Malicious code detection and recognition method and device based on software genes
A malicious code detection and malicious code technology, which is applied in the field of malicious code detection and identification based on software genes, can solve the problems that the detection accuracy cannot be effectively guaranteed, and achieve good representation, low false alarm rate, and good detection accuracy Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
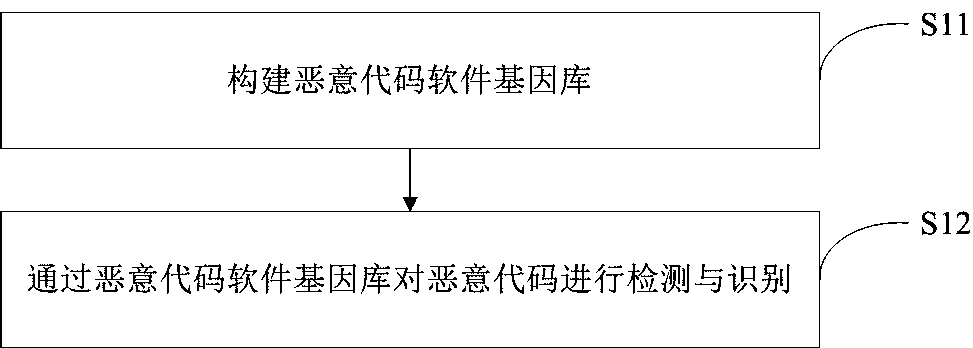
[0060] Such as figure 1 As shown, a kind of malicious code detection and identification method based on software gene of the present invention comprises the following steps:
[0061] Step S11: constructing a malicious code software gene library.
[0062] Step S12: Detect and identify the malicious code through the malicious code software gene library.
Embodiment 2
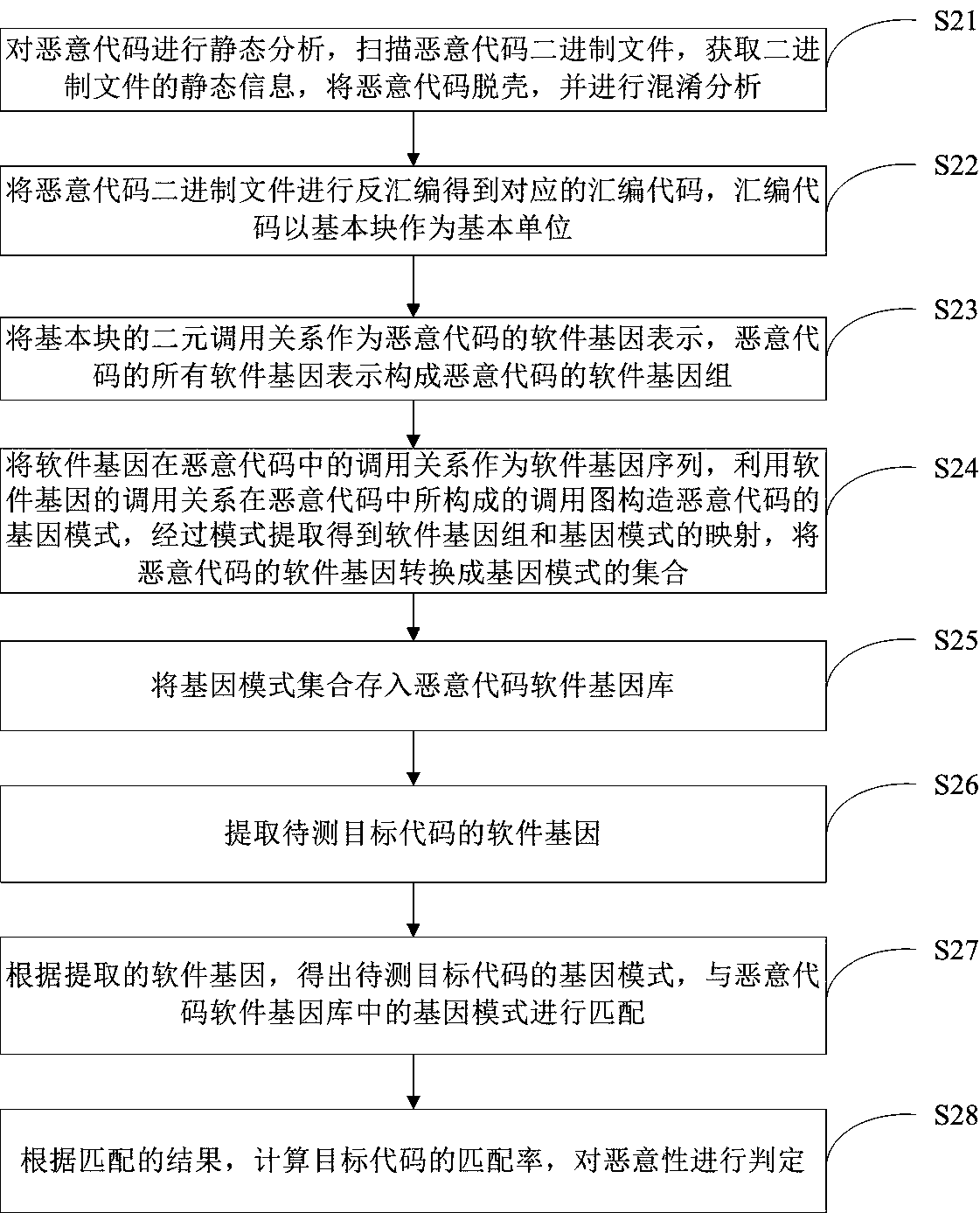
[0064] Such as figure 2 As shown, another malicious code detection and identification method based on software gene of the present invention comprises the following steps:
[0065] Step S21: performing static analysis on the malicious code, scanning the binary file of the malicious code, obtaining static information of the binary file, unpacking the target code, and performing obfuscation analysis.
[0066] Step S22: Disassemble the malicious code binary file to obtain the corresponding assembly code, and the assembly code takes a basic block as a basic unit.
[0067] Step S23: The binary calling relationship of the basic block is used as the software gene representation of the malicious code, and all the software gene representations of the malicious code constitute the software genome of the malicious code, including:
[0068] Step S231: scan the assembly code of the target code, and divide the assembly code according to the basic blocks;
[0069] Step S232: merging the s...
Embodiment 3
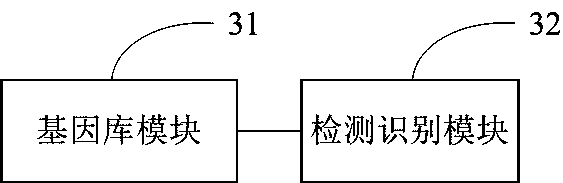
[0091] Such as image 3 As shown, a kind of malicious code detection and identification device based on software gene of the present invention comprises:
[0092] The gene library module 31 is used to construct a malicious code software gene library.
[0093] The detection and identification module 32 is configured to detect and identify malicious codes through the malicious code software gene library.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com