Single-trigger hardware trojan horse detection method based on gate-level structure characteristics
A hardware Trojan detection and structural feature technology, applied in the protection of internal/peripheral computer components, etc., can solve the problems of limiting the generality and feasibility of the method, the high complexity of the score accumulation algorithm, and the high misjudgment rate of Trojan horse detection, and achieve improved scores Calculation method, reduction of detection time, and effect of reduction of detection complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0037] The present invention will be further described below in conjunction with the accompanying drawings.
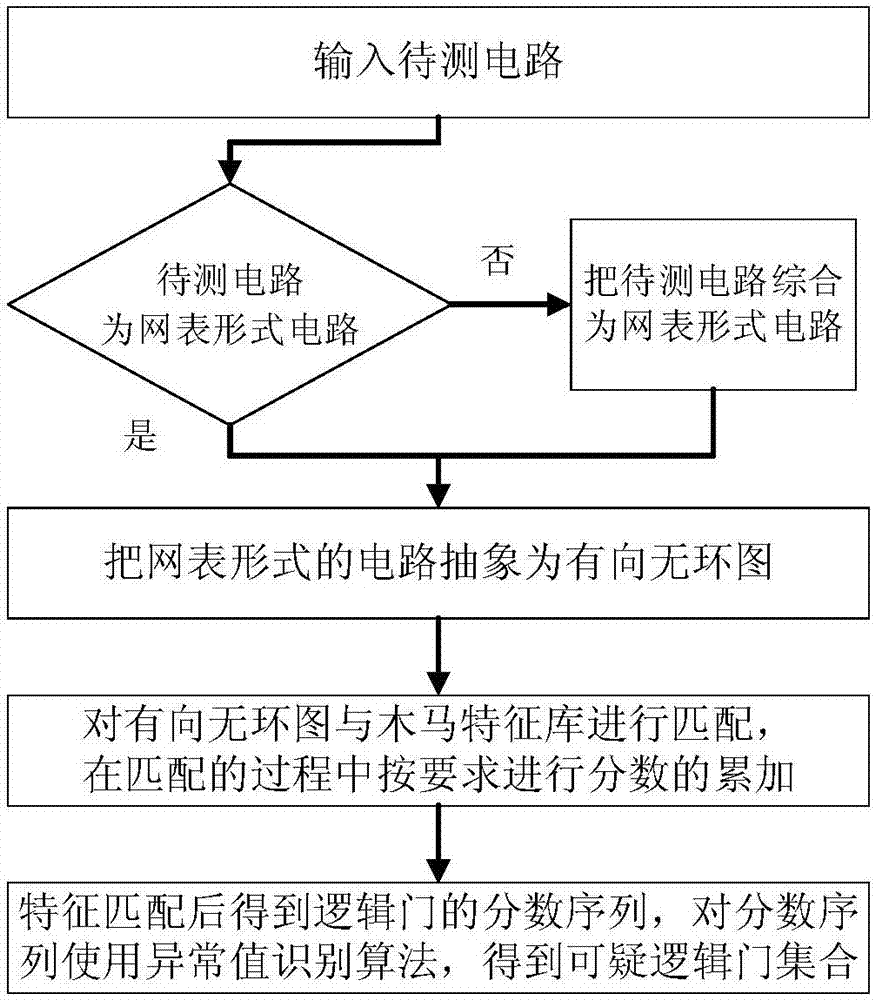
[0038] The detection steps of the present invention for the hardware Trojan horse circuit in the circuit to be tested are as attached figure 1 shown.
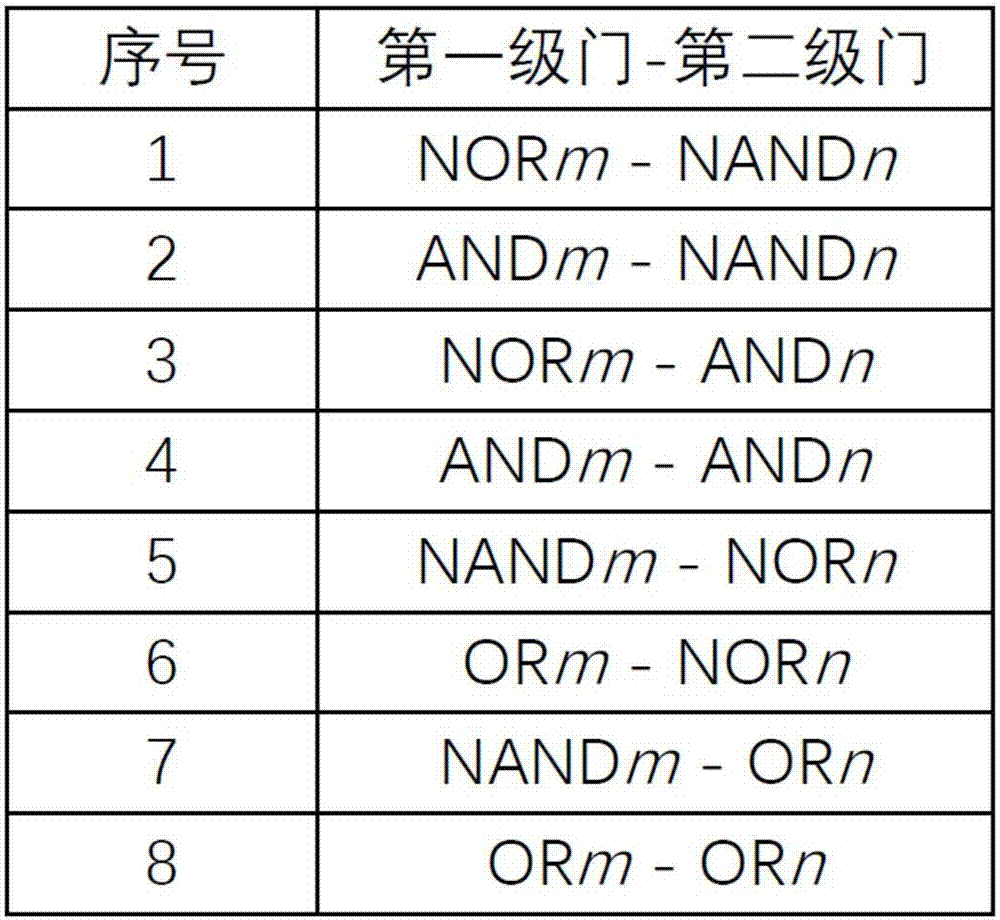
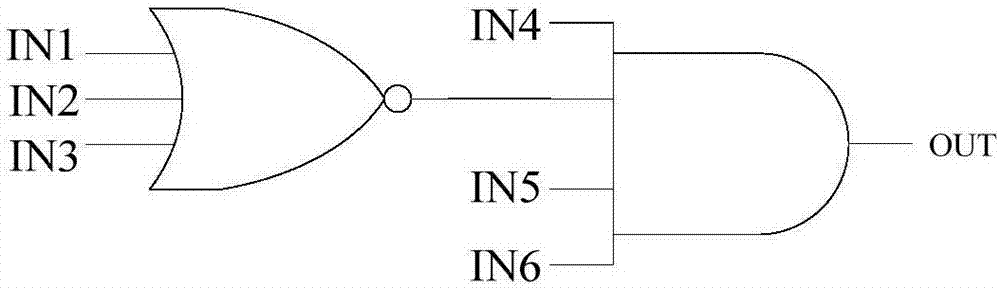
[0039] Specifically, input the circuit to be tested; judge whether the circuit to be tested is a netlist form circuit, if it is a netlist form circuit, proceed to the next step, if not, use a synthesis tool to synthesize the test circuit into a netlist form circuit , followed by the next step; the circuit in the form of a netlist is abstracted into a directed acyclic graph, wherein in the directed acyclic graph, the nodes represent the logic gates in the netlist circuit, and the edges represent the connections between the logic gates in the netlist circuit Connect; match the directed acyclic graph with the Trojan horse feature library, and accumulate the scores as required during the matching process; get the score seq...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com