , a cloud storage data verification method based on elliptic curve encryption, comprising the following steps:
[0052] Generate the user's private key and user's public key through the key generation algorithm based on elliptic curve;
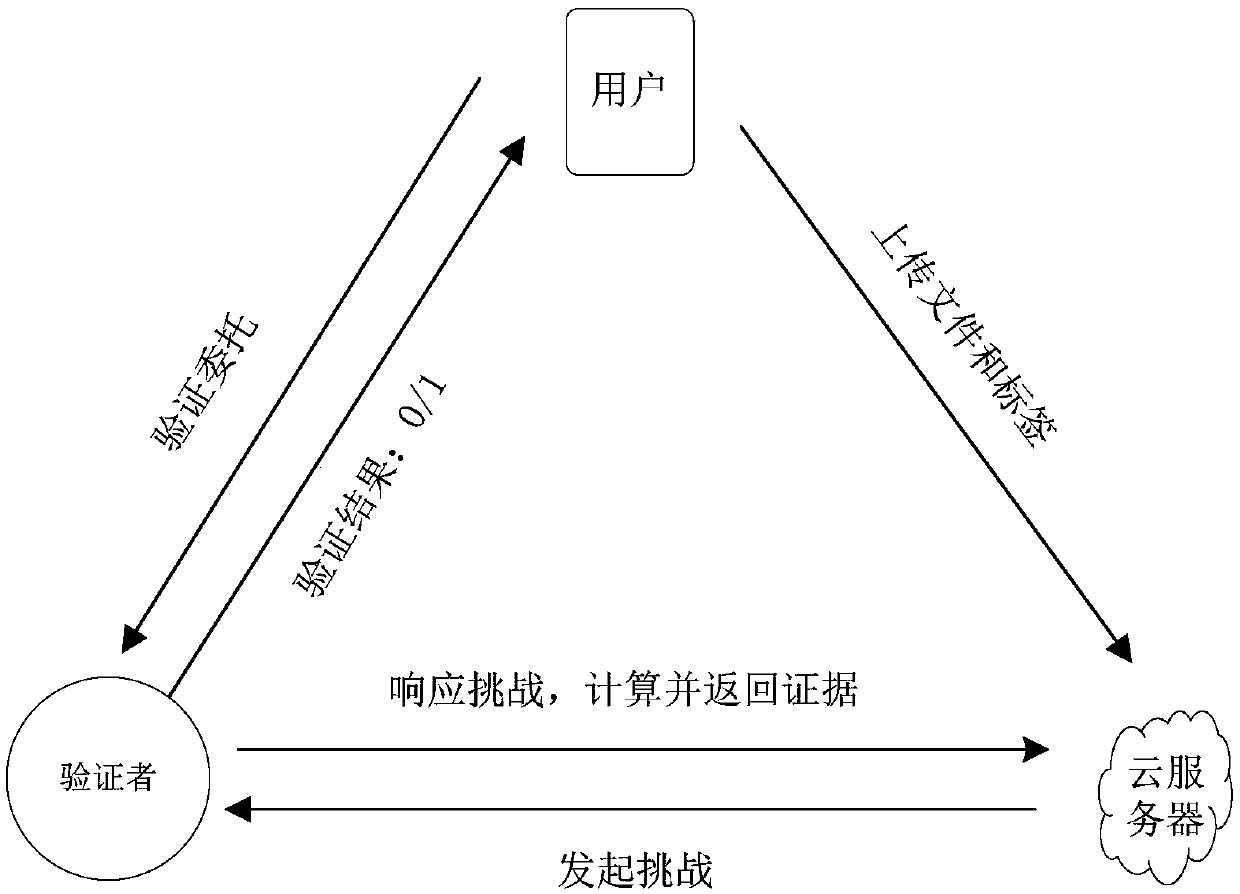
[0053] Generate a label set according to the input data file and the user's private key, and send the label set, the input data file and the user's public key to the cloud server;
[0054] The verifier receives the challenge request sent by the user, combines the tag set and the input data file, generates a challenge set and sends it to the cloud server;
[0055] After receiving the challenge set, the cloud server combines the label set, the input data file and the user's public key to generate a proof set and return it to the verifier;
[0056] The verifier performs evidence verification according to the evidence set, challenge set and the user's public key, obtains the verification result of the evidence and return...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com