A method for dns protection and data leakage prevention based on metadata analysis
A technology of data leakage and metadata, applied in the field of network security analysis, can solve the problem of insufficient security analysis, and achieve the effect of realizing evidence preservation, improving accuracy and reducing false positive rate.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
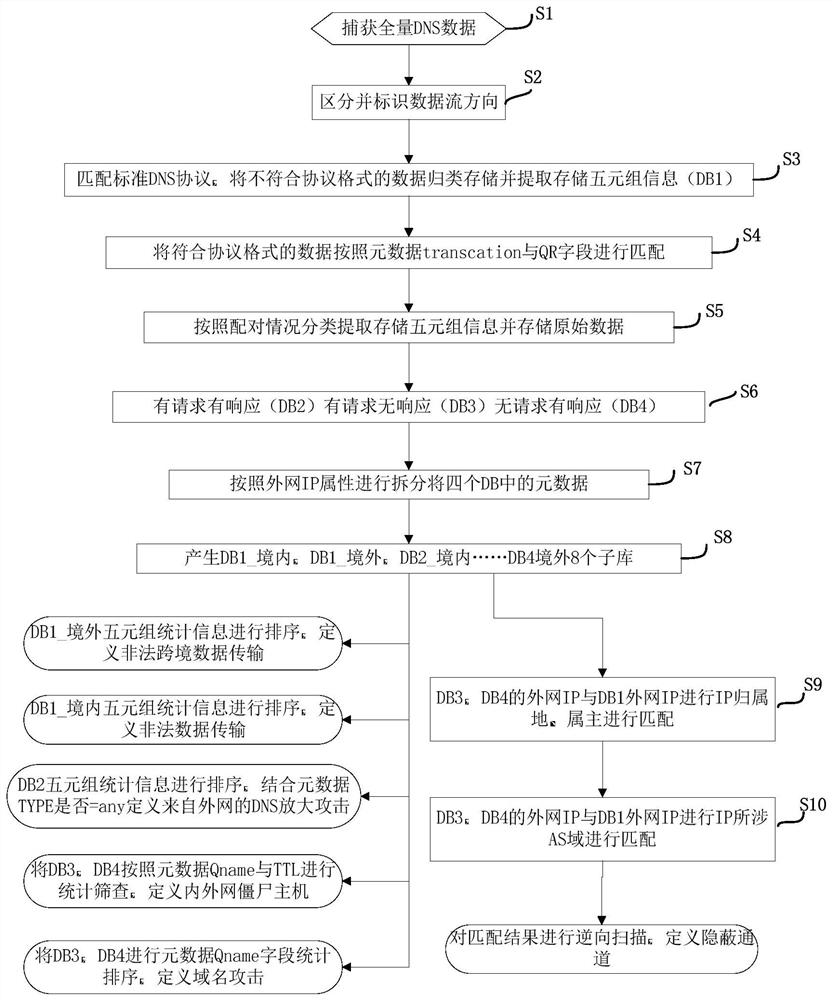
[0032] The method for DNS protection and data leakage prevention based on metadata analysis of the present invention will be described in detail below with reference to the accompanying drawings.
[0033] Such as figure 1 As shown, it shows a preferred implementation of the method for DNS protection and data leakage prevention based on metadata analysis in the present invention.
[0034] A method for DNS protection and data leakage prevention based on metadata analysis, comprising the following steps:
[0035] S1: capture the full amount of DNS data;
[0036] S2: distinguishing the full amount of DNS data captured in step S1 and identifying the data flow direction;
[0037] The way to distinguish the full amount of DNS data is to distinguish and judge by customizing labels or mac addresses in data packets. If you use the data capture product of Datian Information, you can customize the label for the data while capturing; if you have an existing product at the user site, you...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com